🚀 CloudSEK has raised $19M Series B1 Round – Powering the Future of Predictive Cybersecurity
Read more
India’s BFSI sector faces more than just cyber threats it faces regulatory risk from within. Before you think you’re compliant, let’s test your blind spots.
What you just answered aren’t just theoretical risks, they’re the top five blind spots that have repeatedly led to RBI penalties, warnings, and audit escalations.
These oversights continue to trip up even mature financial institutions, turning avoidable gaps into compliance failures.
India’s BFSI sector is witnessing rapid digital transformation, expanding its reach and services. However, this growth comes with escalating cybersecurity risks, making financial institutions prime targets for threat actors. From phishing attacks, data leaks, and credential theft to ransomware, third-party breaches, and brand impersonation, BFSI organizations face a wide spectrum of threats that can compromise customer trust and regulatory standing. In the face of relentless cyber threats and a complex web of RBI directives, India's BFSI sector requires a solution that addresses both risk and regulation simultaneously.
CloudSEK's unified platform is engineered to transform this challenge, moving organizations from a reactive compliance stance to a proactive, intelligence-driven security posture. By integrating continuous attack surface monitoring, automated third-party risk management, ensuring quantification of cyber risks, and predictive threat intelligence from the dark web, we provide a single, holistic view of your entire digital ecosystem. This not only simplifies audit preparations by aligning with RBI’s core principles but also empowers CISOs to communicate risk in clear, financial terms to the board.
Ultimately, CloudSEK ensures regulatory mandates are met not as a separate task, but as the natural outcome of a truly resilient and confident security program. This blog explores RBI’s key cybersecurity mandates and how CloudSEK empowers BFSI entities to navigate them confidently.
Phishing & Brand Impersonation: Attackers create fake websites, mobile apps, or social media profiles to impersonate trusted brands and deceive customers, leading to fraud, reputational damage, and user trust erosion.
Customer Data Leaks (PII): Sensitive personal information such as identity numbers, contact details, or financial records may be unintentionally exposed or exfiltrated, posing serious privacy and security risks.
Third-Party or Vendor Breaches:Weaknesses or breaches within technology vendors, service providers, or outsourced partners can lead to indirect but impactful compromise of systems and data.
Ransomware Attacks: Malicious encryption of systems and demand for ransom payments can disrupt business operations, compromise data, and cause prolonged downtime if not swiftly mitigated.
Vulnerabilities (APIs, Outdated Software, Misconfigurations): Exploitable system vulnerabilities such as insecure APIs, outdated software, and improperly configured cloud environments can serve as critical entry points for cyber attackers.
Weak Identity & Access Management (IAM): Poor control over user privileges, unmonitored access, and leaked or weak credentials increase the likelihood of unauthorized system access and internal abuse.
Delayed Breach Reporting: Delays in detecting and reporting security incidents can worsen the impact, extend the threat window, and slow down recovery. Regulatory timelines mandate reporting within 6 hours for RBI-regulated financial entities and within 72 hours for all organizations under CERT-In jurisdiction.
Unsecured Mobile Applications:Banking apps lacking secure coding practices, proper encryption, or anti-tamper protections expose users to fraud, data theft, and unauthorized access, undermining the security of digital interfaces and customer information.
Let us understand the frameworks better using some use-cases


In response to growing cyber threats in India’s financial sector, the RBI has developed a comprehensive cybersecurity framework. Through guidelines, circulars, and master directions, it aims to build a cyber-resilient BFSI ecosystem with governance, risk management, and incident response integrated into core operations.

- Comprehensive Asset Management: Organizations must meticulously identify and manage all digital assets (domains, APIs, cloud, apps) because effective protection is impossible for unaccounted assets.
- Proactive Threat & Vulnerability Management: Continuously scan for and promptly fix system vulnerabilities, misconfigurations, and data leaks to prevent exploitation by malicious actors.
- Robust Incident Response: Establish a clear plan to effectively detect, contain, and recover from security incidents, ensuring minimal disruption and safeguarding customer trust.
- Third-Party Risk Management: Extend comprehensive security oversight to all vendors and service providers, recognizing their intrinsic link to the organization's overall security posture.
- Protection of Customer Data: Implement stringent controls to prevent unauthorized access or leakage of Personally Identifiable Information (PII) and sensitive financial data.
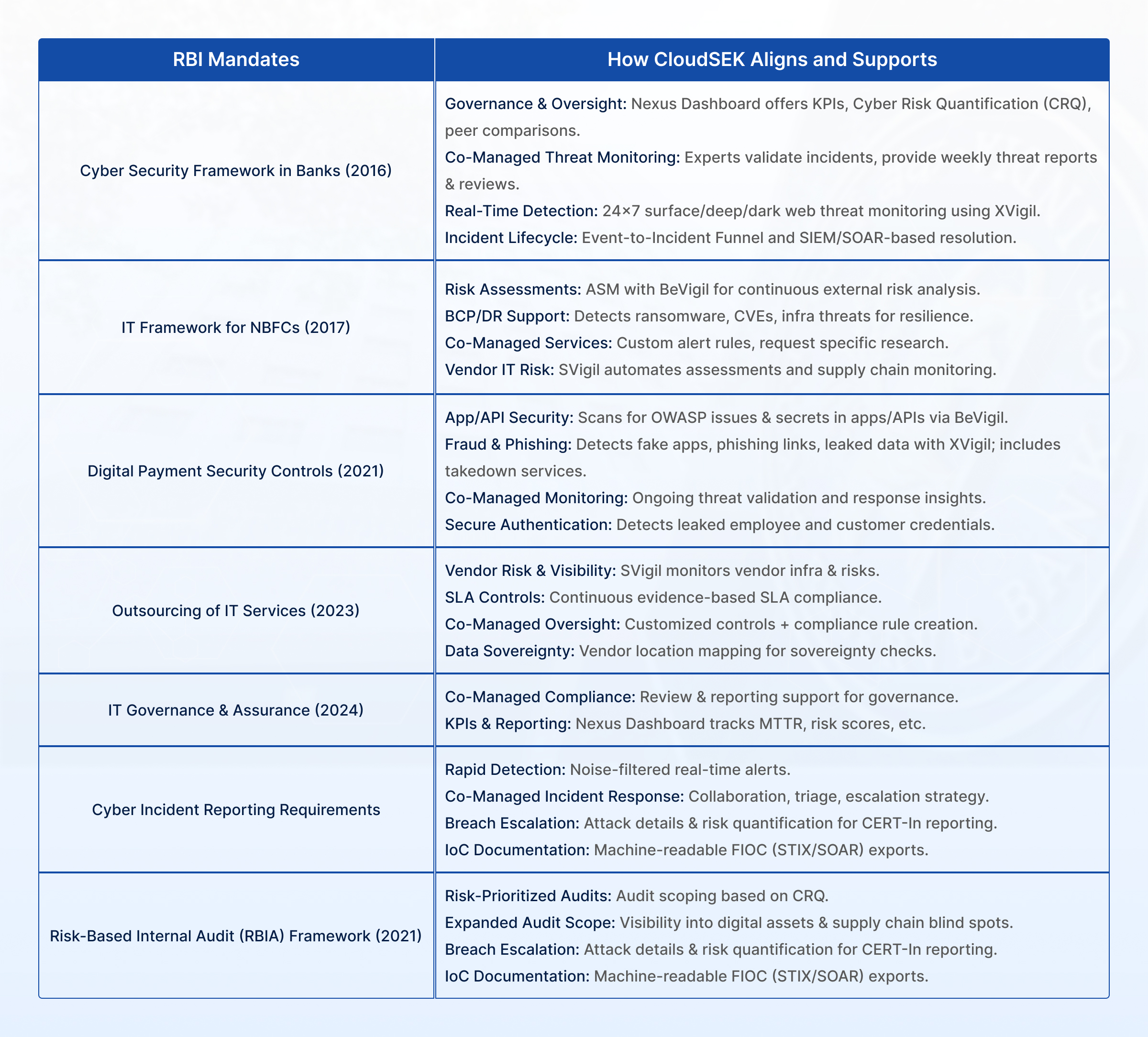
As regulatory expectations grow more complex and threats more sophisticated, achieving RBI compliance requires more than ad-hoc fixes; it demands a continuous, structured, and risk-aware approach. By addressing blind spots before they become liabilities, BFSI institutions can build both resilience and regulatory confidence.
