🚀 CloudSEK has raised $19M Series B1 Round – Powering the Future of Predictive Cybersecurity
Read more




Raksha Bandhan is a time for siblings to celebrate and exchange gifts, but cybercriminals often exploit the occasion. Fraudsters know people shop online and share joyful messages, so they roll out Rakhi-themed scams – from bogus gift deals to fake delivery notices. Cloudsek sees a surge in online shopping scams on Raksha Bandhan: “Fake websites, unbelievably low prices, and attractive offers” are tactics crooks use to lure victims. Popular ploys include fraudulent SMS or email “gift offers” and fake e‑commerce sites claiming huge Rakhi discounts.
Phishing messages (emails/SMS/WhatsApp): Scammers send messages claiming “Your Rakhi gift is on the way” or advertise amazing Rakhi sale coupons. These usually contain malicious links or forms. For example, fraudsters have posed as courier companies (like India Post) saying a Rakhi gift delivery was delayed due to an incomplete address, asking victims to click a link and pay a small “re-delivery” fee. Clicking or responding can lead to malware on your phone or theft of payment data. Always treat unsolicited Rakhi offers or delivery notices with suspicion.
Below is an example of a Raksha Bandhan-themed suspicious WhatsApp message, which may contain a malicious link capable of delivering malware to your device or stealing your payment information.
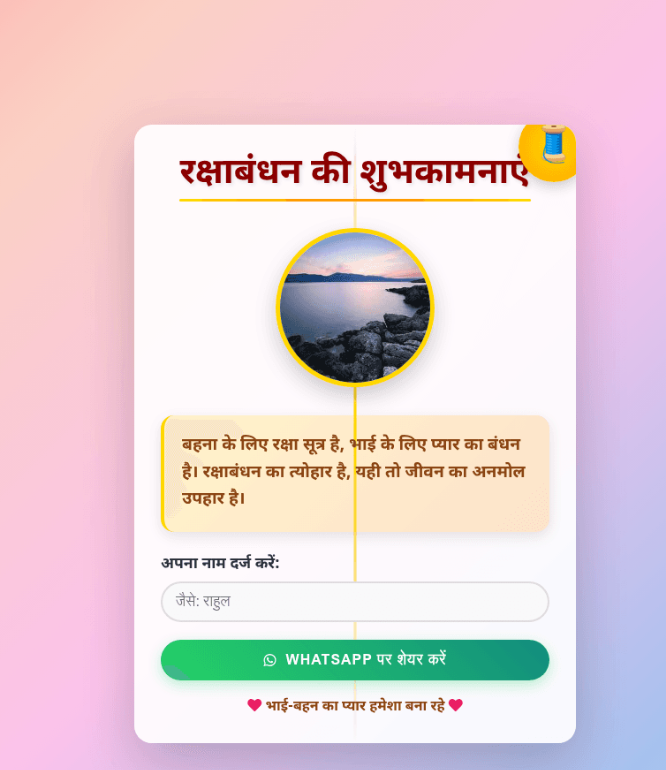
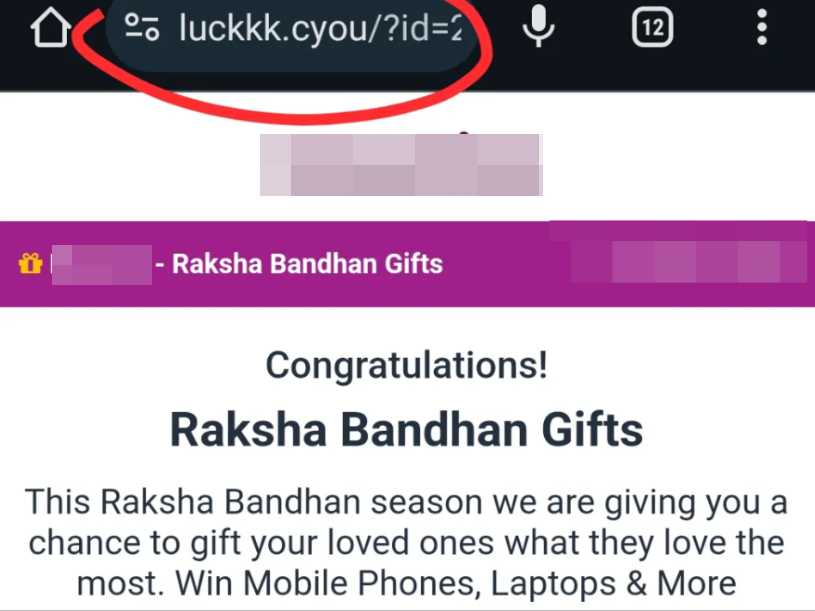
In another method, a new phishing technique is gaining traction by impersonating Raksha Bandhan Gifts from the Ecom platform, which leverages URLs containing legitimate-looking domain names followed by the "@" symbol—for example, [email protected]. At first glance, such URLs may appear to be associated with well-known e-commerce site. However, in reality, the actual destination is a phishing page created on .cyou, not the legitimate domain.

When a user clicks on a link like this, most browsers ignore everything before the "@" symbol (e.g.,ecom.com@) and instead navigate directly to the domain that follows it (e.g.,a malicious webpage created on.cyou). This deceptive use of the "@" symbol can easily mislead users into thinking they are visiting a trusted site, when in fact, they are being redirected to a potentially malicious website.
Fake shopping social media & websites: Criminals set up fake online stores selling rakhis, sweets or gifts at too-good-to-be-true prices. These clone sites often mimic real brands but have spelling errors or strange URLs. When you enter payment or card details, the money goes straight to scammers and your info is stolen. Once victims “enter their payment details… the entire payment redirects to the scammers along with the banking information”.
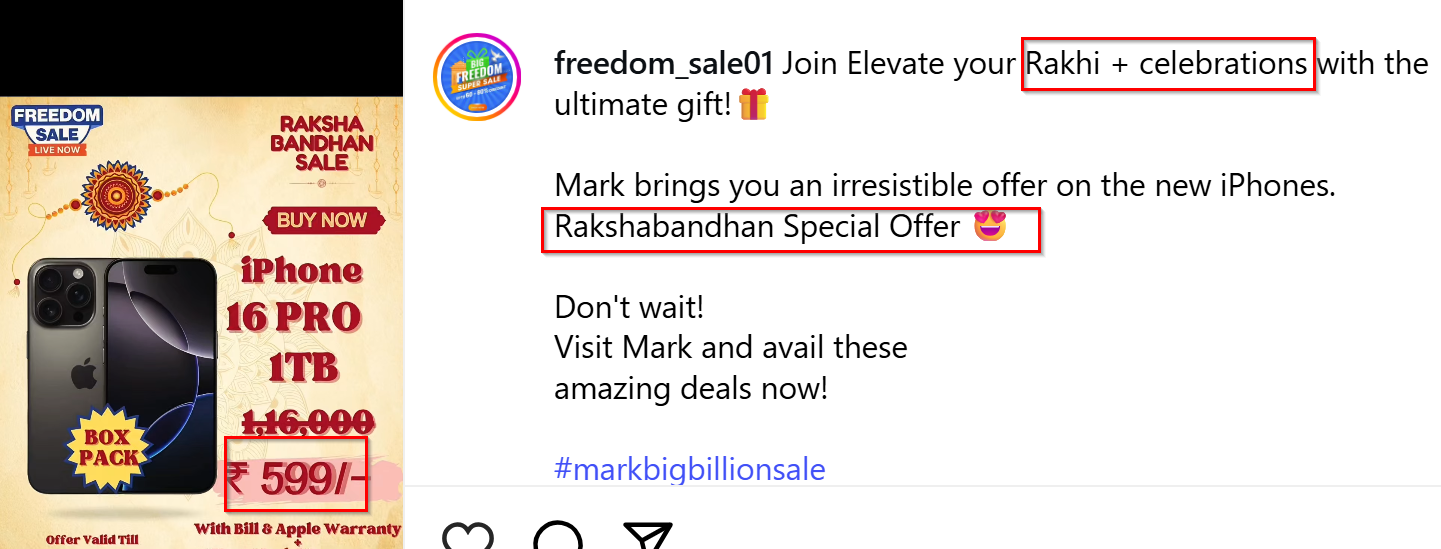
A fraudulent Instagram page is promoting the sale of the iPhone 16 Pro for just ₹599 under the guise of a Raksha Bandhan special offer.
Another sponsored ad uses a Raksha Bandhan sale-themed template to lure victims and redirect them to a scammer-controlled website.
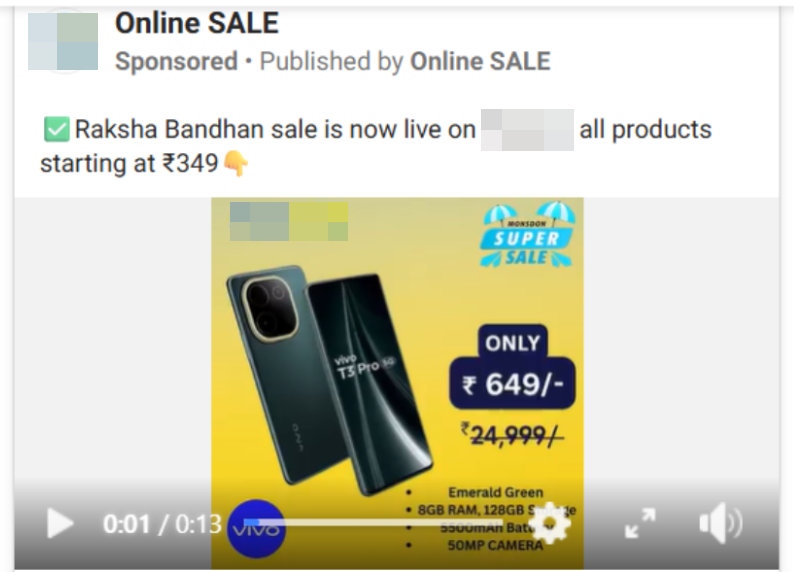
The ad redirects users to a fraudulent website — https://rakshabandhanoffer.in.net/RakhiOff/ — which mimics a legitimate e-commerce platform but is designed to deceive and defraud visitors.
False delivery/shipping alerts: Scammers pretend to be courier or e‑commerce support teams. For instance, after ordering a Rakhi, you might get a WhatsApp or SMS saying the gift needs an urgent delivery fee. You’re given a payment link or told to call a “support number”. Victims who pay are tricked into revealing bank details or unknowingly approving UPI payments. Cloudsek warns of “fake alerts for shipments” with links to pay delivery charges. The recommended safeguard is to verify any shipment notice independently – e.g. check the tracking number on the official courier site or call the real courier’s helpline from their official website.
Fraudulent Gift Card UPI/payment requests: Be wary of UPI “collect” requests or payment links tied to Rakhi greetings. Scammers may send a fake message saying “Brother sent ₹X gift, click here to receive it” or share a phony QR code for Rakhi gifts. In reality, clicking may trigger a UPI payment to the fraudster. Cloudsek have noted similar scams where viral messages claim a government gift but actually trick users into sending money via UPI. Never approve an unexpected UPI request: always double-check the payee’s name and refuse links that ask for your payment PIN or OTP. If something appears official (e.g., government, bank, or e-retailer), cross-verify by searching official sites directly rather than relying on social media links.
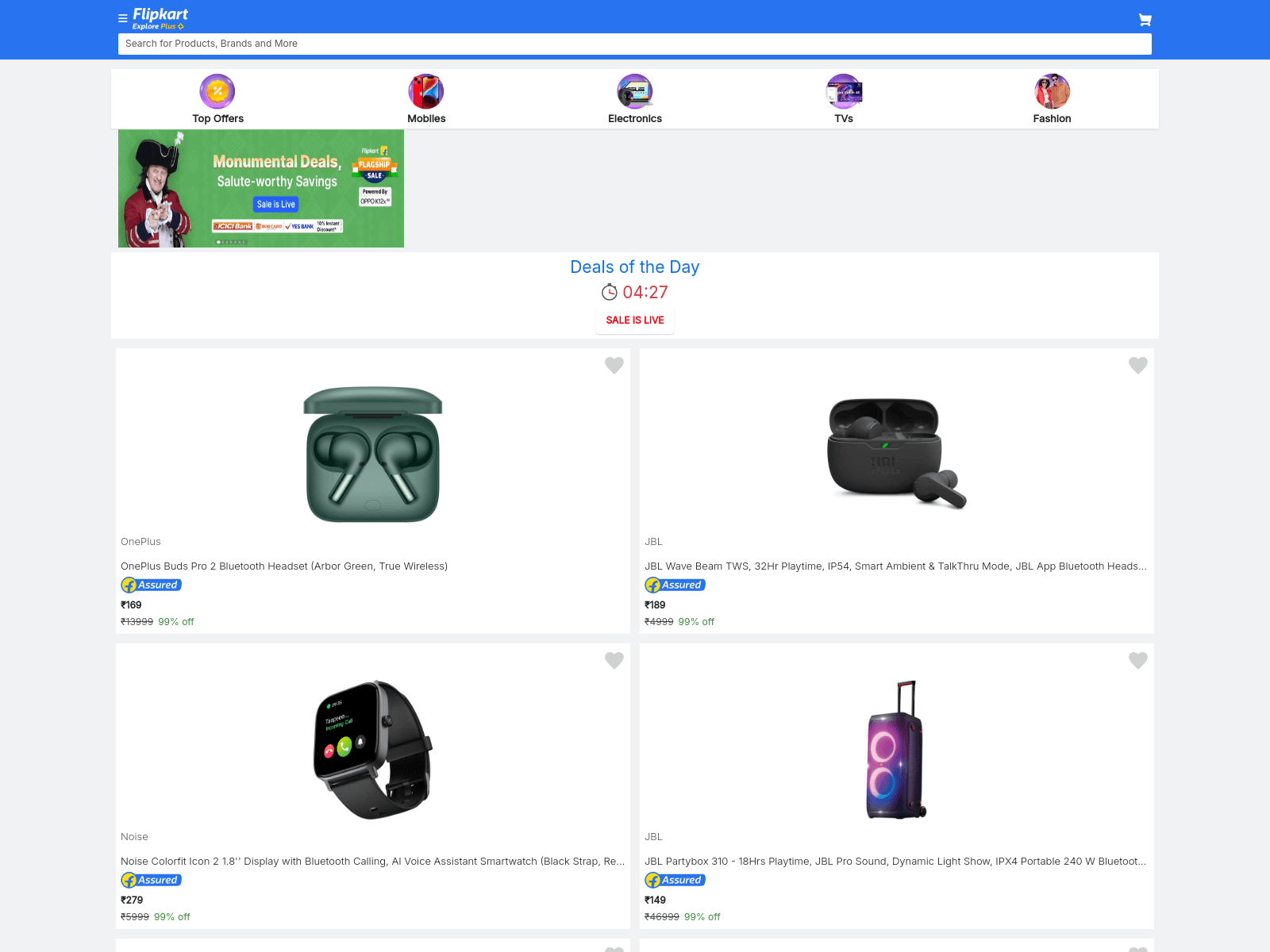
The threat actor appears to be targeting multiple regions by tailoring content in various languages, including Hindi, Telugu, and Tamil. They have crafted phishing campaigns offering fake ₹5,000 gift cards to lure victims.
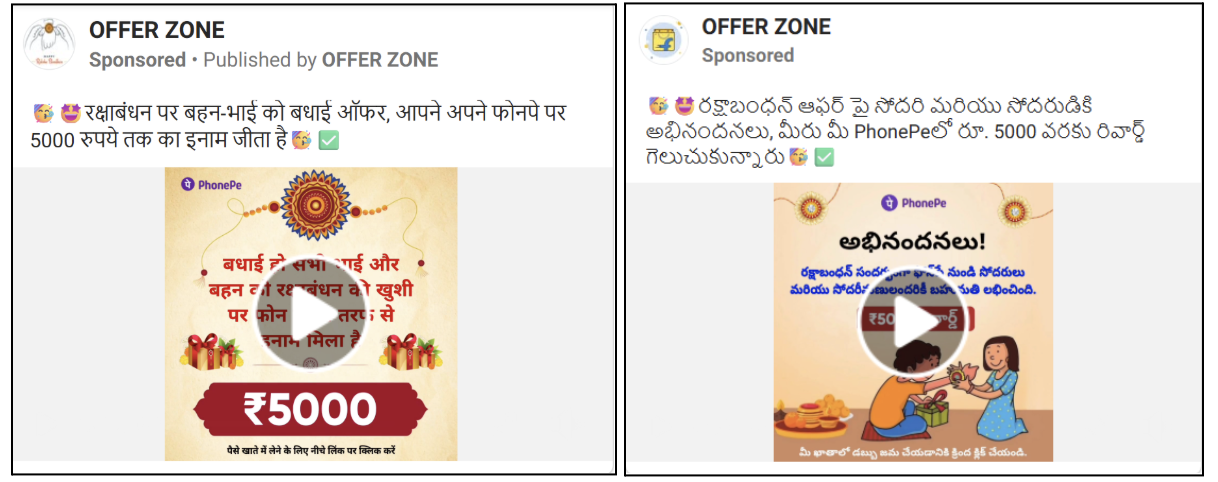
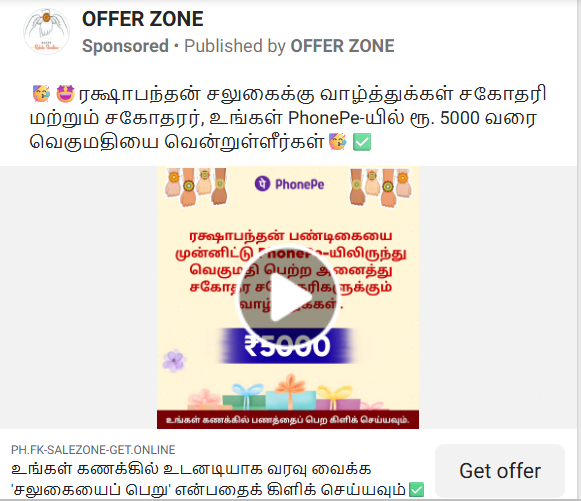
When a victim clicks on any template, they are redirected to a phishing website that falsely claims to offer a gift card from the Prime Minister under the Mudra Yojana. Upon clicking the “Scratch Here” button, an intent-based UPI prompt opens apps like Paytm or PhonePe, allowing the user to directly transfer money to the scammer by simply entering a UPI code.
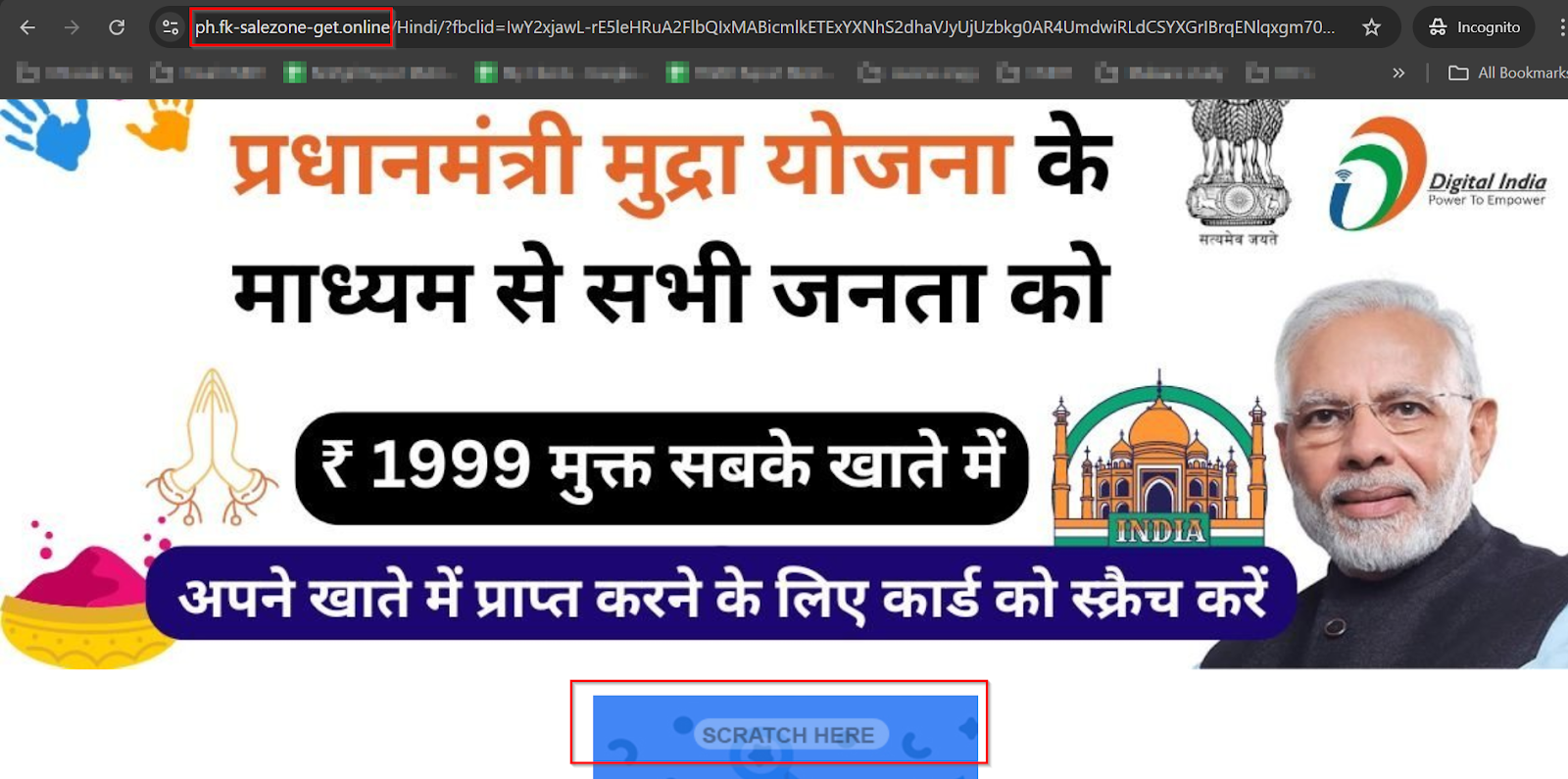
During our deep-dive investigation, our team identified the scammer’s banking details, including their UPI ID: 34161FA82032*AA2D24E6B40@mairtel. This UPI ID is linked to a registered business named "udayrajkiranastore."
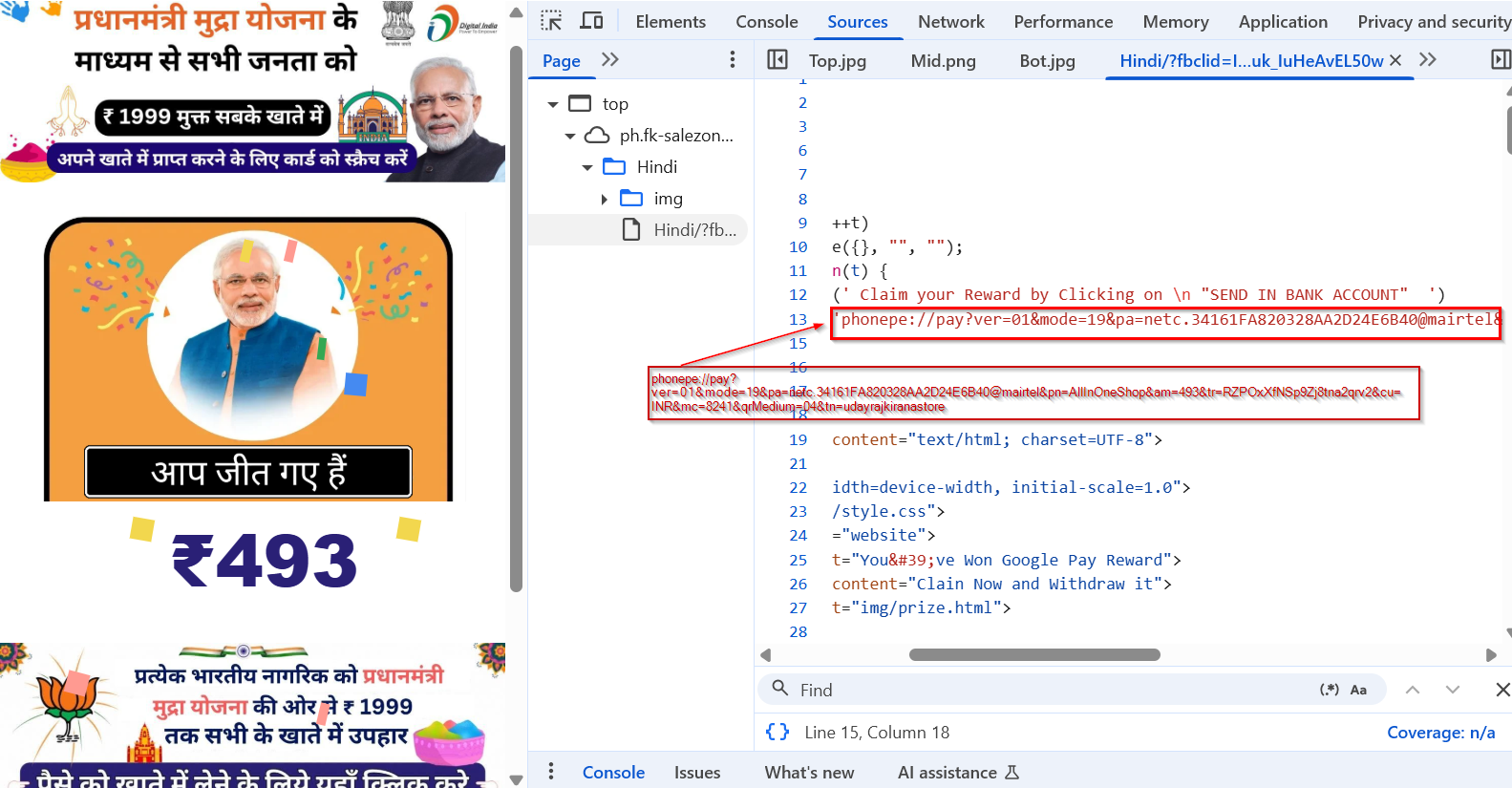
Through threat hunting and OSINT efforts around "udayrajkiranastore", we discovered a Facebook profile belonging to a suspected threat actor named Shyam Saini. Interestingly, the same UPI payment code appears to have been unknowingly uploaded on his profile.
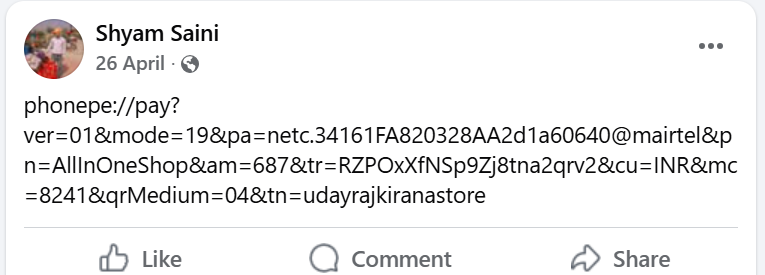
The suspected threat actor behind the gift card scam campaign has been identified as Shyam Saini. Profile URL: https://www.facebook.com/shyam.saini.263528
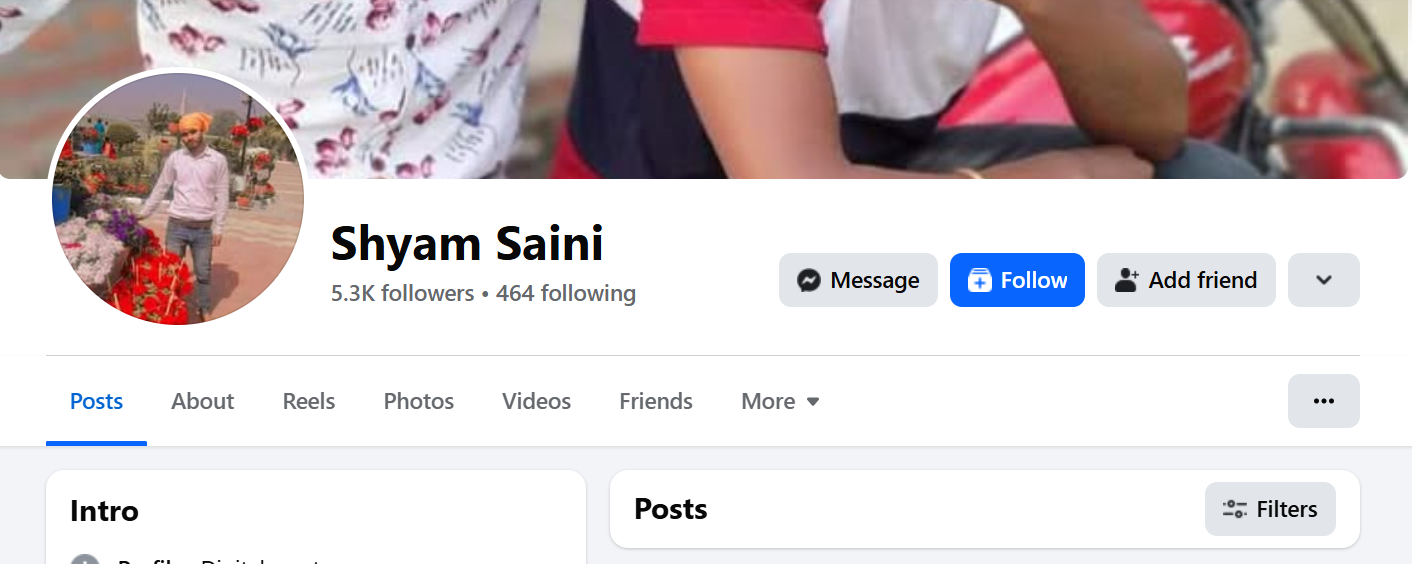
In another threat hunting instance, our team discovered a domain impersonating Raksha Bandhan offers — https[:]//rakshabandhanofer.xyz/ — which was hosting a phishing kit named Giftcard as PM.zip.
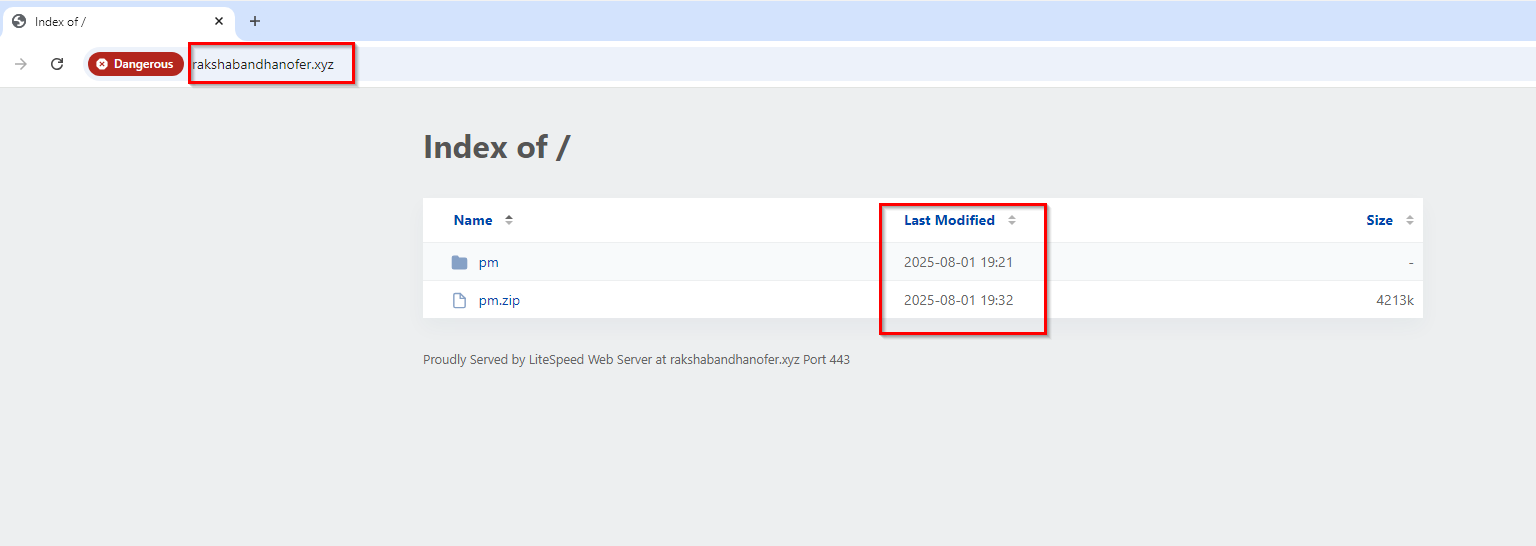
Upon extracting PM.zip, we found that it contained an entire phishing kit designed to support the gift card scam, falsely presented under the guise of the Prime Minister’s Mudra Yojana.

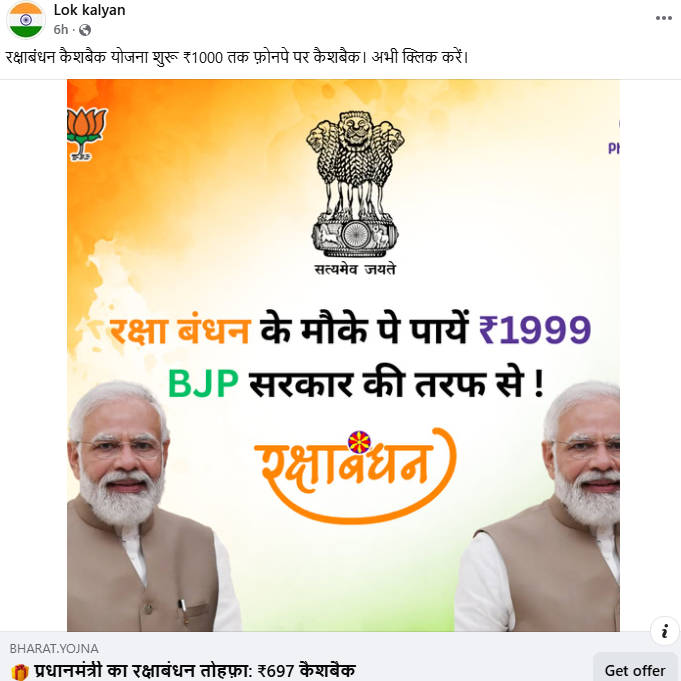
We discovered that this scam is also being circulated on the Facebook platform, where users are lured with a fake ₹1,000-2000 cashback offer under the guise of a Raksha Bandhan festival promotion.
Impersonation/emotional scams: Rakhi is about brother-sister love, and con artists play on that emotion. Some scammers pose as siblings, cousins or even parents in distress. For example, an Indian Express report details a Mumbai woman who received an Instagram friend request from someone claiming to be her “brother” in London. He said he was sending her a Rakhi gift but needed her to pay customs and delivery fees. Over several days she paid ₹8.20 lakh in fake charges before realizing it was a scam. Other con artists may pretend to be elderly relatives or friends in trouble, asking for money urgently. Always pause and verify: call the relative through a known number (not the one the scammer gives) or ask family members directly before sending any money.
Fake support/tech scams: Scammers may impersonate customer support for e‑commerce companies. A common trick is to lure frustrated shoppers onto a WhatsApp or phone call and then request screen-sharing. One India Today story describes how fraudsters posing as “Ecommerce Support” video-called a customer on Raksha Bandhan, insisting she share her screen. They planned to push a malicious app prompt and capture her OTP to drain her bank account. Legitimate companies will never ask you to share your screen or see your PIN. If someone calls claiming to help with your Rakhi order or bank issues, hang up and contact the company yourself via official channels.
News reports show how these scams play out in India:
These cases illustrate the variety of Rakhi-related frauds – from cloned websites and customer support scams to heart-tugging impersonations.
By keeping these precautions in mind, you can ensure your Raksha Bandhan remains joyous. Celebrate the sibling bond – but always double-check online offers or delivery requests. Stick to trusted platforms and official channels, and remember: no gift or deal is worth risking your hard‑earned money or personal data. Stay safe and enjoy a happy, scam‑free festival!