🚀 CloudSEK has raised $19M Series B1 Round – Powering the Future of Predictive Cybersecurity
Read more
The Middle East stands at the forefront of digital innovation. With ambitious national strategies like Saudi Vision 2030, UAE’s Digital Government Strategy, Qatar National Vision 2030, and Kuwait Vision 2035, countries in the region are rapidly embracing cloud adoption, smart infrastructure, and AI-led services. While this digital transformation promises enhanced efficiency and citizen engagement, it also creates a significantly larger and more complex attack surface.
This surge in connectivity, coupled with the region’s geopolitical importance and critical energy reserves, has made Middle Eastern nations prime targets for cyber adversaries. State-sponsored threat groups are launching espionage and sabotage campaigns, ransomware syndicates are extorting major enterprises, and hacktivists are exploiting political unrest to deface, disrupt, and disinform. Meanwhile, vulnerabilities in cloud infrastructure, supply chains, and user credentials are increasingly being exploited—often going undetected until it’s too late.
Regulatory bodies across the GCC have responded by rolling out robust cybersecurity and data protection frameworks from the UAE’s IAS and DESC ISR to Saudi Arabia’s NCA ECC and SAMA guidelines. However, compliance alone cannot defend against today’s evolving threats. Organizations need real-time visibility, contextual threat intelligence, and proactive risk mitigation to stay secure.
In this blog, we break down the most common and critical cybersecurity threats facing the Middle East today, while also examining the compliance and regulatory frameworks across four key countries: the UAE, Saudi Arabia, Kuwait, and Qatar , along with insights on why a reactive approach is no longer sufficient and how intelligent platforms like CloudSEK can help regional entities move toward continuous, contextual cyber resilience.
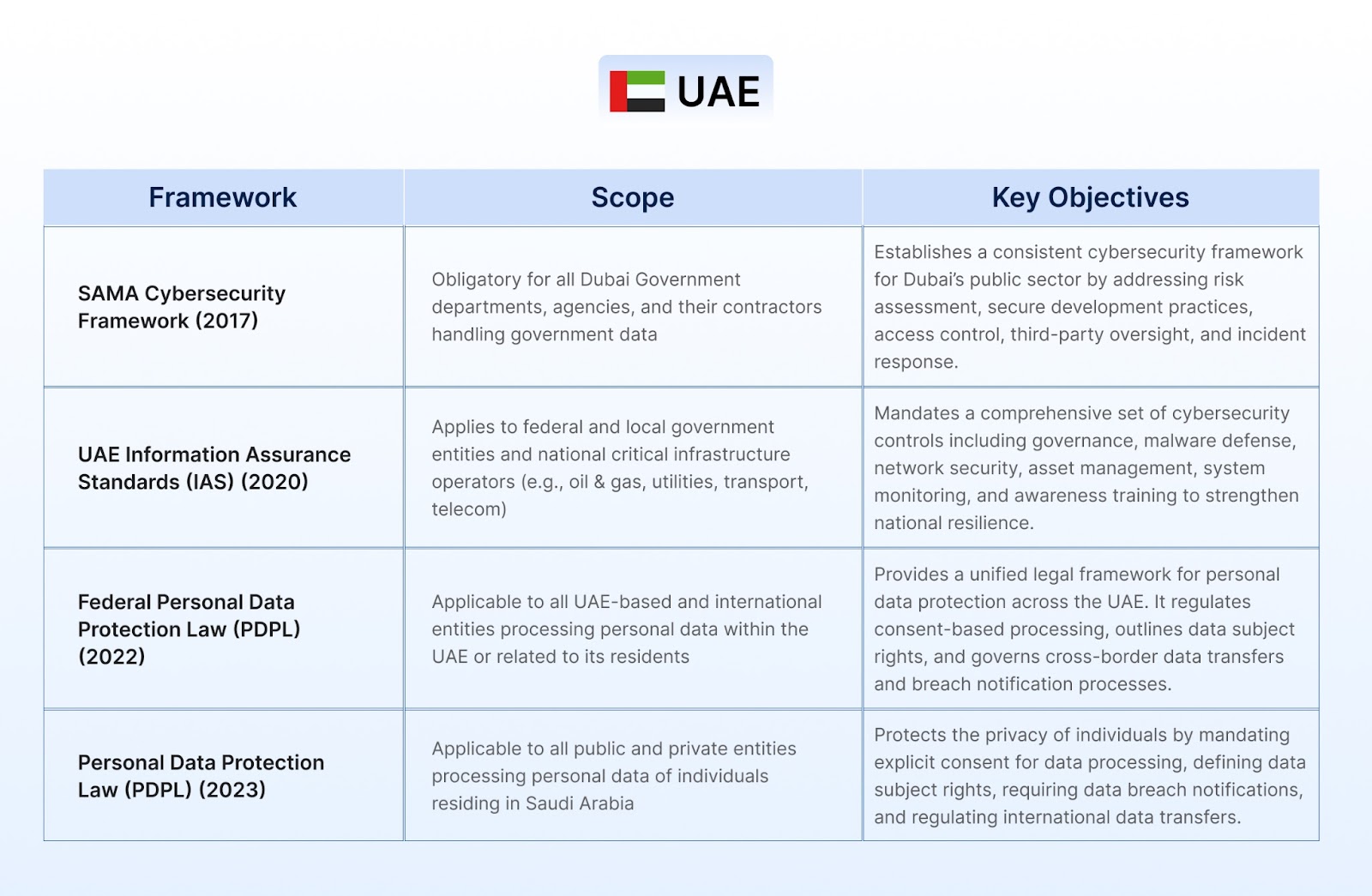
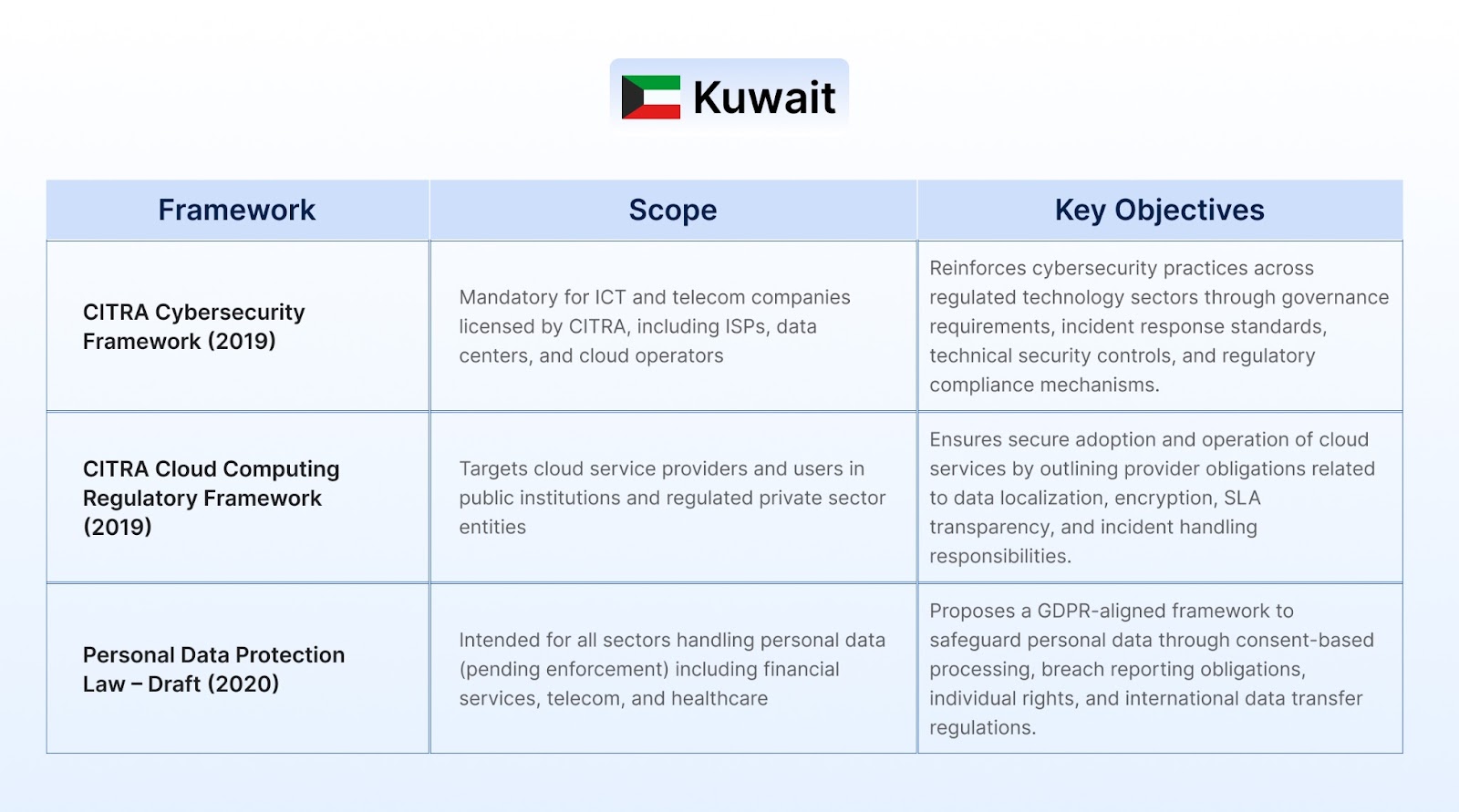
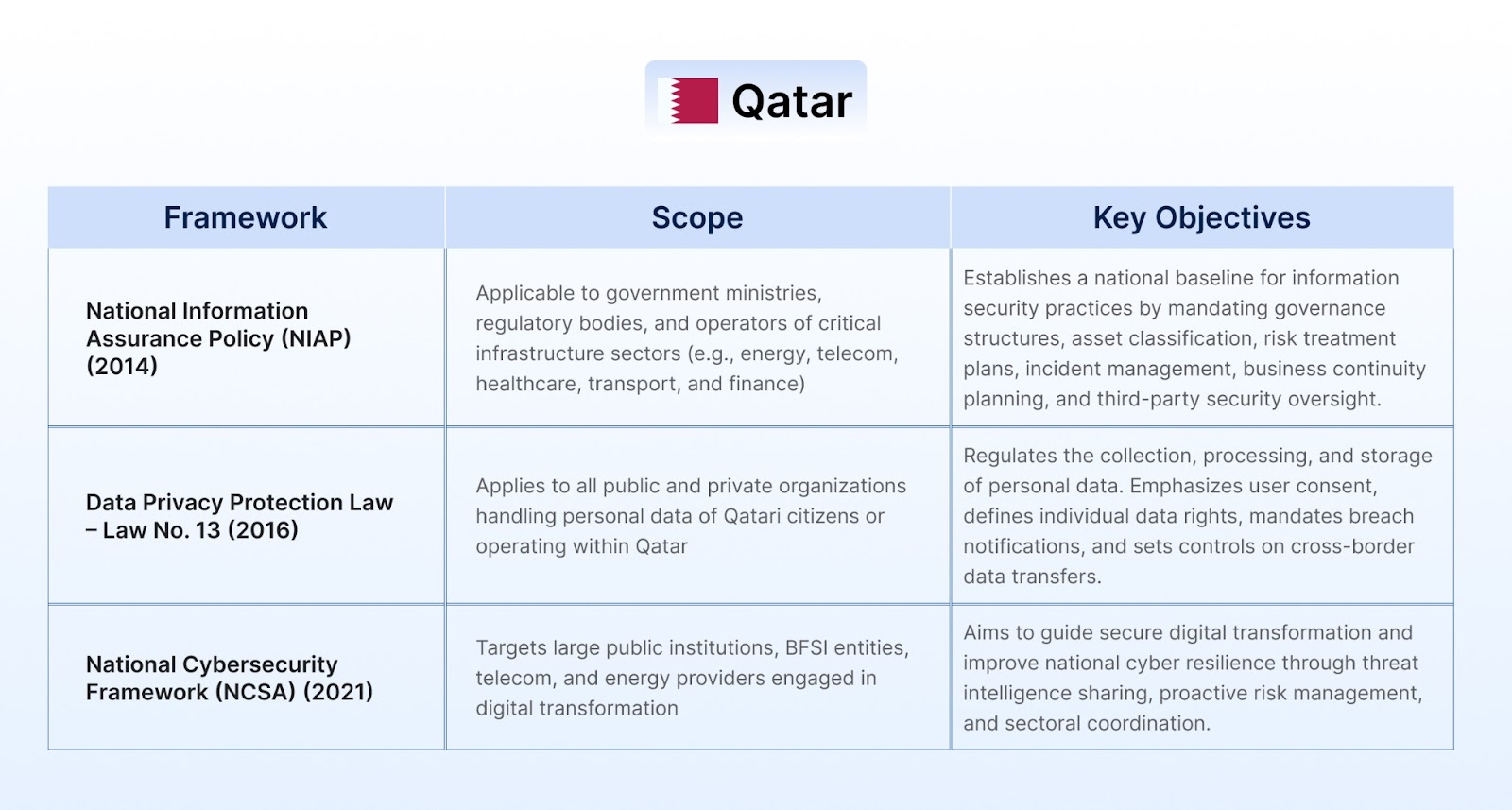
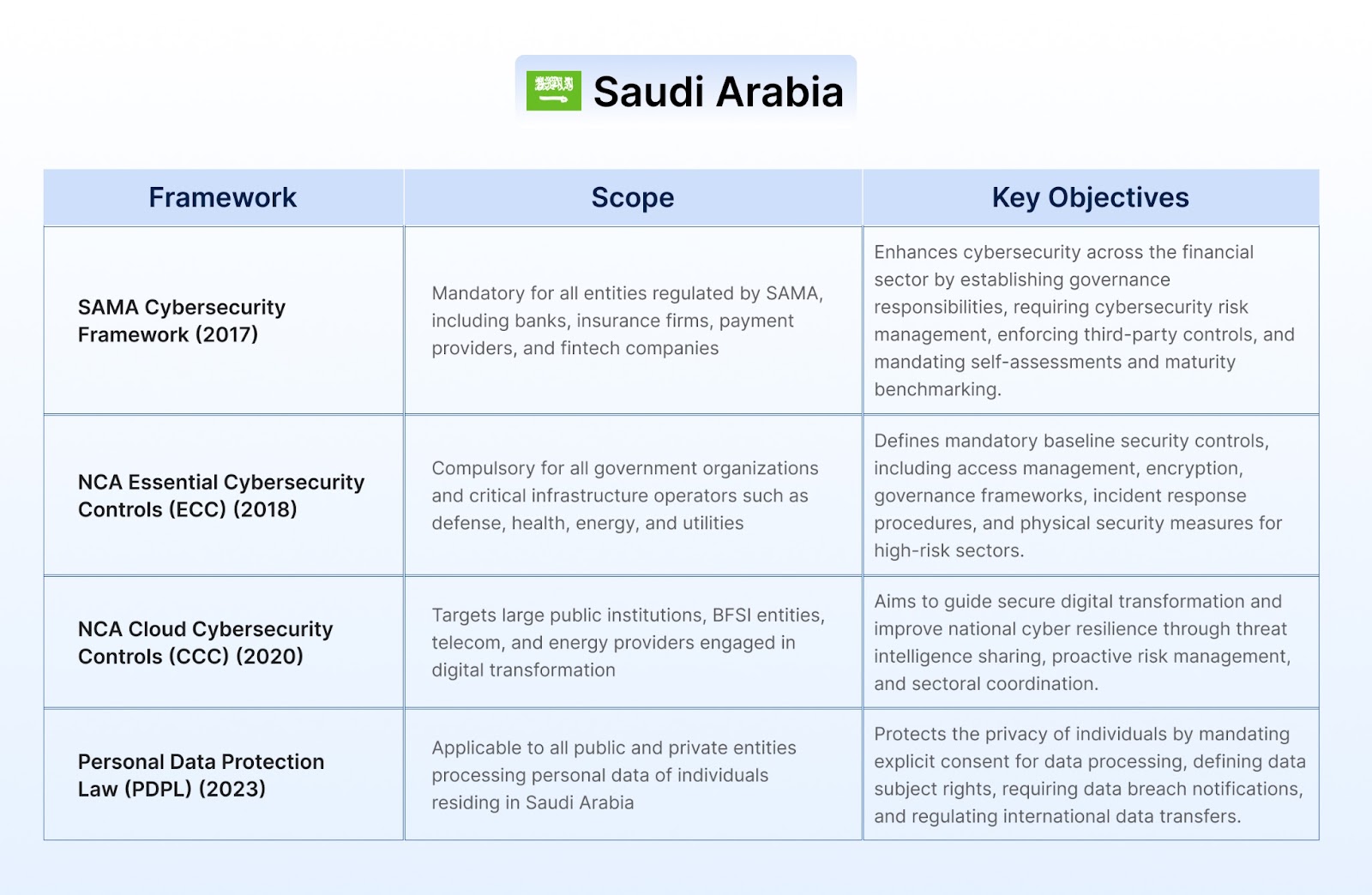
Organizations in the Middle East that fail to comply with cybersecurity and data protection laws face significant penalties, including heavy fines, suspension of services, and revocation of licenses. Regulatory bodies may also blacklist non-compliant entities from public sector contracts or subject them to mandatory audits and remediation. In severe cases, responsible executives could face criminal liability. These penalties aim to enforce strong cyber resilience, protect personal data, and safeguard national infrastructure across sectors like BFSI, telecom, and energy.
Below, we explore real-world use cases that illustrate how organizations across e-commerce, telecom, and government sectors in the Middle East experienced significant cyber incidents and how visibility gaps played a direct role in regulatory non-compliance.
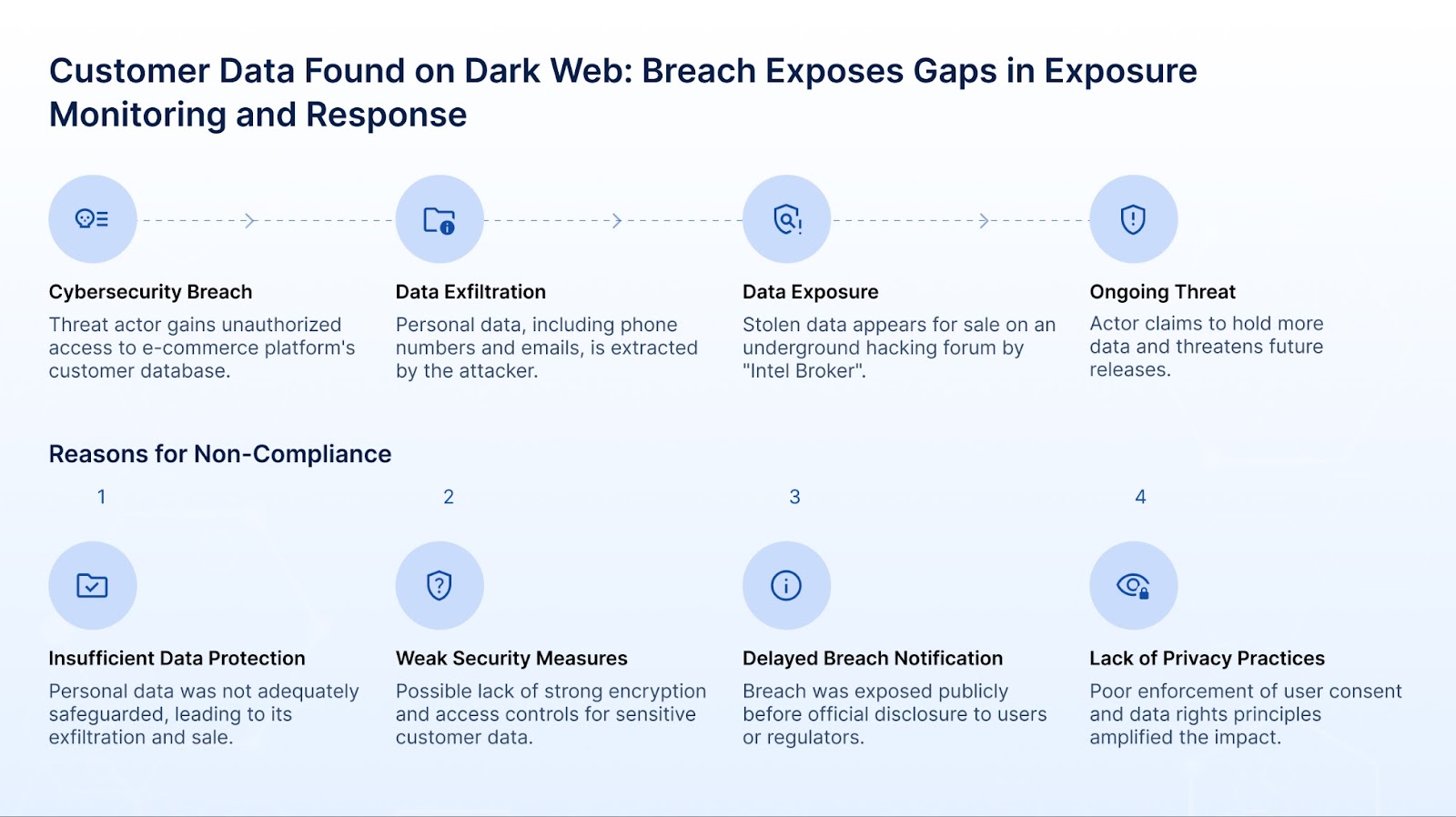
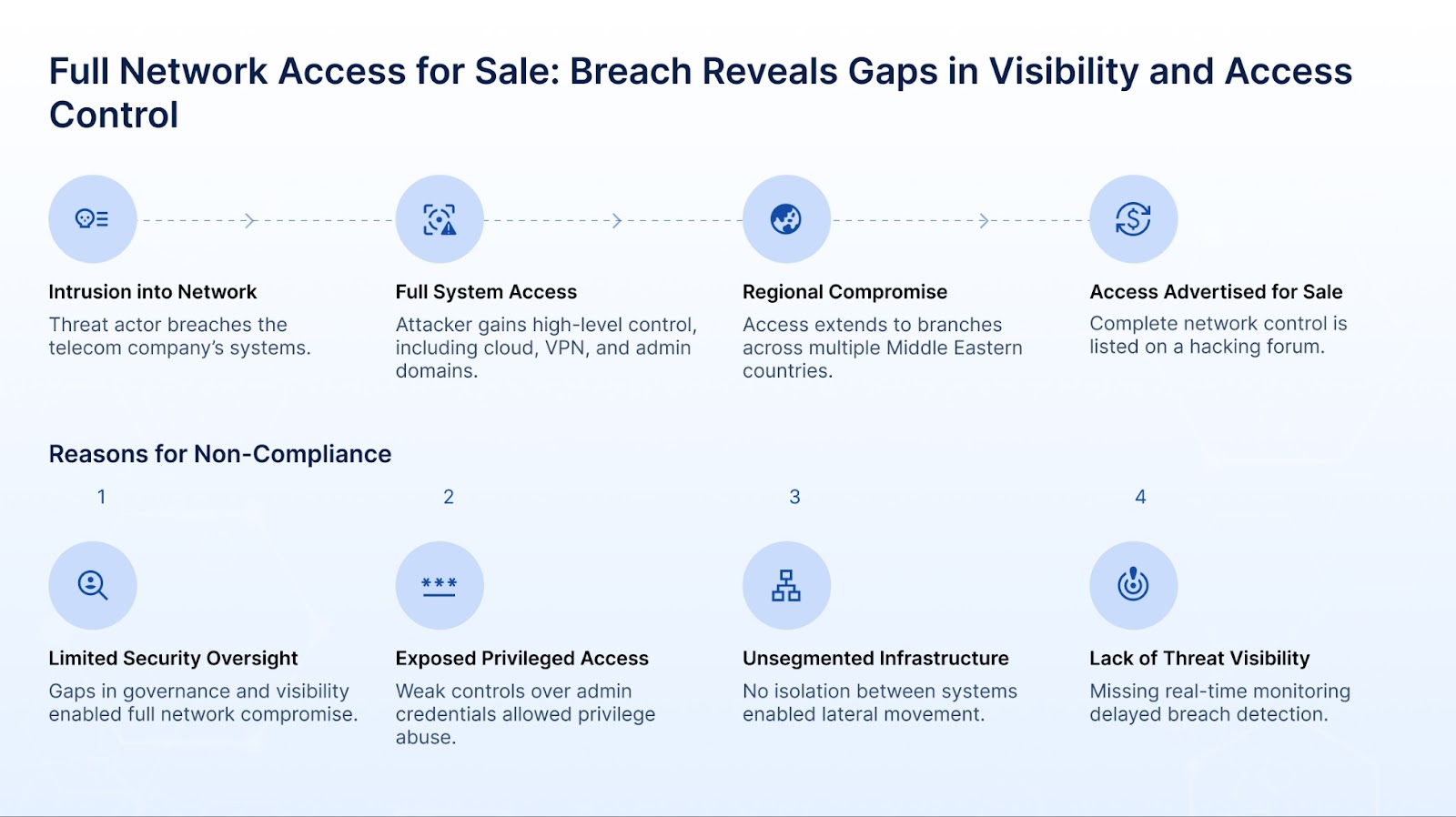

To effectively respond to the rising threat landscape and avoid regulatory fallout, organizations must not only understand where they are exposed, but also how those exposures relate to specific compliance mandates. Each regulatory framework across the Middle East, whether it's Saudi Arabia’s NCA ECC, the UAE’s IAS, or Qatar’s NIAP, outlines baseline security and data protection requirements.
CloudSEK’s modular platform is designed to align directly with these mandates, offering real-time visibility, threat intelligence, and risk monitoring that map to the core control areas defined by various regulators. The table below illustrates how CloudSEK’s capabilities support compliance across key national frameworks.
.jpg)
