| Category:
Adversary Intelligence |
Industry:
Underground |
Motivation:
Financial |
Region:
Global |
Source*:
C - Fairly Reliable
4 - Doubtfully True |
Executive Summary
| THREAT |
IMPACT |
MITIGATION |
- New phishing-as-a-service platform named “Caffeine”, used to conduct phishing campaigns.
|
- Equip malicious actors with details required to launch sophisticated ransomware attacks, exfiltrate data, and maintain persistence.
- Steal sensitive information such as PII and exploit them through social engineering attacks.
|
- Implement a strong password policy.
- Enable MFA across logins.
- Check for anomalies in the endpoints or suspected login attempts.
|
Analysis and Attribution
Information from the Post
- CloudSEK’s contextual AI digital risk platform XVigil discovered a new phishing-as-a-service platform named “Caffeine.”
- The platform could be leveraged to launch phishing campaigns by opting for phishing services providing custom phishing kits.
- The platform mostly contains phishing templates customized to attack Russian and Chinese entities.
[caption id="attachment_21680" align="alignnone" width="652"]

Login Page of the platform[/caption]
Caffeine Platform Analysis
- The platform is open to all and does not require any referral code to register.
- Upon registering on the platform, the threat actor can buy a subscription license which ranges depending on the operator and features:
- USD 250 for a month
- USD 450 for 3 months
- USD 850 for 6 months
- The platform also offers anti-detection and anti-analysis systems and customer support services along with the subscription, making it expensive as compared to other Phishing-as-a-service platforms.
- The platform also offered the following features apart from phishing services:
- Mechanisms for customizing dynamic URL schemes to help dynamically generate sites with victim-specific data already filled in
- Ultimate luring pages and first-stage redirect pages for campaigns.
- Geo-blocking, CIDR range-based blocking, and other IP blocklisting options
- At the time of writing this, the platform seems to be temporarily down due to maintenance issues.
[caption id="attachment_21681" align="alignnone" width="453"]

Store under maintenance[/caption]
Caffeine Service Analysis
- CloudSEK researchers investigated the services available on the "Caffeine" platform and discovered that the threat actor was misusing an online service called - ongraphy[.]com which is a no-code SaaS platform to host websites or apps to launch teaching business websites.
- Similar SaaS services are quickly abused and adopted by other threat actors to host malicious pages.
- An old phishing page was hosted and disseminated via email ("eduardorodiguez9584.[ongraphy.]com")
Information from the Cybercrime forum
- The platform “Caffeine” emerged in October 2021 when the threat actor named “MRxCODER” advertised about the store and office365 sender.
- The threat actor also operates on telegram where regular updates and new tools from the platform are advertised.
- The video demonstration for the python spamming tools from the Caffeine platform was advertised on crax tube.
Information from OSINT
- The platform's Telegram channel promoted numerous bots and an Office 2FA cookies stealer. On the channel, the following were advertised:
- Caffeine Sender
- Caffeine Redirect
- OfficeTools FUD Telegram Bot
- Chase Bank KIT
- FUD Links Service
- Boa Kit
- Dubai Islamic Bank Kit
- Office 365 Cookies stealer
- The threat actor or Caffeine Store administrator surveyed on Telegram to inquire about the next phishing kit.
How can services offered be abused?
- Phishing kits for Chase Bank, Bank of America, and Dubai Islamic Bank are advertised on the service's Telegram channel, along with a service to make FUD phishing URLs that can be used to launch extensive phishing campaigns and attacks.
- Office 2FA cookie stealer can be used to steal 2FA cookies, victim's PII, and gather logs.
- Provides an email template for spamming customers and luring victims.
- The Ongraphy domain served as a redirect to a phishing page housed at a third-party domain that mimics the appearance of the official website for an Italian ophthalmologist's medical practice.
Threat Actor Activity and Rating
| Threat Actor Profiling |
| Alias |
MRxCODER |
| Active since |
2021 |
| Reputation |
Medium |
| Current Status |
Active |
| Telegram |
t.me/caffeinestore_news [decent number of subscribers]
@mrxc0der
@mrxc0derii |
| ICQ |
https://icq.im/caffeine |
| Crax Tube |
https://crax.tube/@caffeinestore |
| Underground Forum |
https://www.nulled.to/user/1018926-mrxc0der |
| History |
Threat actor advertised about the Caffeine store and free carrier lookup bot |
| Rating |
C4 (C: Fairly Reliable; 4: Doubtfully True) |
References
Appendix
[caption id="attachment_21682" align="alignnone" width="1254"]

Advertisement on cybercrime forum[/caption]
[caption id="attachment_21683" align="alignnone" width="917"]

Screenshot from the Telegram channel[/caption]
[caption id="attachment_21684" align="alignnone" width="896"]

Telegram Channel[/caption]
[caption id="attachment_21685" align="alignnone" width="1716"]
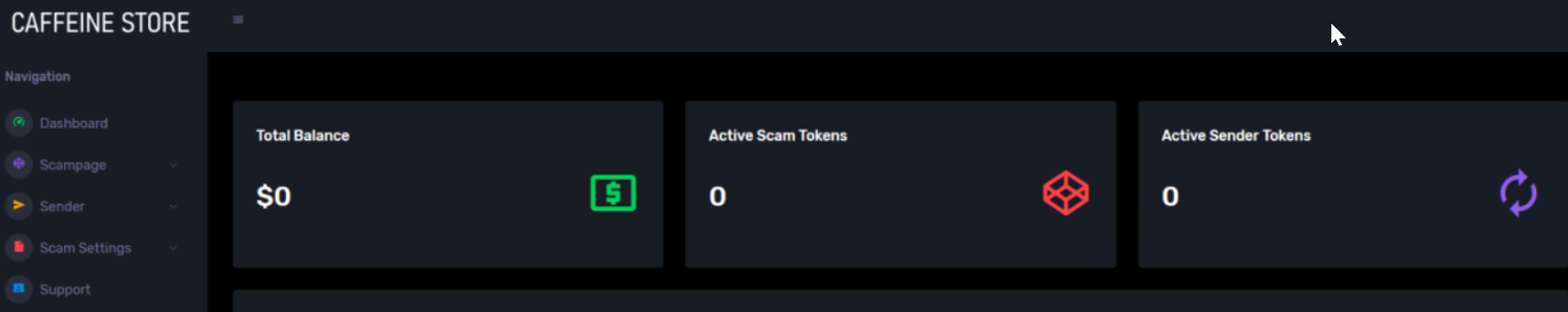
Dashboard of Caffeine[/caption]
[caption id="attachment_21686" align="alignnone" width="1688"]

Dashboard of Caffeine[/caption]
[caption id="attachment_21687" align="alignnone" width="400"]

Logo of Caffeine Store[/caption]
 Login Page of the platform[/caption]
Login Page of the platform[/caption]
 Store under maintenance[/caption]
Store under maintenance[/caption]
 Advertisement on cybercrime forum[/caption]
[caption id="attachment_21683" align="alignnone" width="917"]
Advertisement on cybercrime forum[/caption]
[caption id="attachment_21683" align="alignnone" width="917"] Screenshot from the Telegram channel[/caption]
[caption id="attachment_21684" align="alignnone" width="896"]
Screenshot from the Telegram channel[/caption]
[caption id="attachment_21684" align="alignnone" width="896"] Telegram Channel[/caption]
[caption id="attachment_21685" align="alignnone" width="1716"]
Telegram Channel[/caption]
[caption id="attachment_21685" align="alignnone" width="1716"] Dashboard of Caffeine[/caption]
[caption id="attachment_21686" align="alignnone" width="1688"]
Dashboard of Caffeine[/caption]
[caption id="attachment_21686" align="alignnone" width="1688"] Dashboard of Caffeine[/caption]
[caption id="attachment_21687" align="alignnone" width="400"]
Dashboard of Caffeine[/caption]
[caption id="attachment_21687" align="alignnone" width="400"] Logo of Caffeine Store[/caption]
Logo of Caffeine Store[/caption]








