🚀 CloudSEK has raised $19M Series B1 Round – Powering the Future of Predictive Cybersecurity
Read more




APT73/BASHE, a newly emerged ransomware group active since April 2024, mimics established groups like LockBit. Targeting mid-sized organizations with annual revenues of $10M–$500M, their victims span the Financial Services, IT, Banking, and Manufacturing sectors. They focus on exfiltrating sensitive data to create a facade of legitimacy for their claims, prioritizing targets in North America, Europe and Asia. Despite signs of inexperience, their adaptive strategies suggest potential for rapid growth.
Bashe ransomware group thrives on false claims and fabricated victories, operating as little more than opportunistic fraudsters in the world of cybercrime. Their strategy of taking credit for attacks they didn’t commit is nothing but a desperate attempt to inflate their relevance to attract legitimate ransomware affiliates. Instead of showcasing genuine technical prowess, Bashe relies on deception, smoke screens, and manipulates their samples by masking PII, making it more challenging to validate their claims. Beneath the facade, their lack of authenticity makes them a prime example of cybercriminal incompetence and overblown theatrics.
Bashe ransomware group falsely claims responsibility for attacks to gain reputation and invite credible threat actors to their affiliate program. This tactic helps them project an image of strength and influence, enticing other cybercriminals to collaborate with them.
We believe that affiliates have either already joined them or will likely join in the near future, driven by the media hype these individuals are generating.
Below are some of the recent targets along with the timelines of their posting dates on the DLS:
Timeline:
1. January 20, 2025: Bashe ransomware group announced on their data leak site, that they have compromised Malindo Air, Bangladesh, listing passenger PII.


Upon further analysis and by examining the masked sample listed on the ransomware DLS website, it was determined that this is a repost of the Malindo Air data leak that originally occurred in March 2019.

To confirm that the post made by Bashe is merely a repost of old data, we randomly selected names from the sample provided by Bashe and cross-checked them against compromises. All the randomly selected names were found to be part of the same Malindo Air data leak that occurred in 2019.
2. January 15, 2025: Bashe announced another leak on their data leak site targeting an online gambling organization Betclic, again listing Customer PII.


Upon analyzing this post and the samples, it was discovered that the data they presented was curated from a combolist hosted on different hacking forums.
The masking of the samples made it challenging to validate the authenticity of this post. However, by randomly selecting names from the sample and analyzing them across various data sources, we noticed one common factor: all the names were present in the same combolist from one of these platforms.
This finding leads us to conclude that this post is yet another fake post where the actor has simply curated data from an existing combolist.
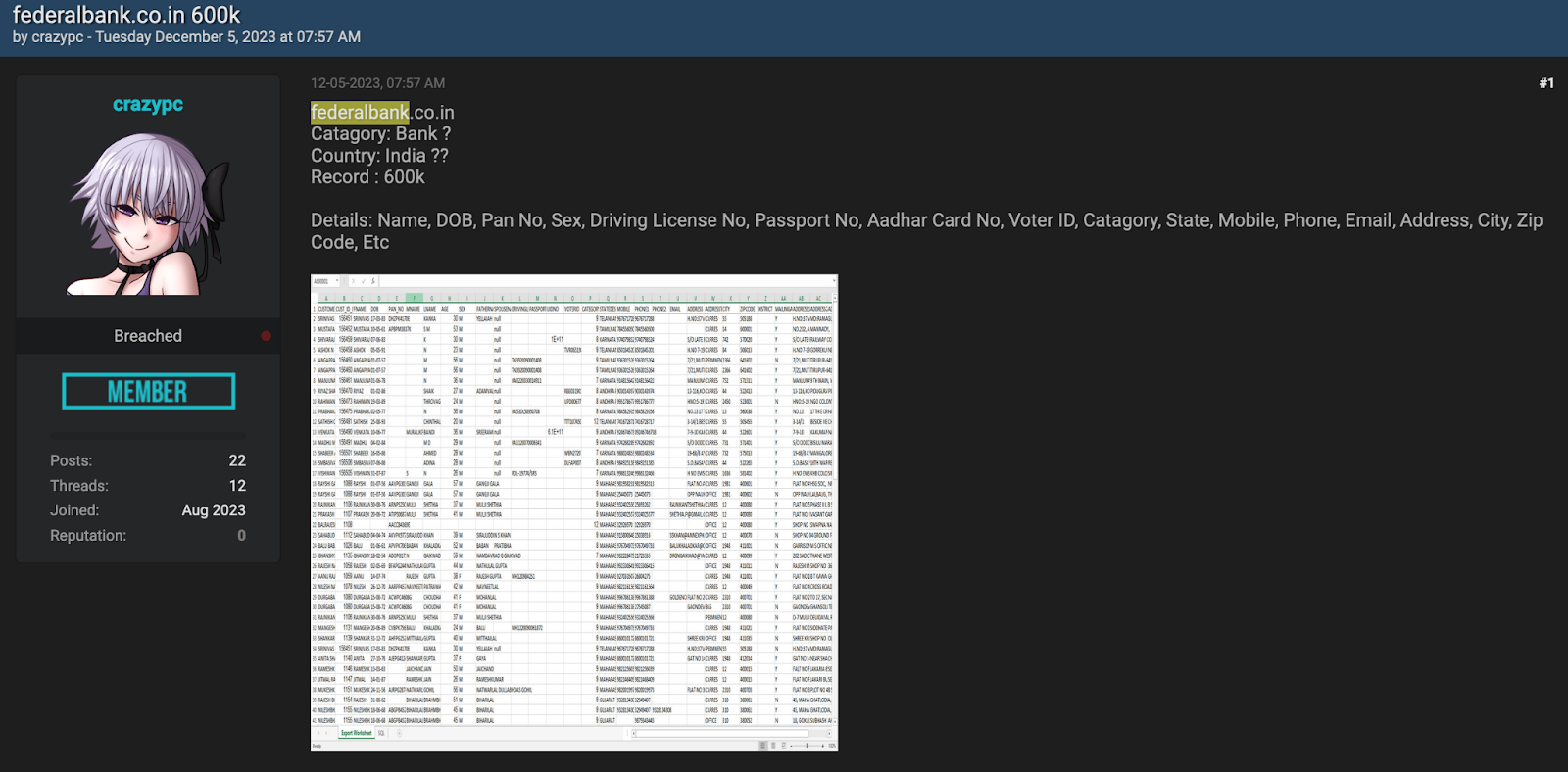
3. December 24, 2024: Bashe announced another leak on their data leak site targeting Federal Bank India giving Customer PII.


Upon analyzing this post and the samples, it was discovered that the sample they presented is identical to the sample posted on Breachforum in May 2023.
4. December 23, 2024: Bashe announced another leak on their data leak site targeting an Indonesian Bank - Linebank, again listing Customer PII.


Upon analyzing this post and the samples, it was discovered that the data they presented is completely irrelevant to Indonesia Bank due to the mentions of Indian Banks IFSC code.


5. December 18, 2024: Bashe announced another leak on their data leak site again targeting an Indonesian Bank - Bank Rakyat Indonesia(BRI) , again listing Customer PII.


Upon analyzing this post and the samples, it was discovered that the sample they presented is identical to one of the documents that is publicly available on a sharing platform.

Alias: eraleign, APT73 (self proclaimed APT)
Activity Level: Highly active
Primary Motivation: Financial gain, Gaining credibility
Bashe demonstrates a broad targeting scope across various industries, including: