| Category:
Adversary Intelligence |
Industry:
Finance and Banking |
Region:
Global |
Source*:
C3 |
Executive Summary
| THREAT |
IMPACT |
MITIGATION |
- Generaly, a new OTP bot setup capable of capturing OTP, Card CVV, pin codes, and recordings of the spoofed calls.
- The bot has a dedicated Telegram channel to capture & display information.
|
- Captured OTP can be used to bypass 2FA and gain complete access to bank accounts.
- P2P payment services like Cashapp and Paypal are affected.
|
- Implement bot-detection technologies and algorithms.
- Verify the legitimacy of the caller before giving away vital information.
|
Analysis and Attribution
- CloudSEK’s contextual AI digital risk platform, XVigil, discovered a post where a threat actor was advertising a Telegram OTP Bot named Generaly.
- OTPs (one-time passwords) are widely regarded as a fool-proof security measure to guarantee authentication whether for authorizing a bank transfer or gaining access to your online accounts.
[caption id="attachment_20059" align="aligncenter" width="1635"]

The crux of the threat actor’s services, advertised on the forum[/caption]
- Another actor was observed offering a bot that could bypass accounts on Paypal, Amazon and in banking/payment sectors. (For more information refer to the Appendix)
- Generaly bot is designed to bypass authentication on payment gateway platforms like Venmo, Paypal, and Cashapp.
- Its use case can be extended to the banking sector with the stealing of card CVV and pin codes.
Modus Operandi
- Prior to the attack, the actor provides the victim’s PII to the bot (phone number is entered with /pp or /call prefixes).
- The bot impersonates a legitimate entity (bank, e-commerce store, etc) by making a spoofed call from the toll-free customer care number to the intended target.
- Telegram bots do not need a registered number, so the possibility of call traces and number lookups can be eliminated.
- The reason for the call can range from anything like unauthorized activity on a bank account or on the online account portal.
- The threat actor then coaxes the victim to log in to the bank’s portal, to verify if the said incident <insert reason> happened.
- Authentication apps or similar mechanisms incorporated on websites, help to validate a legitimate session from said user.
- The bot captures the credentials entered and the OTP from the victim gets exfiltrated.
- Once the OTP is secured, the attacker gains complete access to the compromised accounts.
- This access can be further leveraged for malicious purposes such as withdrawals and long-term access, etc.
- Similar technique is employed to steal CVV numbers and pin codes from bank-issued credit/debit cards.
Tactics, Techniques & Procedures
Adversary Infrastructure
- One of Telegram’s attractive offerings are bots that are used to communicate with humans. Many businesses make use of them to streamline customer needs.
- In this instance, bots are used by threat actors as infrastructure to conduct cybercrime by:
- Capturing the OTP
- Transmitting the OTP to the server side
- The bot comes with a number of predefined message templates that show the steps involved in the crime from the time the victim is first contacted until they hang up.
- An audio transcript of the call is also delivered to the attacker upon conclusion.
Tactics observed
- Social Engineering
- Stealing of OTP and other sensitive information (CVV number, card pin, etc).
- Use of dedicated infrastructure service on Telegram (subtag).
[caption id="attachment_20060" align="aligncenter" width="798"]

Screenshot of the dedicated channel of the Generaly bot, on Telegram[/caption]
Monetary Benefits
- Three lease options, i.e daily, weekly, and monthly plans, are available for the bot.
- There is an option to purchase the bot outright for USD 250,000.
- Primary mode of purchase is via cryptocurrency using Coinbase as a payment platform.
- Payments can also be made via other cryptocurrencies like Ethereum, Bitcoin, and Bitcoin Cash.
- Access to the bot is sent to the customer’s email address.
Threat Actor Activity & Rating
| Threat Actor Profiling |
| Active since |
October 2020 |
| Reputation |
High (Few complaints and concerns against them) |
| Current Status |
Active |
| History |
- Seller of spammed credit cards and gift cards for popular brands like Dunkin’ Donuts & Amazon.
- They also sell logs sourced from information stealers.
- Provides tools and services for smishing attacks and OTP bypasses.
- Known for paying other actors for promoting their website’s products and offerings.
|
| Target Countries |
France, India, & USA |
| Point of Contact |
SNOWXUP Telegram Channel (t[.]me/snowxup - 4,542 subscribers), SNOWXUP Online Store, Discord (1,622 members), SNOWXUP support channel (t[.]me/datasnow), Bot Telegram Channel (@GeneralyOTPbot) |
| Rating |
C3 (C: Fairly reliable, 3: Possibly True) |
SNOWXUP Online Store
The alleged domain is registered in Turkey and the table below contains its IP and server-related information.
| IP Address |
Name Servers |
| 104.21.13.49 |
Austin.ns.cloudflare.com (United States) |
| 172.67.154.161 |
Jean.ns.cloudflare.com (United States) |
Impact and Mitigation
| Impact |
Mitigation |
- The OTP captured OTP by the bot can be missued to conduct withdrawals, maintain persistence, etc.
- The bot can be used to bypass 2FA mechanisms and to gain complete access to online/bank accounts.
|
- Implement bot-detection technologies and algorithms.
- Create awareness against social engineering tactics.
- Ask the right questions and verify the legitimacy of the individual that is calling, before giving away vital or sensitive information.
|
References
Appendix
[caption id="attachment_20061" align="aligncenter" width="813"]
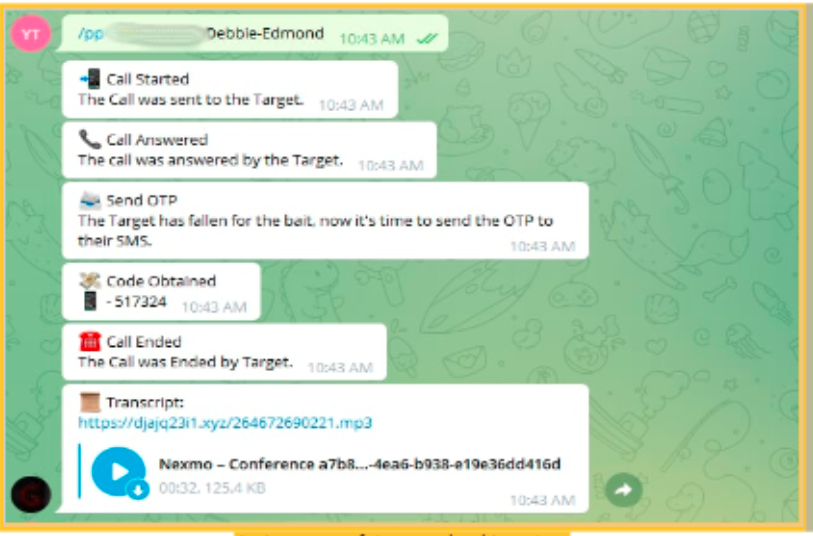
An instance of the attack taking place[/caption]
[caption id="attachment_20062" align="aligncenter" width="543"]

Core purposes of the Generaly bot[/caption]
[caption id="attachment_20063" align="aligncenter" width="1032"]
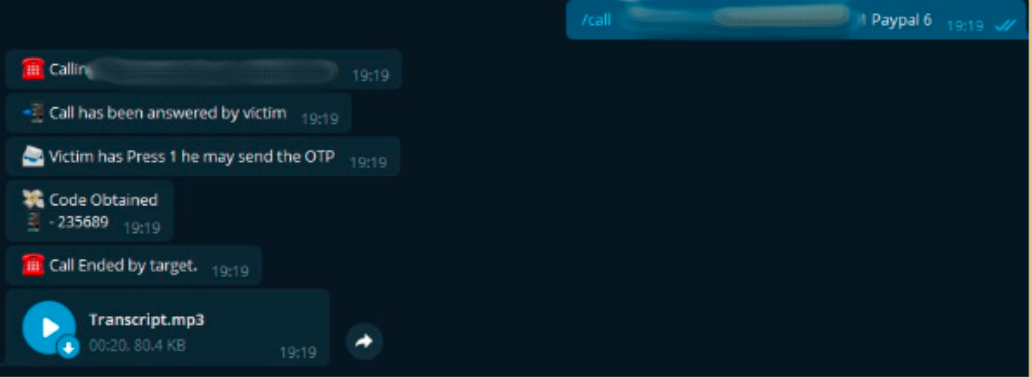
Another instance of the OTP stealing attack taking place[/caption]
[caption id="attachment_20064" align="aligncenter" width="1050"]

Price descriptions for the sale of the OTP bot[/caption]
[caption id="attachment_20065" align="aligncenter" width="438"]

Image of options to send purchased goods[/caption]
[caption id="attachment_20066" align="aligncenter" width="1264"]

Payment methods that are offered to the customer while purchasing the bot[/caption]
[caption id="attachment_20067" align="aligncenter" width="390"]
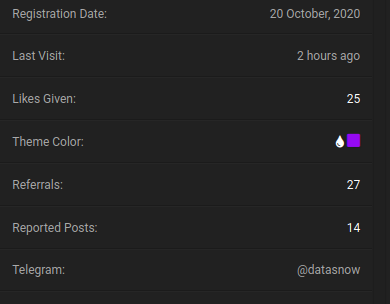
Profile specifics of the threat actor, SNOWXUP - on the underground forum[/caption]
[caption id="attachment_20068" align="aligncenter" width="1635"]

Sponsored advertisements on other threat actor’s profile[/caption]
[caption id="attachment_20069" align="aligncenter" width="531"]

SNOWXUP’s Telegram channel that advertises their services and offerings[/caption]
[caption id="attachment_20070" align="aligncenter" width="396"]

Channel specifics of the threat actor’s shop on Telegram, SNOWXUP[/caption]
[caption id="attachment_20071" align="aligncenter" width="488"]

Samples received by CloudSEK’s researchers’ source[/caption]
[caption id="attachment_20072" align="aligncenter" width="1437"]
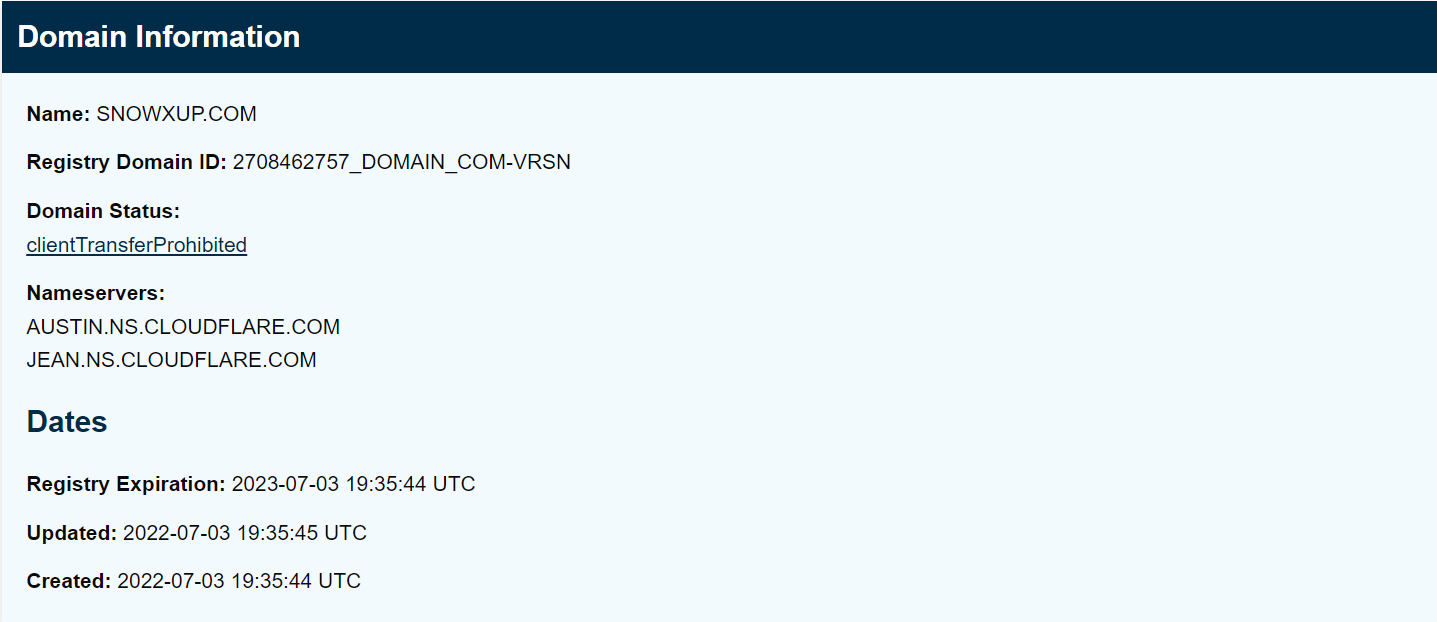
Domain registration information of snowxup.com suggests it to be a new website[/caption]
[caption id="attachment_20073" align="aligncenter" width="1039"]

No transactions had taken place, on this BTC address, at the time of writing this report.[/caption]
(Source - https://www.blockchain.com/btc/address/39WE5wB4WUxbQSvE9DFjmRN7GgR2kMfoKD)  The crux of the threat actor’s services, advertised on the forum[/caption]
The crux of the threat actor’s services, advertised on the forum[/caption]
 Screenshot of the dedicated channel of the Generaly bot, on Telegram[/caption]
Screenshot of the dedicated channel of the Generaly bot, on Telegram[/caption]
 An instance of the attack taking place[/caption]
[caption id="attachment_20062" align="aligncenter" width="543"]
An instance of the attack taking place[/caption]
[caption id="attachment_20062" align="aligncenter" width="543"] Core purposes of the Generaly bot[/caption]
[caption id="attachment_20063" align="aligncenter" width="1032"]
Core purposes of the Generaly bot[/caption]
[caption id="attachment_20063" align="aligncenter" width="1032"] Another instance of the OTP stealing attack taking place[/caption]
[caption id="attachment_20064" align="aligncenter" width="1050"]
Another instance of the OTP stealing attack taking place[/caption]
[caption id="attachment_20064" align="aligncenter" width="1050"] Price descriptions for the sale of the OTP bot[/caption]
[caption id="attachment_20065" align="aligncenter" width="438"]
Price descriptions for the sale of the OTP bot[/caption]
[caption id="attachment_20065" align="aligncenter" width="438"] Image of options to send purchased goods[/caption]
[caption id="attachment_20066" align="aligncenter" width="1264"]
Image of options to send purchased goods[/caption]
[caption id="attachment_20066" align="aligncenter" width="1264"] Payment methods that are offered to the customer while purchasing the bot[/caption]
[caption id="attachment_20067" align="aligncenter" width="390"]
Payment methods that are offered to the customer while purchasing the bot[/caption]
[caption id="attachment_20067" align="aligncenter" width="390"] Profile specifics of the threat actor, SNOWXUP - on the underground forum[/caption]
[caption id="attachment_20068" align="aligncenter" width="1635"]
Profile specifics of the threat actor, SNOWXUP - on the underground forum[/caption]
[caption id="attachment_20068" align="aligncenter" width="1635"] Sponsored advertisements on other threat actor’s profile[/caption]
[caption id="attachment_20069" align="aligncenter" width="531"]
Sponsored advertisements on other threat actor’s profile[/caption]
[caption id="attachment_20069" align="aligncenter" width="531"] SNOWXUP’s Telegram channel that advertises their services and offerings[/caption]
[caption id="attachment_20070" align="aligncenter" width="396"]
SNOWXUP’s Telegram channel that advertises their services and offerings[/caption]
[caption id="attachment_20070" align="aligncenter" width="396"] Channel specifics of the threat actor’s shop on Telegram, SNOWXUP[/caption]
[caption id="attachment_20071" align="aligncenter" width="488"]
Channel specifics of the threat actor’s shop on Telegram, SNOWXUP[/caption]
[caption id="attachment_20071" align="aligncenter" width="488"] Samples received by CloudSEK’s researchers’ source[/caption]
[caption id="attachment_20072" align="aligncenter" width="1437"]
Samples received by CloudSEK’s researchers’ source[/caption]
[caption id="attachment_20072" align="aligncenter" width="1437"] Domain registration information of snowxup.com suggests it to be a new website[/caption]
[caption id="attachment_20073" align="aligncenter" width="1039"]
Domain registration information of snowxup.com suggests it to be a new website[/caption]
[caption id="attachment_20073" align="aligncenter" width="1039"] No transactions had taken place, on this BTC address, at the time of writing this report.[/caption]
(Source - https://www.blockchain.com/btc/address/39WE5wB4WUxbQSvE9DFjmRN7GgR2kMfoKD)
No transactions had taken place, on this BTC address, at the time of writing this report.[/caption]
(Source - https://www.blockchain.com/btc/address/39WE5wB4WUxbQSvE9DFjmRN7GgR2kMfoKD)







