🚀 CloudSEK has raised $19M Series B1 Round – Powering the Future of Predictive Cybersecurity
Read more




Over the past decade, the English-speaking cybercriminal ecosystem commonly referred to as “The COM” has undergone a profound transformation. What began as a niche subculture centered on the trading of what is called “OG Usernames (original gangster)” social media handles has evolved into a sophisticated, service-oriented economy that drives some of the most disruptive cyberattacks worldwide. Today, The COM drives a wide spectrum of cybercriminal activity, including large-scale data breaches, extortion campaigns, SIM-swapping attacks, ransomware incidents, cryptocurrency draining, rug pulls, and other forms of financial fraud frequently targeting multinational corporations, government entities, critical infrastructure, and retail investors alike.
The COM's foundations were laid in early forums like RaidForums, which cultivated a strong sense of community and reputation among threat actors. These early spaces provided fertile ground for the rise of forums like OGUsers, which further amplified social engineering tactics and account takeovers. Following a wave of law enforcement takedowns and forum disruptions, a “Migration Effect” occurred blending the manipulation skills of OG traders with the technical expertise of breach-focused hackers. This convergence created a new generation of agile, reputation-driven cybercriminals.
This report charts The COM’s evolution and analyzes its fusion with key threat actor groups, including Lapsus$, ShinyHunters, Scattered Spider (UNC3944), and the Silent Ransom Group (SRG). It explores their organizational structures, monetization models, and the underground supply chains that enable their operations. Additionally, the report examines the response from law enforcement and provides a forward-looking assessment of the threats posed by this increasingly decentralized and adaptive ecosystem.
The contemporary English-speaking cybercriminal threat landscape cannot be understood without appreciating the historical, cultural, and technical tapestry from which it emerged. What began as loosely-federated forums for “OG” (original gangster) username hunters rapidly evolved by necessity and profit incentive into a professionalized illicit economy. This new “as-a-service” environment supports a near-infinite array of attack vectors, drawing in participants globally and erasing many prior barriers to entry.
The COM ecosystem is fundamentally built on social engineering tactics exemplified by OGUsers’ “callers,” Lapsus manipulation of IT staff, and the GTA VI hack executed from a hotel room.
Takeaway: Organizations must prioritize protecting IT/help desk personnel as a critical security layer.
SIM swapping, pioneered on OGUsers, enables attackers to drain crypto wallets and compromise enterprise accounts, making SMS-based MFA a core vulnerability.
Takeaway: SMS-based 2FA is critically insecure for high-value accounts.
Groups like Lapsus$ actively recruited or coerced employees to access internal tools, as seen in the Twitter breaches.
Takeaway: Insider threat programs must include social engineering and coercion scenarios.
From financially motivated crypto thieves to fame-seeking groups like Lapsus$ and ShinyHunters, attacker goals include disruption and notoriety.
Takeaway: Incident response must address reputational damage and public taunting, not just data theft.
Law enforcement takedowns of major forums (RaidForums, BreachForums) cause fragmentation but not collapse, pushing activity onto Telegram, Discord, and invite-only channels.
Takeaway: Threat intelligence can’t rely solely on traditional forums.
The roots of the cybercriminal online marketplace (COM) ecosystem trace back to the early and mid-2010s, a period when English-speaking cybercriminals driven by profit and reputation began gathering in public and semi-private online forums.
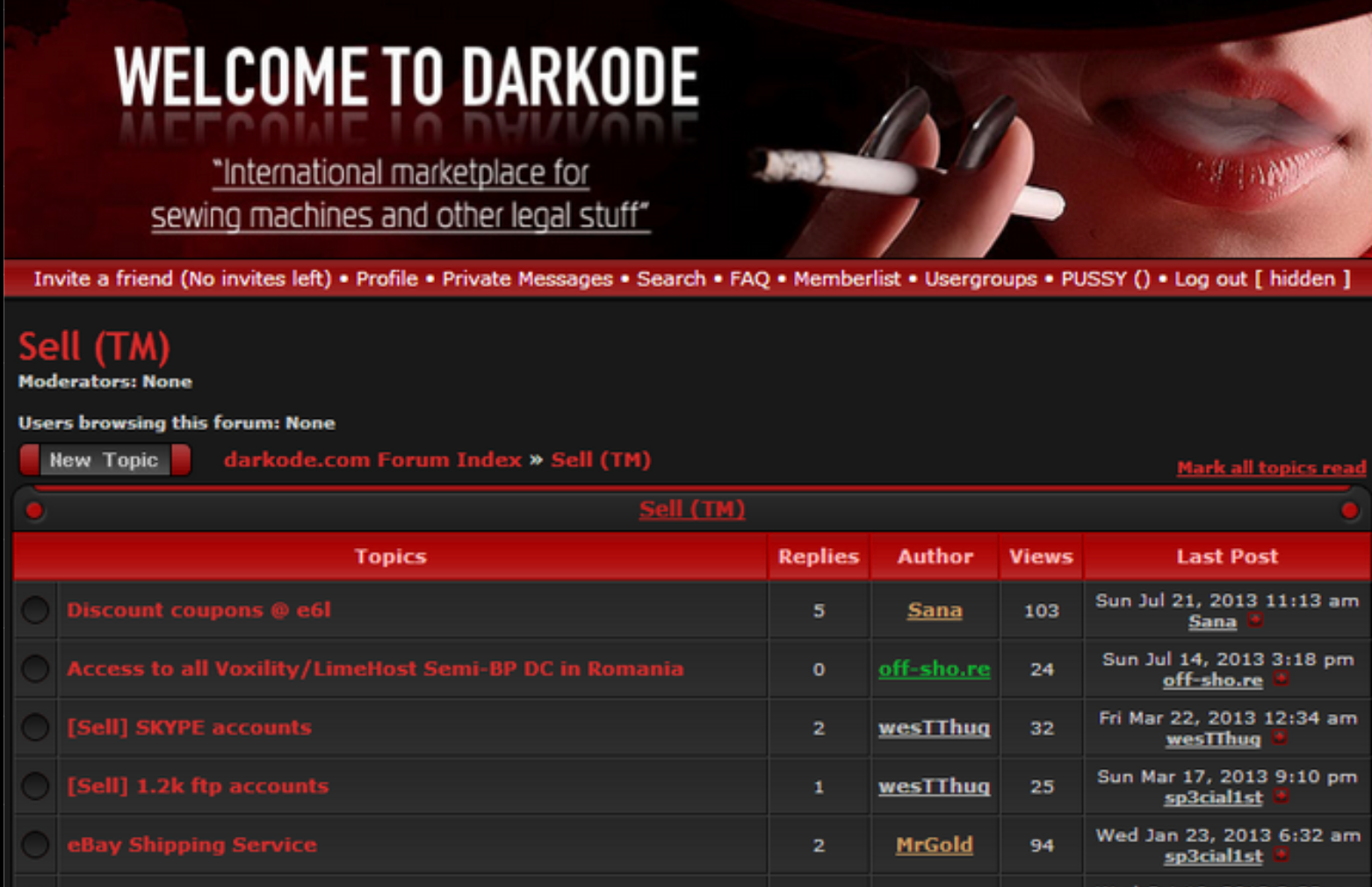
One of the earliest and most influential hubs was Dark0de, a notorious English-language hacking forum that gained prominence as a marketplace for trading stolen data, hacking tools, and illicit services. However, in 2015, law enforcement agencies conducted a major takedown of Dark0de, disrupting this community and scattering its members across the cybercriminal underground.
Following Dark0de’s demise, many of its more technically skilled users migrated to a new forum founded that same year: RaidForums.
While forums like Dark0de and RaidForums provided the infrastructure and technical marketplace, the mid-2010s saw the emergence of the first high-profile, English-speaking threat groups that mastered the art of public spectacle. The most notorious of these was Lizard Squad, a collective that operated between 2014 and 2016. Their chaotic, high-visibility DDoS campaigns against gaming networks, combined with their pioneering of the "DDoS-for-hire" model, served as a direct precursor to the tactics that would later be refined by groups like Lapsus$. Lizard Squad's story is a foundational case study in the shift from forum-based activity to brand-name cybercrime.

LizardSquad was a notorious black hat hacking collective that operated primarily between 2014-2016, achieving international notoriety through high-profile DDoS attacks against gaming networks and major corporations. The group gained infamy for disrupting PlayStation Network and Xbox Live on Christmas Day 2014, affecting millions of gamers worldwide. Following extensive law enforcement operations, key members were arrested and prosecuted, with the group eventually dissolving as its leadership faced imprisonment and legal consequences.
LizardSquad emerged in September 2014, initially announcing its formation only to claim disbandment shortly after, before returning to claim responsibility for various high-profile attacks. The group participated in the Darkode hacking forums and shared hosting infrastructure with other cybercriminal organizations. The collective operated as a loose network of primarily teenage hackers from various countries, including Finland, the UK, the Netherlands, and the United States.
Beyond their technical impact, the true legacy of groups like Lizard Squad and their contemporaries, such as HOICSquad, was the establishment of the "leak-and-brag" culture as a core tenet of the ecosystem. For these actors, the attack itself was only part of the operation; the other half was the performance. By publicly claiming responsibility on social media, taunting their victims, and engaging with the media, they transformed disruption into a form of entertainment and a tool for building notoriety. This tactic of leveraging public spectacle to amplify an attack's impact is a direct cultural ancestor to the public extortion models employed by modern COM groups. The taunts of Lapsus$ and the theatrical data dumps of ShinyHunters are a direct evolution of the same impulse: weaponizing notoriety to pressure victims and build a reputation in the underground
The group's most infamous operation occurred on Christmas Day 2014, when LizardSquad launched simultaneous DDoS attacks against both PlayStation Network and Xbox Live. The attack affected approximately 110 million PlayStation Network subscribers and 48 million Xbox Live users, disrupting gaming services during peak holiday hours.
Xbox Live was restored within 24 hours, but PlayStation Network experienced extended outages that prevented both existing and new users from accessing online features. The attacks were reportedly halted after Kim Dotcom negotiated with the group, offering 3,000 premium MegaPrivacy vouchers valued at approximately $300,000 in exchange for ending the attacks.
Monetization Strategy
Following their Christmas attacks, LizardSquad commercialized their operations by launching "Lizard Stresser," a DDoS-for-hire service. The service was marketed as a stress-testing tool but functioned as a cyberattack platform, with packages ranging from $19.99 to $200 for monthly access. The service offered attack durations of 20 to 60 minutes and included additional features such as IP spoofing and DNS/NTP amplification capabilities.
The group's business model represented a shift from attention-seeking attacks to profit-driven cybercrime, with some members later forming additional groups like PoodleCorp to continue similar operations.
Key Members and Leadership
Note : Vinnie is still active on social media and still carries a huge reputation among “THE COM” and allegedly educates people.
Law Enforcement Response and Arrests
The international nature of LizardSquad's operations triggered coordinated law enforcement responses across multiple jurisdictions. The group's members were systematically identified and arrested through various investigative techniques.
Investigation Techniques
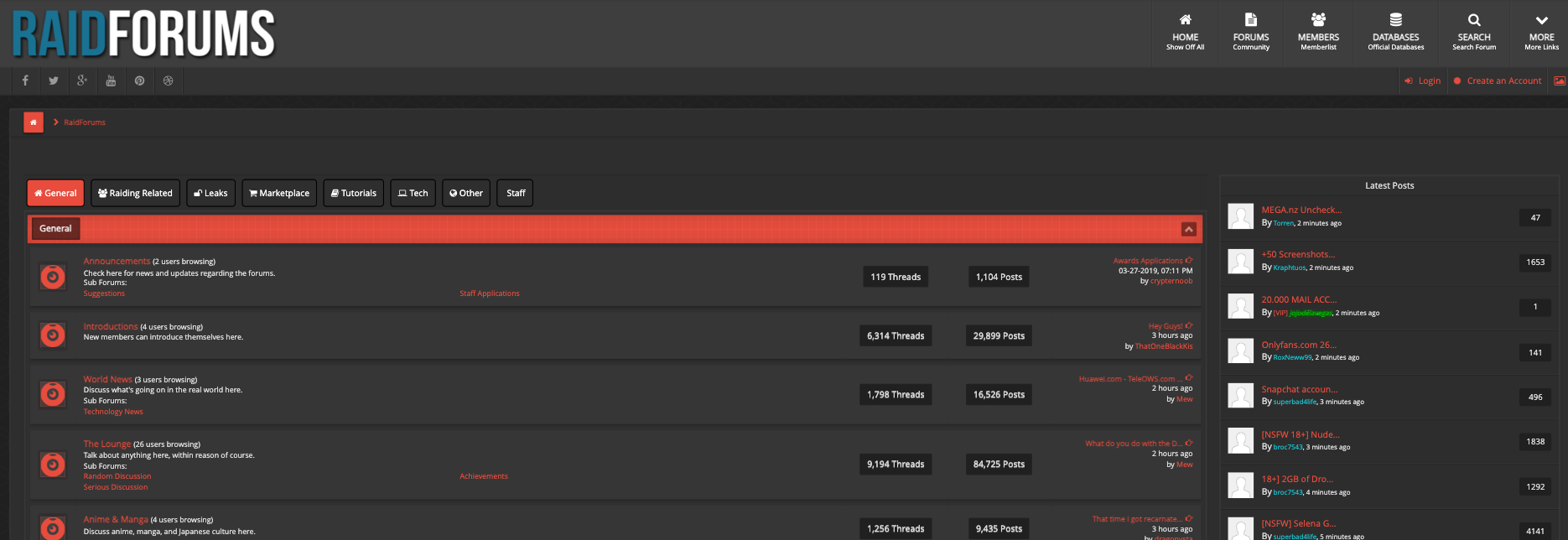
Initially, RaidForums started as a gathering place for “twitch raiders” and internet trolls but quickly evolved into a sophisticated marketplace centered around data breaches, database exploits, credential stuffing, and malware development. The forum became a breeding ground for technical hackers and cybercriminals seeking to trade stolen data and hacking tools, steadily gaining influence in the underground ecosystem. RaidForums was founded by a young Portuguese hacker known by the pseudonym “Omnipotent,” and over time, it grew into one of the most prominent English-language hacking forums, until it was seized and shut down by law enforcement in 2022.
Parallel to the rise of RaidForums, another influential community emerged: OGUsers, founded in 2017. Initially, OGUsers served as a marketplace for trading rare and highly sought-after social media usernames known as “OG” (original gangster) handles on platforms like Twitter, Tiktok, Telegram and Instagram. These short, brandable usernames carried significant value, sometimes selling for thousands of dollars.

However, the community quickly evolved beyond simple trading. Users began employing social engineering tactics to steal valuable handles, initially targeting individual account holders. Over time, these methods expanded to include the manipulation of employees at social media platforms, gaining unauthorized access to internal tools and admin panels. One such insider-enabled breach led to the now-infamous series of Twitter account hijackings.
The trajectory of this burgeoning ecosystem was supercharged by the cryptocurrency boom of 2020-2021. This period introduced both a highly lucrative new target class digital currency wallets and a streamlined, pseudo-anonymous mechanism for monetization and laundering. The focus of many actors shifted dramatically; SIM-swapping and account takeover techniques, once perfected for stealing social media handles, were now repurposed to drain cryptocurrency accounts holding millions of dollars. Consequently, the role of OG usernames also transformed. No longer just status symbols, they became instrumental assets for money laundering; stolen crypto was used to purchase valuable handles, which were then resold for clean currency, effectively breaking the chain of illicit transactions. This economic catalyst marked a critical inflection point, professionalizing the community’s motivations and setting the stage for the more audacious, financially-driven operations that would soon follow.
A new class of social engineers, often referred to as “callers/texters,” became central to these operations. Using scripted pretexts and psychological manipulation, callers deceived telecom and platform support staff to execute SIM swaps and account takeovers.
Their targets included high net-worth cryptocurrency holders, influencers, executives, and celebrities. The techniques pioneered during this era would go on to form the backbone of the enterprise-level social engineering attacks seen today.

It is important to note the origins of the COM can be traced back particularly to OGUsers Era. This forum fostered a strong sense of community and belonging among its members, where participants felt part of something larger than just transactions. This shared identity and reputation culture became a defining feature of cybercriminal marketplaces and helped shape the social dynamics that underpin today’s underground economy.

There was considerable overlap between the user bases and tactics employed on both forums, particularly as cybercriminals sought new venues following the takedowns of older carding and hacking forums. RaidForums became known for its technical hacking and data markets, while OGUsers carved out a niche in social engineering and account hijacking. Together, these forums fostered a cybercriminal supply chain by providing platforms to build skills, establish reputation, and trade illicit goods and services, shaping much of the English speaking cybercrime landscape seen today.
As The COM matured into a fragmented yet highly collaborative ecosystem, it gave rise to several specialized subgroups that significantly elevated the scale and visibility of cybercrime operations. Among the most prominent were Lapsus$ and ShinyHunters, each embodying different facets of The COM’s evolution ranging from chaotic public-facing breaches to quiet, methodical data exfiltration campaigns.

Formed in mid-2020 by experienced actors from the RaidForums scene, ShinyHunters quickly distinguished themselves through their adoption of industrial-scale attack methodologies. Among the first groups to operationalize a combination of automated SQL injection, API abuse, Github takeovers, and credential harvesting, ShinyHunters moved well beyond the traditional focus on OG username trading. Their targets rapidly expanded to include large consumer platforms, SaaS providers, and enterprise environments.
ShinyHunters helped define the “leak-and-brag” ethos, gaining widespread media attention by publicly dumping massive datasets from high-profile breaches including Tokopedia, Microsoft, Nitro PDF, and others. These high-volume leaks were not only designed to monetize stolen data but also to bolster the group’s reputation across underground forums and public platforms.
In addition to direct breaches, ShinyHunters played a key role in the commercialization of cybercrime by acting as one of the first consumer-facing hubs for Initial Access Brokers (IABs). They operated within a broader ecosystem of “as-a-service” offerings leveraging shared infrastructure, credential marketplaces, and collaboration with other specialized groups. This modular, service-based approach helped establish a repeatable model for mid- to high-tier cybercriminal operations, many of which still emulate their tactics today.

Lapsus$ emerged on Telegram in late 2021, quickly gaining notoriety as a disruptive, publicity-driven threat group composed largely of teenage actors from the English-speaking world. Despite their seemingly chaotic structure and informal communications, Lapsus$ demonstrated a high degree of technical capability and operational effectiveness—successfully compromising high-profile organizations including NVIDIA, Samsung, Microsoft, and Twitter.
The group became infamous for its bold tactics: hacking livestreams, public data leaks, extortion threats, and direct taunts aimed at victims and law enforcement. Yet beneath the spectacle was a disciplined approach to human-centric intrusion techniques. Lapsus$ primarily leveraged social engineering, SIM-swapping, credential theft, and the manipulation of customer support and IT staff to gain unauthorized access to privileged systems. These techniques enabled the group to sidestep conventional security controls and pivot deep into target networks.
Lapsus$ was composed of skilled members with roots in both OGUsers and RaidForums. Many began as social engineers on OGUsers, building reputations through account takeovers and SIM-swapping schemes. As law enforcement pressure intensified on OGUsers, several actors migrated to RaidForums, where they encountered a more technically advanced ecosystem centered on data breaches, exploit sharing, and access brokerage. The fusion of social engineering expertise from OGUsers and breach-oriented tactics from RaidForums laid the foundation for Lapsus$—a hybrid threat group reflective of The COM’s convergence-driven evolution.
Despite a wave of arrests in March 2022, Lapsus$'s techniques and aggressive ethos had already influenced a broader shift in the cybercrime landscape. Their success inspired a generation of copycat actors and seeded new collectives that adopted more operationally secure, decentralized structures, while continuing to use the aggressive, high-visibility tactics that Lapsus$ had pioneered.
Between 2021 and 2023, the English-speaking cybercriminal underground experienced its most significant disruption to date. Coordinated law enforcement takedowns, combined with high-profile arrests of teenage hackers, fundamentally reshaped the digital threat landscape. These operations highlighted unprecedented international cooperation and disrupted platforms that had collectively hosted over 500,000 active users.
One of the most pivotal cases during this period was the arrest of Arion Kurtaj, an 18-year-old from Oxford, UK. Known online as "White," "Breachbase," "WhiteDoxbin," and "TeaPotUberHacker", Kurtaj orchestrated breaches of some of the world’s most prominent tech companies, including NVIDIA, Microsoft, Uber, and Rockstar Games.
Kurtaj began his cybercrime career in 2021 with attacks on BT Group and EE, demanding £4 million through sophisticated social engineering campaigns. Diagnosed with autism, he was deemed unfit to stand trial. Instead, UK courts focused on whether he committed the acts, rather than proving criminal intent. His case established important legal precedents around the prosecution of neurodivergent individuals in cybercrime.
The most dramatic incident occurred in September 2022, when Kurtaj, under police protection at a Travelodge hotel, used a hotel TV, Amazon Fire Stick, and a mobile phone to infiltrate Rockstar Games and leak footage of the unreleased Grand Theft Auto VI. This bold act led to his indefinite detention in a secure psychiatric facility.
LAPSUS functioned more as a loosely organized international collective than a traditional cybercrime syndicate. Co-conspirators were arrested in Brazil, the UK, and the US, revealing a wide operational footprint. In Brazil, Operation Dark Cloud exposed LAPSUS$’s infiltration of government systems, including the Ministry of Health.
The group’s operational model relied heavily on social engineering, SIM swapping, and insider recruitment. They also used public Telegram polls to select targets, blending spectacle with effective intrusion tactics.
Despite their youth, LAPSUS$ members demonstrated capabilities rivaling nation-state threat actors. Their attacks disrupted companies with some of the most mature security operations in the world. The group's behavior reflected non-financial motives as well—status, recognition, and peer influence were recurring drivers.

On February 4, 2021, at 1:00 PM PST, a rare coordinated takedown by Instagram, Twitter, TikTok, and other platforms targeted OGUsers, the premier forum for trading stolen social media accounts and coordinating SIM-swapping attacks.
Instagram and Facebook led the charge, disabling hundreds of accounts linked to OGUsers and issuing cease and desist letters. Twitter followed by banning high-follower "OG" handles hijacked during the July 2020 Twitter breach. TikTok recovered dozens of unique usernames, many acquired through fraudulent means.
This joint action marked a paradigm shift from isolated enforcement to industry-wide cybercrime disruption.
OGUsers was the central hub for SIM-swapping attackers and digital identity thieves. The platform’s status economy rewarded those who could hijack rare usernames, high-profile accounts, and cryptocurrency wallets. Its members targeted influencers, executives, and celebrities using advanced vishing, phishing, and insider exploitation.
By revoking access, recovering hijacked accounts, and improving verification protocols, platforms disrupted the illicit value chain that sustained OGUsers' marketplace. Multi-factor authentication, improved support staff training, and better fraud detection significantly reduced the effectiveness of these attacks.
Law enforcement intelligence sharing further amplified the effort, setting a precedent for private-public collaboration in disrupting digital criminal infrastructure.
The seizure of RaidForums was the culmination of a multi-agency operation initiated in 2018, when federal agents detained Diogo Santos Coelho ("Omnipotent") at Hartsfield-Jackson Airport in Atlanta. Forensic analysis of his devices exposed his direct connection to RaidForums, including registration of backup domains like rf.ws and raid.lol.
RaidForums operated with a tiered membership model, complete with a "God" status and escrow services. Coelho personally operated a fee-based “Official Middleman” system that facilitated data sales and credential transfers documented through FBI undercover purchases.

On January 31, 2022, Coelho was arrested in Croydon, UK, followed by a coordinated seizure of all RaidForums infrastructure on February 25, 2022. Operation Tourniquet involved the FBI, NCA, Europol, and law enforcement agencies from Portugal, Romania, and Sweden.
Law enforcement seized all known domains and replaced them with banners displaying criminal charges marking a decisive public message about the risks of cybercrime participation.
Coelho’s extradition has since become a complex legal issue, with both the US and Portugal filing competing requests. In September 2025, the UK High Court ruled that procedural errors had compromised the decision-making process, requiring reconsideration. The case has since set new precedents in multi-jurisdictional cybercrime prosecutions.
By 2021–2022, after multiple high-profile hacks against the forums and law enforcement takedowns, the COM (criminal online marketplace) ecosystem no longer relied on any single platform. While many users initially migrated to RaidForums, core COM activity shifted toward decentralized platforms such as Telegram and Discord. The ecosystem evolved into a mesh of invite-only forums, temporary marketplaces, and encrypted communication channels. This decentralization enhanced user anonymity but reduced coordination efficiency and centralized oversight.
Following RaidForums’ takedown, over 500,000 displaced users sought refuge primarily on Telegram. However, language barriers and geopolitical tensions, especially anti-Russian sentiment due to the Ukraine invasion, limited movement to Russian-speaking forums. The absence of a centralized English-speaking hub created a power vacuum. Temporary platforms, including low-security forums and Discord servers, emerged but failed to replicate RaidForums’ robust infrastructure, reputation systems, or escrow services.
On March 16, 2022, Conor Brian Fitzpatrick, known as “Pompompurin,” launched BreachForums—a near-clone of RaidForums. The platform rapidly grew from 1,500 to over 192,000 users within eight months. Fitzpatrick’s notoriety, particularly from the 2021 FBI email hack, attracted high-value actors and helped bridge OGUsers’ social engineering community with RaidForums’ data breach-focused user base. BreachForums quickly became a defining hub in the modern COM landscape.

The convergence of OGUsers and RaidForums communities, catalyzed by successive takedowns, reshaped the COM ecosystem. Social engineers who specialized in OG account takeovers adapted to a marketplace rich with leaked data and credentials. Techniques like bypassing two-factor authentication, SIM swapping, and manipulating support agents merged with data breach operations. This fostered hybridization of skills and the development of underground reputation systems. COM actors expanded their targets from individual social accounts to enterprises and crypto platforms. Professionalized services such as callers, doxers, and exploit developers became common, with operations coordinated over Telegram, Discord, and private channels.
Despite BreachForums’ rapid growth, not all actors migrated there. A significant portion of the COM, especially those involved in SIM swapping, crypto fraud, and related activities did not join BreachForums. The platform’s strict rules against financial fraud discouraged many from participating publicly. Instead, these actors remained active on Telegram, Discord, and private networks. This was true not only for prominent groups like ShinyHunters but also for many smaller actors and entire fraud circles that chose to operate underground or on alternative platforms. ShinyHunters, for example, maintained control behind the scenes but distanced themselves publicly by delegating BreachForums’ day-to-day administration to IntelBroker, keeping a low profile while holding influence.
This divide meant that while BreachForums served as a central hub for data breach trading and infosec discussions, it never fully replaced the broader fraud forums that had existed previously. Much of the old COM community either fragmented further or remained hidden in private channels.
After Fitzpatrick’s arrest in March 2023, BreachForums cycled through a series of administrators including Baphomet, ShinyHunters, IntelBroker, and Anastasia each making changes under pressure. Domain seizures and internal instability eroded user trust, accelerating the community’s move toward fragmented, semi-private ecosystems. Access to key spaces became increasingly reputation- or referral-based, further compartmentalizing the landscape.
This fragmentation of the underground ecosystem, coupled with the absence of centralized, public-facing forums, has contributed to the rise of numerous UNC-designated threat clusters that often operate below the radar of mainstream infosec reporting.
Without consistent visibility, formal naming conventions, or public TTP sharing, many of these groups function in relative isolation. Their campaigns appear as disjointed, anomalous incidents, making it difficult for researchers to recognize them as part of a larger, coordinated threat model. This creates significant blind spots for defenders, particularly when overlapping infrastructure or techniques are obscured by intermediary service providers (phishing kits, vishing crews, IABs, etc.).
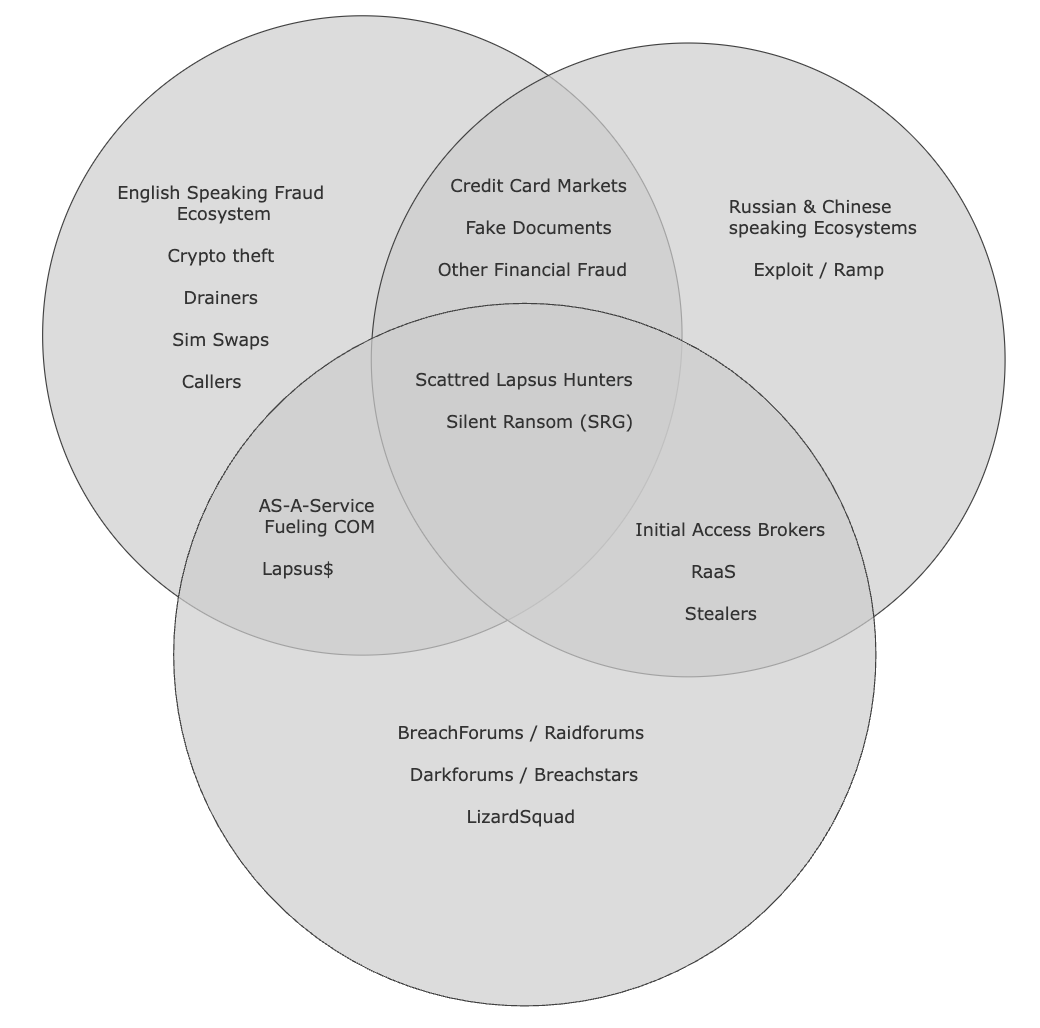
Some notable examples of these loosely or semi-affiliated groups include:


Formed in mid-2025, Scattered Lapsus$ Hunters is a newly emerged cybercrime coalition that represents a strategic consolidation of capabilities from three of the most notorious threat actors within the COM ecosystem: Scattered Spider, Lapsus$, and ShinyHunters. Unlike previous short-term collaborations, this group appears to operate as a more structured alliance. Their public debut occurred via Telegram, where they engaged in high-visibility data leaks, victim extortion, and public taunts directed at both cybersecurity firms and law enforcement echoing Lapsus$’s signature tactics.
Allegedly, the group comprises not only English-speaking members but also individuals fluent in Russian and Chinese, indicating a more globally distributed network. These members are believed to operate in loosely coordinated cells and maintain connections to multiple financially motivated cybercriminal groups. However, the group reportedly takes active measures to obscure these affiliations including efforts to keep internal structures private and the deliberate dissemination of misinformation to conceal ties to Russian and Chinese-speaking actors. The formation of Scattered Lapsus$ Hunters underscores an emerging trend of increased collaboration and professionalization within the cybercrime ecosystem, paired with greater operational security and deception tactics.
Scattered Lapsus$ Hunters is guided by a “log in, not hack in” philosophy, privileging identity‑centric intrusion and bypassing traditional defenses by targeting human trust. Their methodology is a synthesis of the constituent groups’ specialties:
This blend of social engineering, wholesale exfiltration, and performative extortion makes them especially volatile and unpredictable.

Since launching, Scattered Lapsus$ Hunters has claimed responsibility for several major attacks:
In late September 2025, the group’s public-facing channels posted farewell messages, announcing a “going dark” phase. But most analysts and law enforcement view this as a tactic, not a genuine shutdown. The procedure resembles strategies used by ransomware and other threat actors to deflect public scrutiny, regroup, rebrand, or continue operations under the radar. While outward activity has quieted, private extortion against undisclosed victims appears to persist.
What truly distinguishes The COM from prior cybercriminal eras is its modular specialization and supply-chain integration, mirroring the efficiency and structure of legitimate industries. The ecosystem has matured into a cybercrime-as-a-service (CaaS) model where few actors operate entirely independently.Threat actors form transactional micro-economies, each playing a defined role in a seamless, high-functioning apparatus.
This structure emphasizes the interdependence within the cybercrime economy and reinforces how The COM has evolved beyond disorganized criminality into a professionalized, service-driven industry. These roles are modular and interchangeable, allowing criminal operations to scale quickly, outsource risk, and remain resilient under pressure.
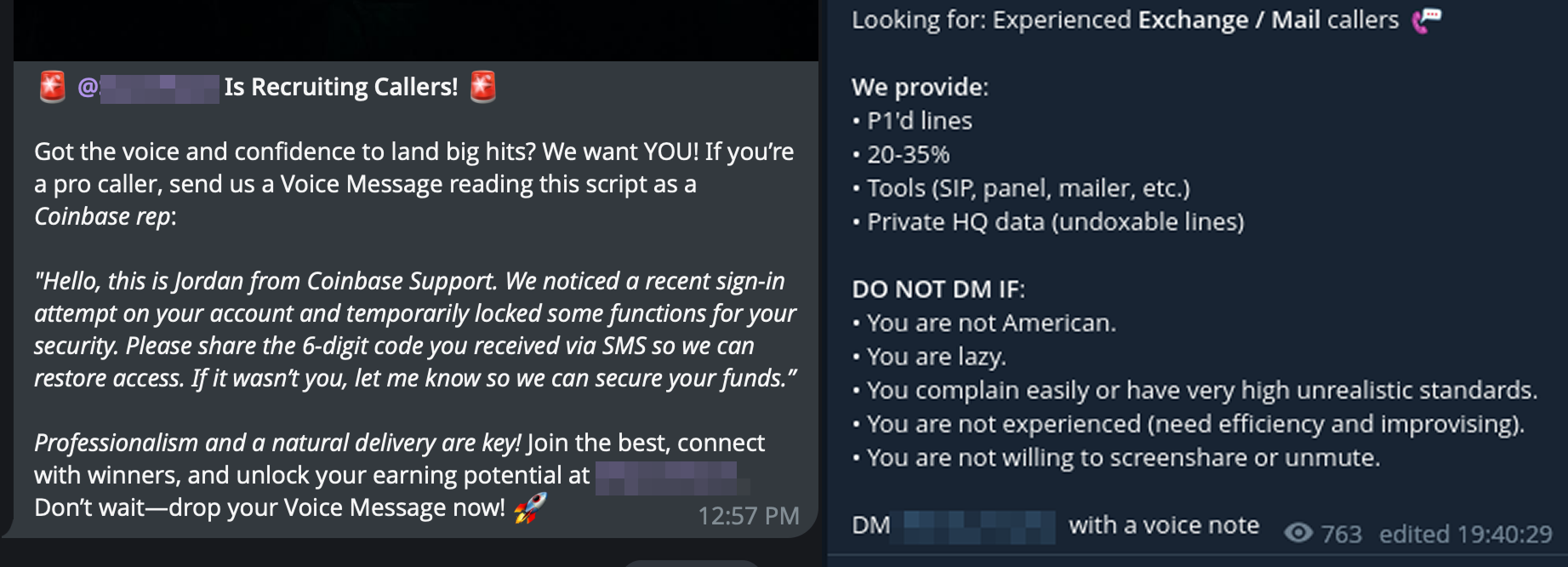
1. Callers
Social engineering specialists who engage in live voice phishing (vishing). These operators impersonate internal IT staff, telecom providers, or corporate help desks to extract credentials, reset passwords, and facilitate SIM swaps. They are instrumental in breaching multi-factor authentication (MFA) barriers.
2. Texters / Spammers
Operators behind high-volume SMS phishing (smishing) and vishing campaigns. Often backed by botnets or bulk SMS APIs, they blast phishing lures to tens of thousands of targets. Their goal: initial credential harvesting or directing victims to phishing sites controlled by downstream actors.

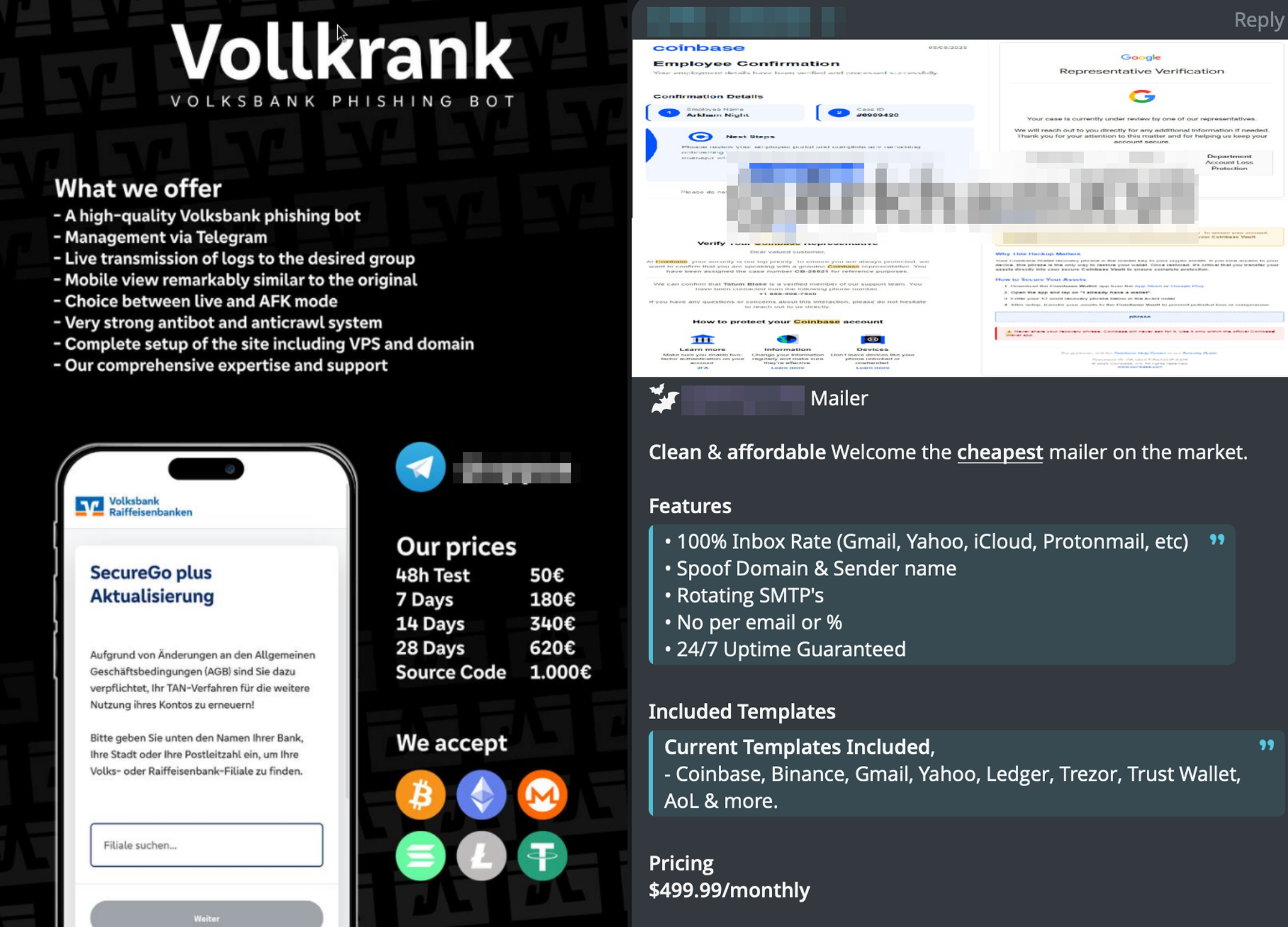
3. Phishing Kit Developers
Technical developers who create turnkey phishing kits, often spoofing login portals for major platforms (Google Workspace, Microsoft 365, banking apps). These kits frequently integrate real-time MFA grabbers or session cookie stealers, enabling attackers to bypass two-factor authentication entirely.
4. SIM Swappers
Actors who hijack phone numbers to intercept password resets, OTPs, or 2FA tokens. They operate through:
5. Initial Access Brokers (IABs)
Specialists who obtain and validate access to corporate environments, including:
They monetize this access by selling to ransomware groups, drainer crews, or data extortionists.

6. Doxers / OSINT Teams
Information brokers who build deep victim profiles using both open-source intelligence (OSINT) and breached data. These profiles inform tailored social engineering campaigns and enhance the success rate of phishing, vishing, and SIM-swapping attacks.

7. Ransomware-as-a-Service (RaaS) Affiliates
Operators who weaponize access sold by IABs. After gaining entry, they deploy ransomware, exfiltrate sensitive data, and launch multi-phase extortion campaigns. Many of these actors are linked to groups like LockBit, Cl0p, or splinter cells from Conti.
8. Crypto Launderers
Financial enablers who obscure the movement of illicit funds. They offer:
9. Drainers
Technical teams that develop and deploy wallet-draining scripts, often embedded in:
These operations have drained hundreds of millions in digital assets across DeFi ecosystems.
This structure emphasizes the interdependence within the cybercrime economy and reinforces how The COM has evolved beyond disorganized criminality into a professionalized, service-driven industry. These roles are modular and interchangeable, allowing criminal operations to scale quickly, outsource risk, and remain resilient under pressure.
The as-a-service model fueling The COM makes traditional IOC-based detection IP addresses, malware hashes, domain blacklists largely ineffective for the following reasons:
The October 2025 law enforcement seizure of the iteration of BreachForums triggered the latest evolutionary phase of the Cybercrime Operations Market (COM). This disruption did not eliminate the marketplace but instead catalyzed a bifurcation, leading to a new hierarchy within the English-speaking underground and an unprecedented convergence with established Russian-speaking forums.
In the immediate aftermath of the takedown, displaced users scattered across various platforms. However, a clear two-tiered system has since emerged:
This forum has rapidly consolidated its position as the primary, reputation driven successor to BreachForums. Its legitimacy is bolstered by intelligence suggesting the platform is operated by, or with the approval of, actors closely affiliated with the ShinyHunters collective. This connection lends it immediate credibility, attracting experienced threat actors, high-value data brokers, and the core community from the previous forum.

Serving as a secondary marketplace, DarkForums has become the de facto destination for newer or less-established actors. While active, it lacks the robust reputation systems, exclusive databases, and high-level discourse that characterize BreachStars positioning it as a more transactional, lower-tier platform.

Perhaps the most significant strategic development in the post-BreachForums era is the migration of a notable contingent of high-value, English-speaking threat actors to established Russian-language forums particularly Exploit[.]in.
Historically, these ecosystems operated in parallel, separated by significant linguistic and cultural barriers. However, analysis of activity in 2025 indicates a paradigm shift. Exploit[.]in’s administrators and veteran user base are now actively accommodating and integrating key service providers from the COM.
Observed developments include:
This East–West convergence represents a dangerous maturation of the cybercrime ecosystem. It grants English-speaking actors access to a more operationally secure and technically advanced marketplace, including sophisticated malware, zero-day exploits, and robust money-laundering networks.
For defenders, the implications are clear:
the boundaries between financially motivated threat groups are eroding. The result is a new generation of hybrid adversaries blending linguistic, cultural, and technical capabilities into a more diverse and potent set of offensive tools.
Conclusion: The Human Perimeter Is the New Frontline
The story of the English-speaking cybercriminal ecosystem is one of relentless adaptation. What began as a community for trading social media handles has evolved into a service driven economy powering some of today’s most damaging cyberattacks. From OG Users to the hybrid threat of Scattered Lapsus$ This is not merely a chronicle of forums and actors, it is the story of how social engineering was professionalized and scaled into the single greatest threat to modern enterprises.
The central conclusion is unavoidable: technology-centric security has failed to keep pace. The COM operates on a simple truth. It is easier to compromise a person than a device. Its “as-a-service” ecosystem is designed to exploit this weakness, exposing the limits of architectures that neglect the human element. The era of treating social engineering as a low-level threat is over; it is now the primary vector for enterprise compromise.
The future of this threat lies in the ongoing convergence of Western social engineering specialists with Eastern European syndicates on platforms like Exploit[.]in creating hybrid adversaries with unprecedented reach and sophistication. In this reality, effective security is not about building higher walls, but building resilience from the inside out.
Organizations that fail to pivot from network defense to identity-centric security, from legacy MFA to phishing-resistant controls, and from awareness training to robust protection for high-value personnel will remain prime targets for this ever-evolving ecosystem. The frontline has moved. It’s time our defenses did as well.