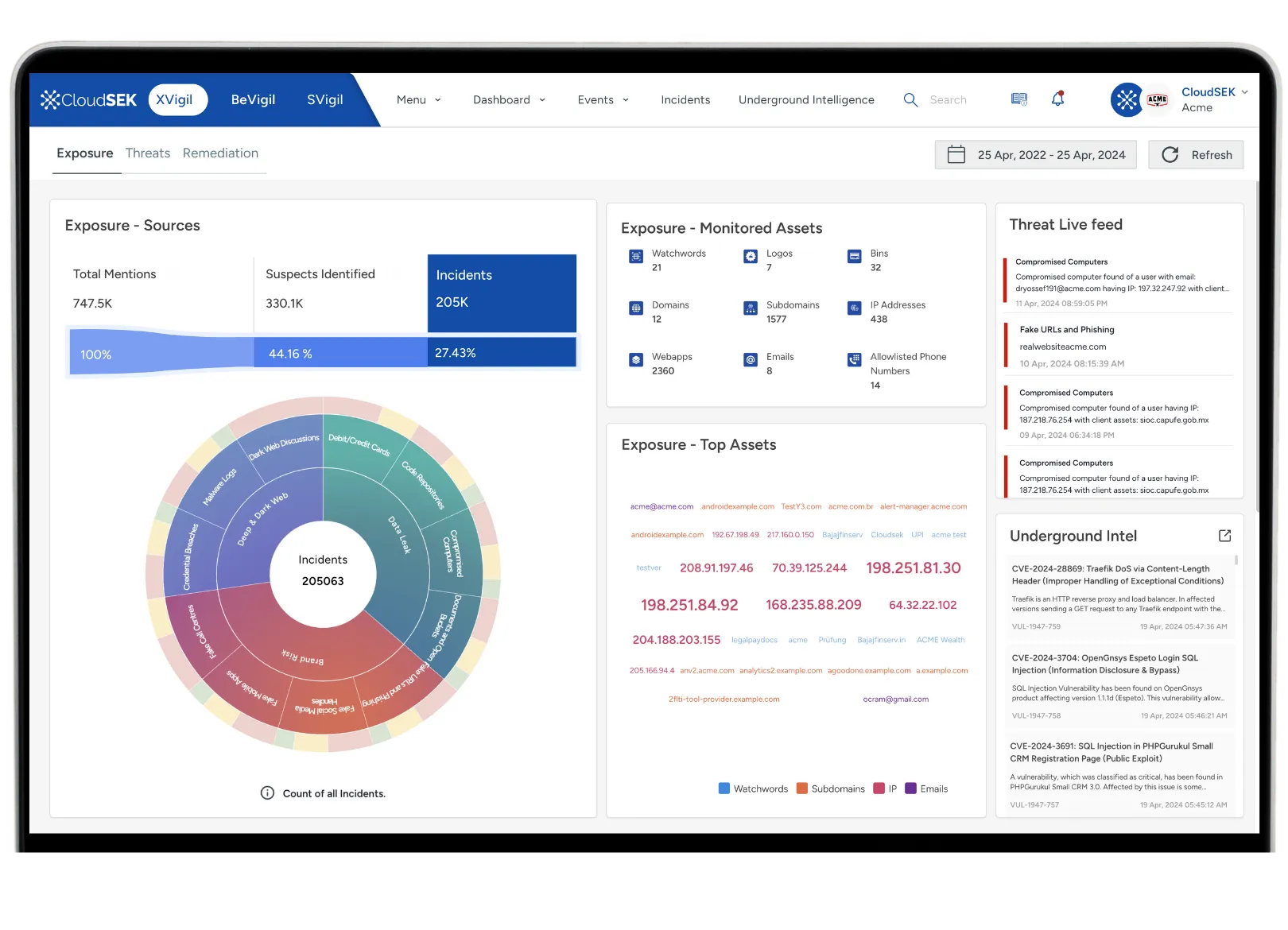
In a digital world where threats evolve daily, your business needs a shield against unseen dangers. Learn how our Digital Risk Protection (DRP) solutions offer comprehensive monitoring and defence against digital threats. Transform your online presence into a fortress with our innovative strategies.








CloudSEK stops the Kill Chain by predicting and preventing Initial Access Vectors
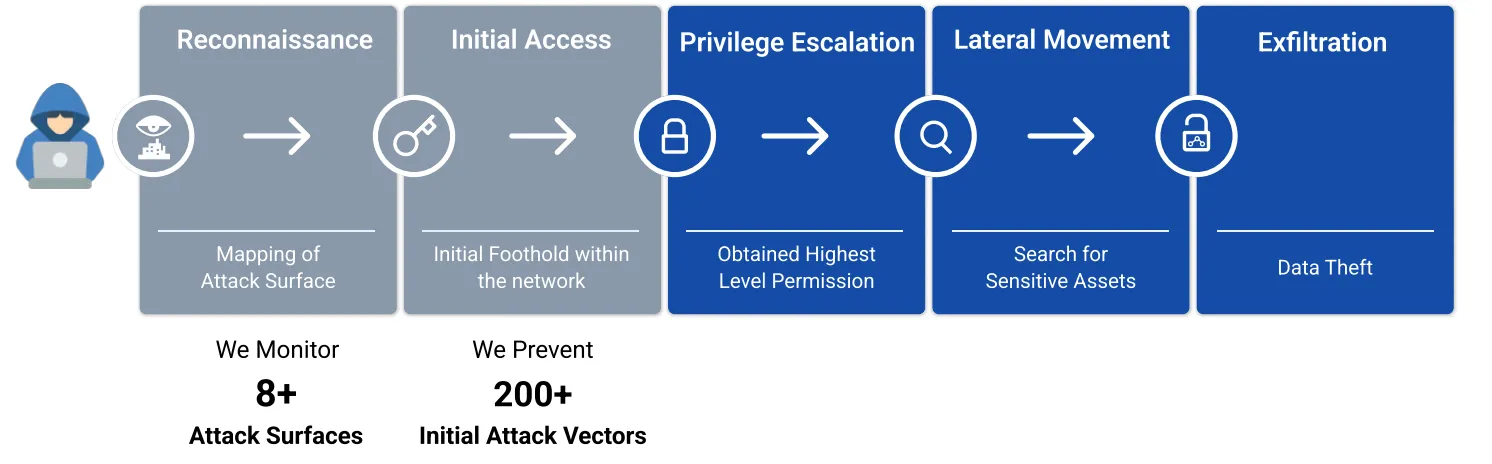
Threat actors are constantly evolving their methods. Off late, cyber threat researchers are observing that attackers spend considerable time on reconnaissance - scoping out the weakness in an organization's attack surface - whether it is an outdated infrastructure asset or weak password policies. Once they determine the angle of attack, they are able to gain access and wreak havoc inside.
Hence, it is absolutely necessary that the attackers are stopped before they can gain initial access within the network.
CloudSEK stops the kill chain attackers follow even before they can gain an initial foothold within the network. We do this by mapping customers' attack surfaces and all IAVs commonly used by threat actors. Killing the IAV would prevent a cyber threat from happening.
At CloudSEK, we combine the power of Cyber Intelligence, Brand Monitoring, Attack Surface Monitoring,
Infrastructure Monitoring and Supply Chain Intelligence to give visibility and context to our customer's IAVs.
Modules that are designed to protect organization's external attack surface
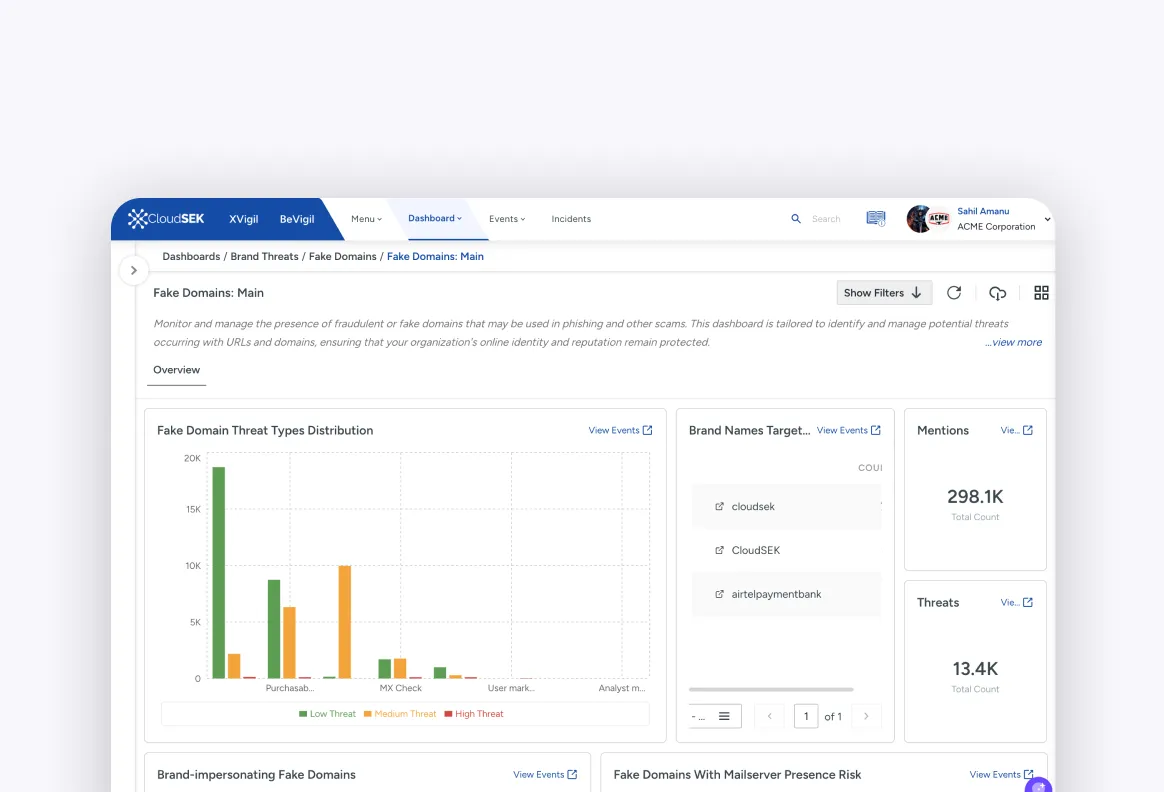
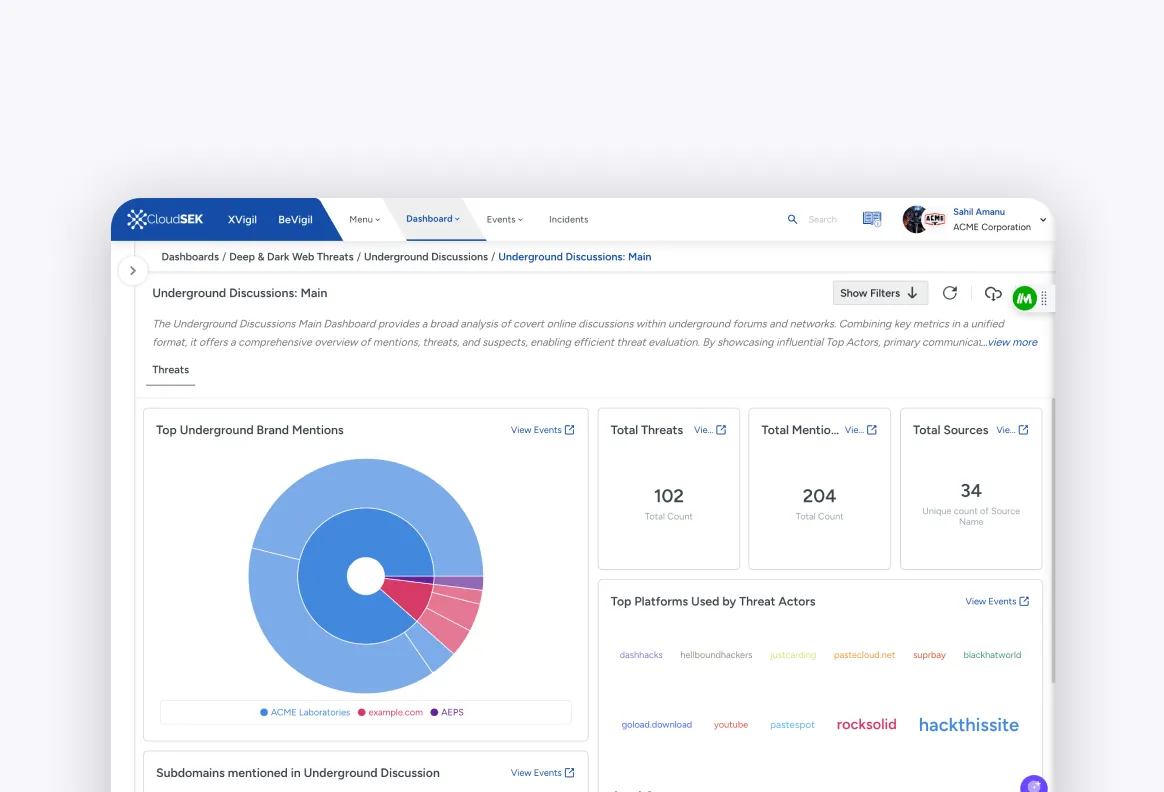
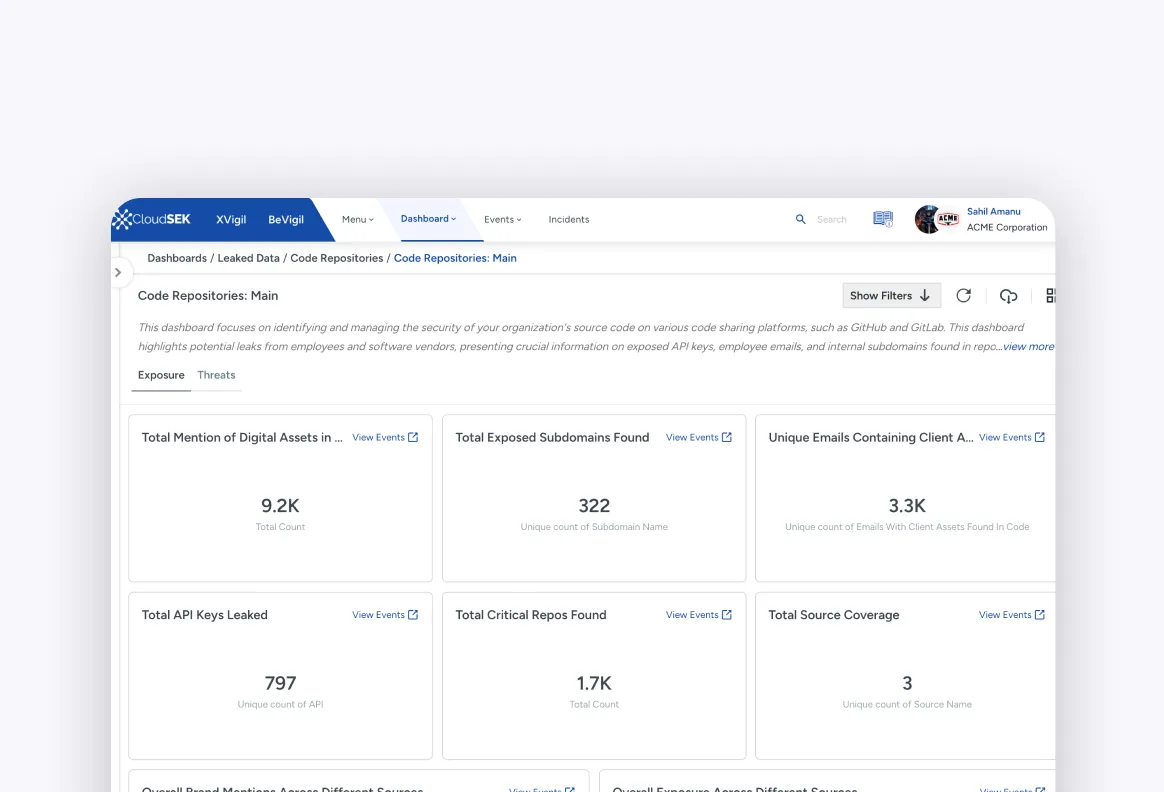
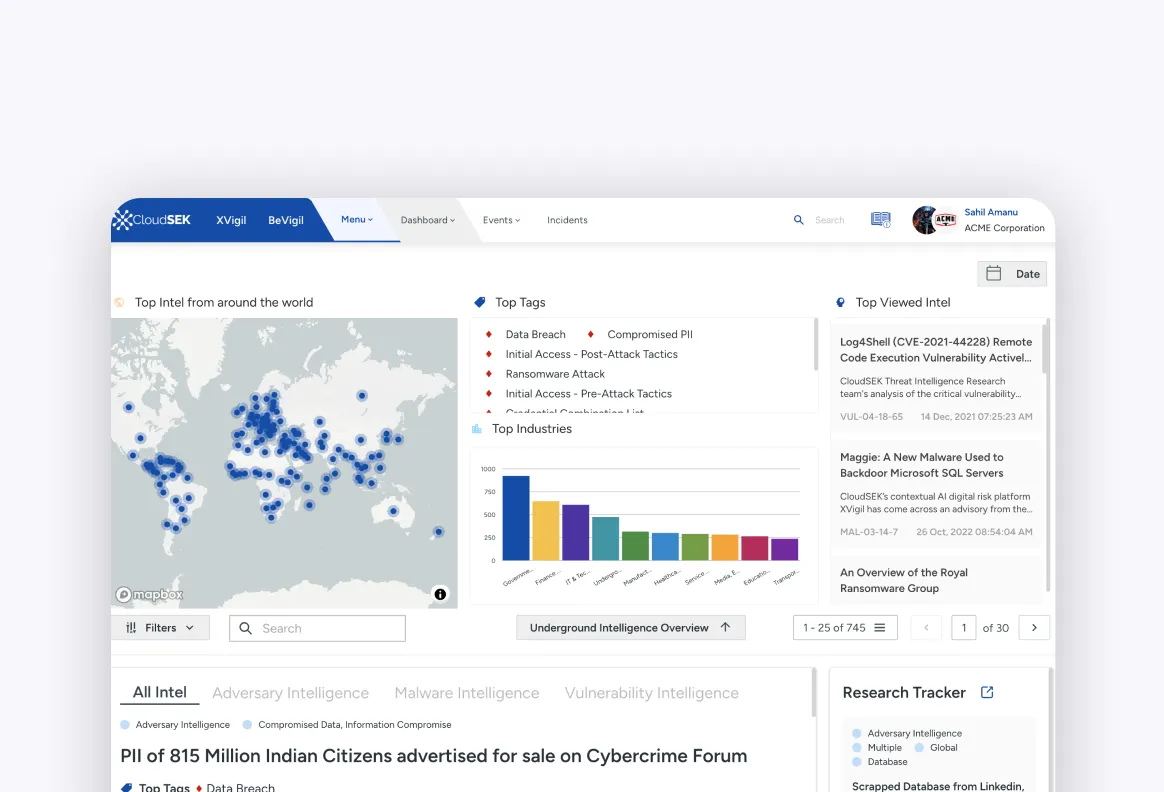
Understand how you can leverage the CloudSEK platform to combat external threats and secure your business against Cyber Threats, Sensitive Data Leaks, Fraud, Scam and more.