🚀 CloudSEK has raised $19M Series B1 Round – Powering the Future of Predictive Cybersecurity
Read more




The CloudSEK Threat Research Team discovered a generic phishing page that can impersonate any brand using a generic login page to steal credentials. The phishing page is hosted using Cloudflare's workers.dev, a free domain name service.
1. The generic looking phishing page is hosted on this URL: workers-playground-broken-king-d18b.supermissions.workers.dev which is designed to steal credentials from unsuspecting victims.

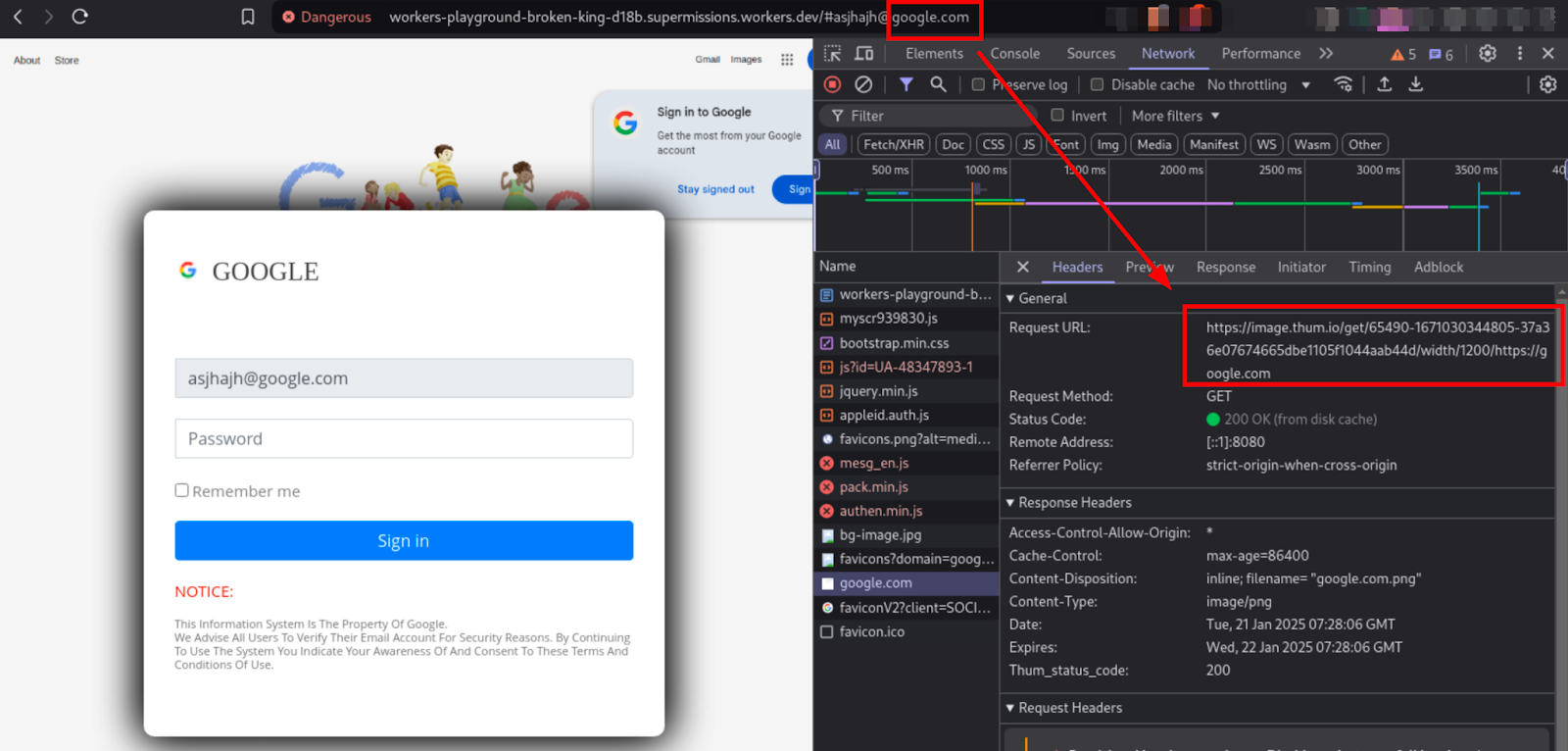
2. In order to turn the generic looking webmail login page into impersonating specific brand scam can use this crafted URL: workers-playground-broken-king-d18b.supermissions.workers.dev/#ahshs@google.com.

3. Phishing attacks can be customized to target specific organizations by adding an employee's email address to the end of a generic phishing page URL, separated by a # symbol.
4. The phishing site takes a screenshot of the domain found in the targeted user's email address (e.g. google.com) using thum.io(a free website screenshot generator) and uses it as the background of the phishing site to deceive unsuspecting users.
5. Once victim enters credentials to login then their credentials are being exfiltrated to a remote endpoint - hxxps://kagn[.]org/zebra/nmili-wabmall.php

6. The phishing page's DOM was obfuscated using JavaScript (filename:myscr939830.js)[Fig5] to evade detection from scam engines. However, the JavaScript was not sophisticated and was easily deobfuscated. Once deobfuscated, the page's functionalities could be verified from the source code.

7. The code snippet prevents users from viewing the page source, which can be used to identify and block phishing attempts - Fig6

8. Below is the functionality in the deobfuscated source code demonstrating how a phishing page is dynamically generated using free services from thum.io and Google’s favicon fetcher endpoint.

1. Based on the similarity of the obfuscated Javascript file, we have identified other phishing URLs employing the same tactics but hosted with Cloudflare's r2.dev: https://pub-3bb44684992b489e903bd3455d3b6513.r2[.]dev/WEBDATAJHNCHJF879476436743YREBHREBNFBJNFHJFEJERUI4894768467RYHGJGFHJGHJ.html

2. During a deeper analysis of the same JavaScript file (myscr939830.js), it was discovered that it is hosted on a free blockchain storage service, web3.storage.
3. The threat actor exfiltrated the stolen credentials to a remote server, kagn[].org. This domain, controlled by the threat actor, was registered 6 years ago and is hosted on Wordpress. The threat actor likely exploited a vulnerability and possibly backdoored the server at /zebra/nmili-wabmall.php.
