🚀 CloudSEK has raised $19M Series B1 Round – Powering the Future of Predictive Cybersecurity
Read more




As India celebrates its 79th Independence Day, the nation faces a highly organized and escalated cyber threat. This threat operates on two distinct fronts: on one hand, fueled by geopolitical tensions following the Pahalgam terror attack, hacktivist groups are openly forming alliances to target critical sectors like government, finance, and technology. On the other hand, opportunistic criminals are preparing widespread phishing campaigns and fake domains to exploit the festive spirit and defraud the general public.
This blog post breaks down the data from recent attacks, reveals the propaganda and recruitment tactics being used by threat actors, details the phishing and fake offer scams to watch out for, and provides clear, actionable steps for every Indian to stay safe online. The analysis covers both the high-volume, disruptive attacks from hacktivist collectives and the more sophisticated, stealthy campaigns from state-sponsored groups like APT36 (Transparent Tribe), Side Copy and APT 41 which continue to target sensitive infrastructure.
Ideological Motivation & The Global Network
The primary driver behind this surge is a potent mix of geopolitical tension and ideological motivation. A significant portion of the activity is explicitly framed as a response to perceived injustices or as retaliation for events like the Pahalgam terror attack and subsequent Indian operations. This is evident in the widespread use of hashtags like #OpIndia on one side and pro-Palestine messaging on the other.
This shared ideology has fueled the formation of a vast, interconnected global network of hacktivist groups. Our intelligence shows groups from Indonesia, Bangladesh, Pakistan, Turkey, and even the United States participating in coordinated campaigns against India.
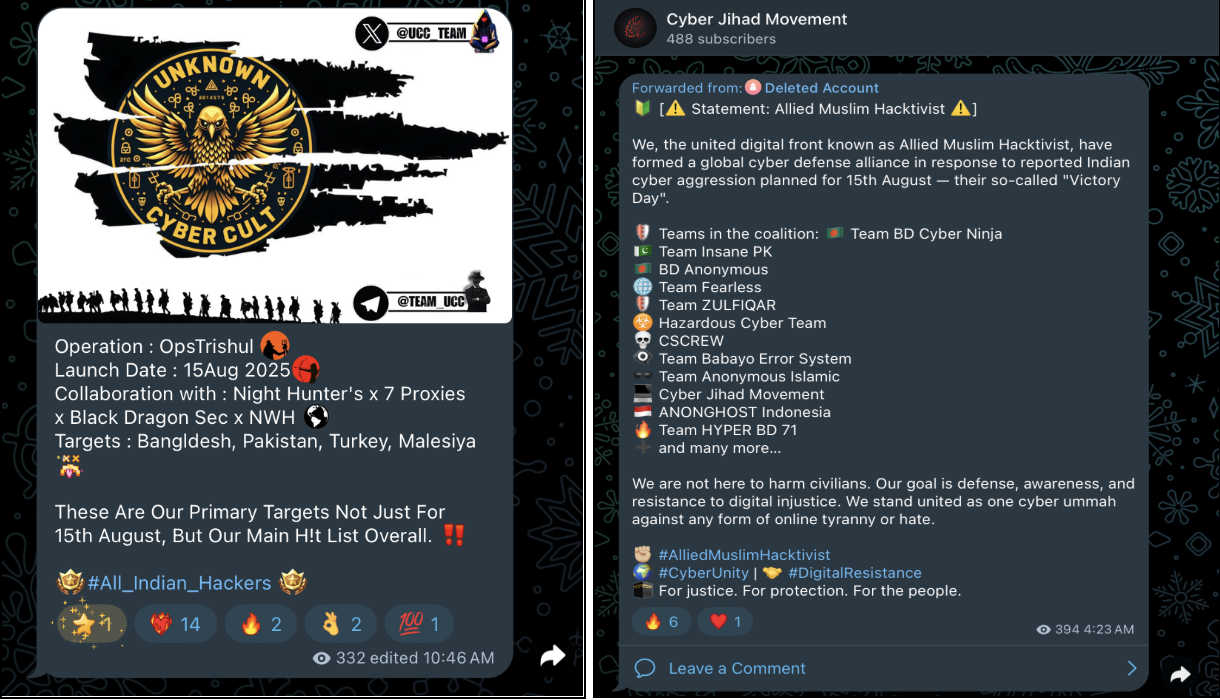
The Inflection Point: The Pahalgam Terror Attack
The current state of hacktivism was mostly observed post Pahalgam terror attack, where the Pro-Indian hacktivist group launched campaigns against Pakistan, while anti-Indian coalitions used the ensuing geopolitical tensions as a justification for their own coordinated assaults.
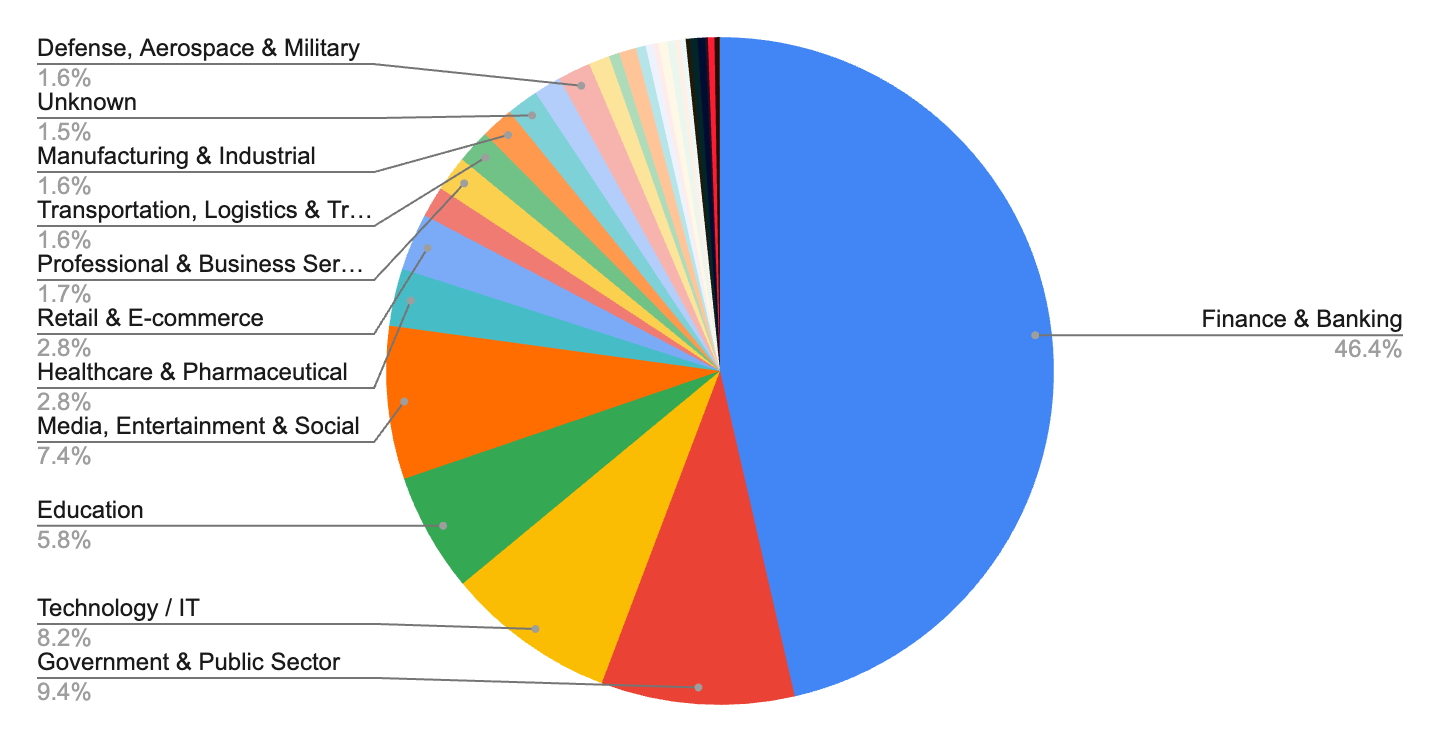
The sectoral split of hacktivist targets reveals a broad and strategic approach to their activism. While sectors like Finance and Banking are the most frequent targets (over 4,000 incidents), highlighting a focus on economic disruption, the presence of government (over 800 incidents), healthcare, education and technology sectors demonstrates a desire to impact critical infrastructure and everyday life.
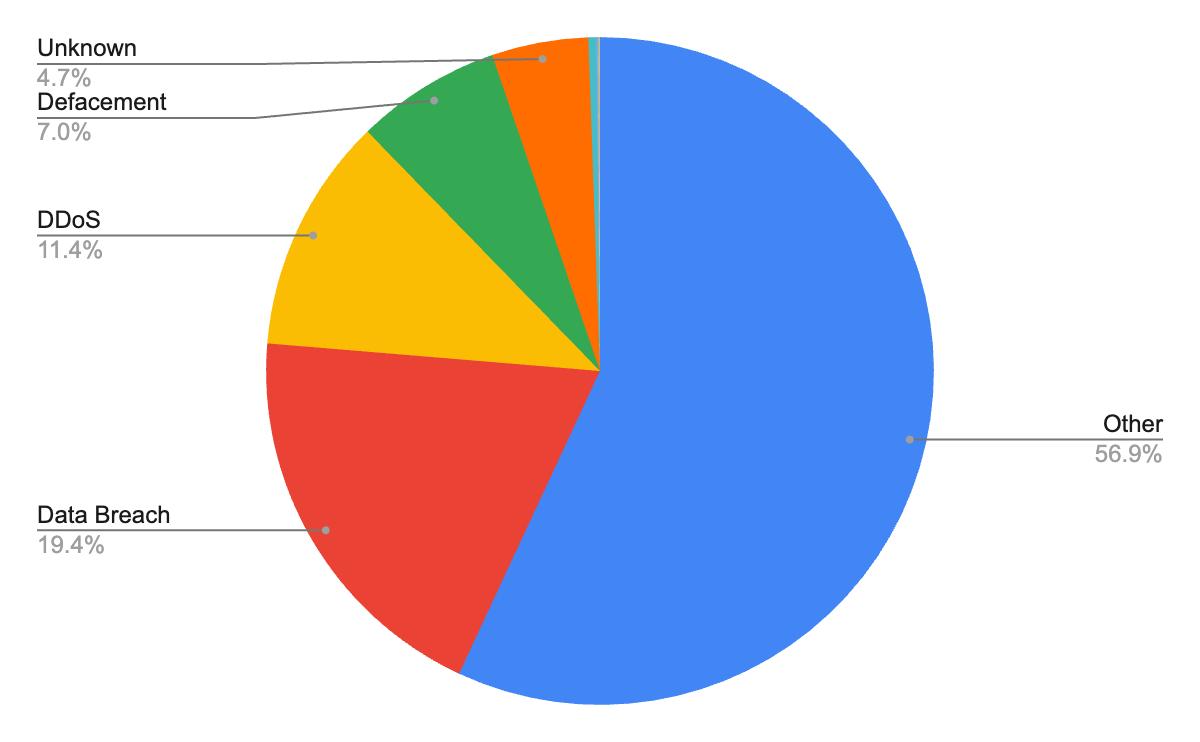
The type of attacks employed by hacktivists in this dataset reveals a focus on disruption and information control.
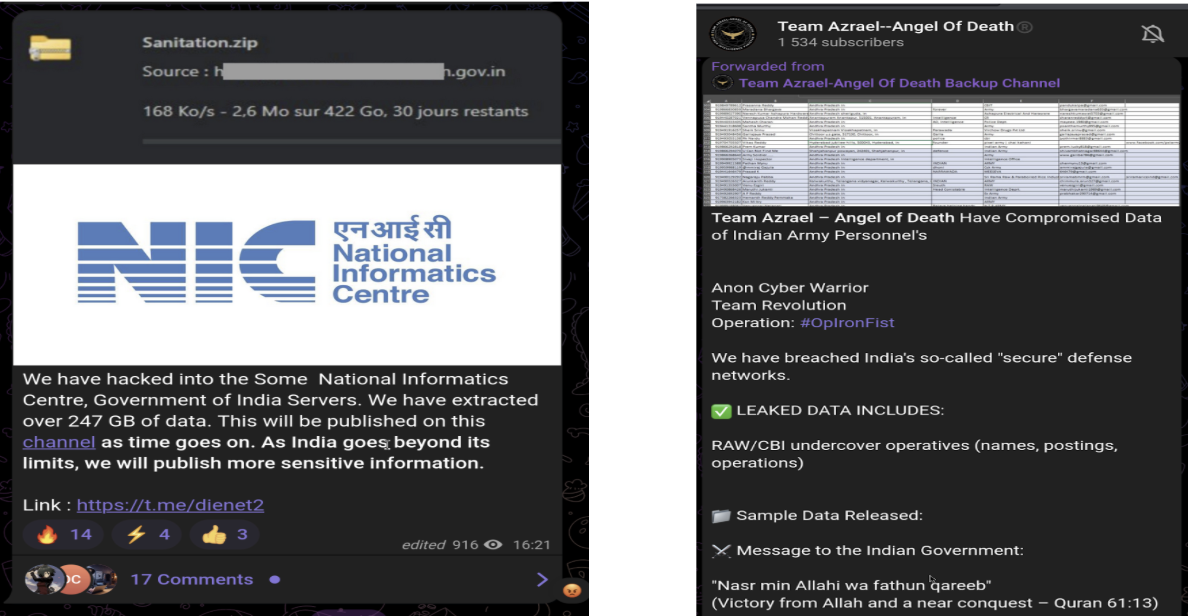
The Threat in Action: Phishing, Scams, and APTs
Phishing and Fake Domains:
We are observing a significant number of malicious websites designed to steal credentials. These sites are sophisticated clones of legitimate portals. Active examples we have identified include impersonation of different government services such as Aadhar Card, National Portal of India and Birth Certificates and Registration sites.
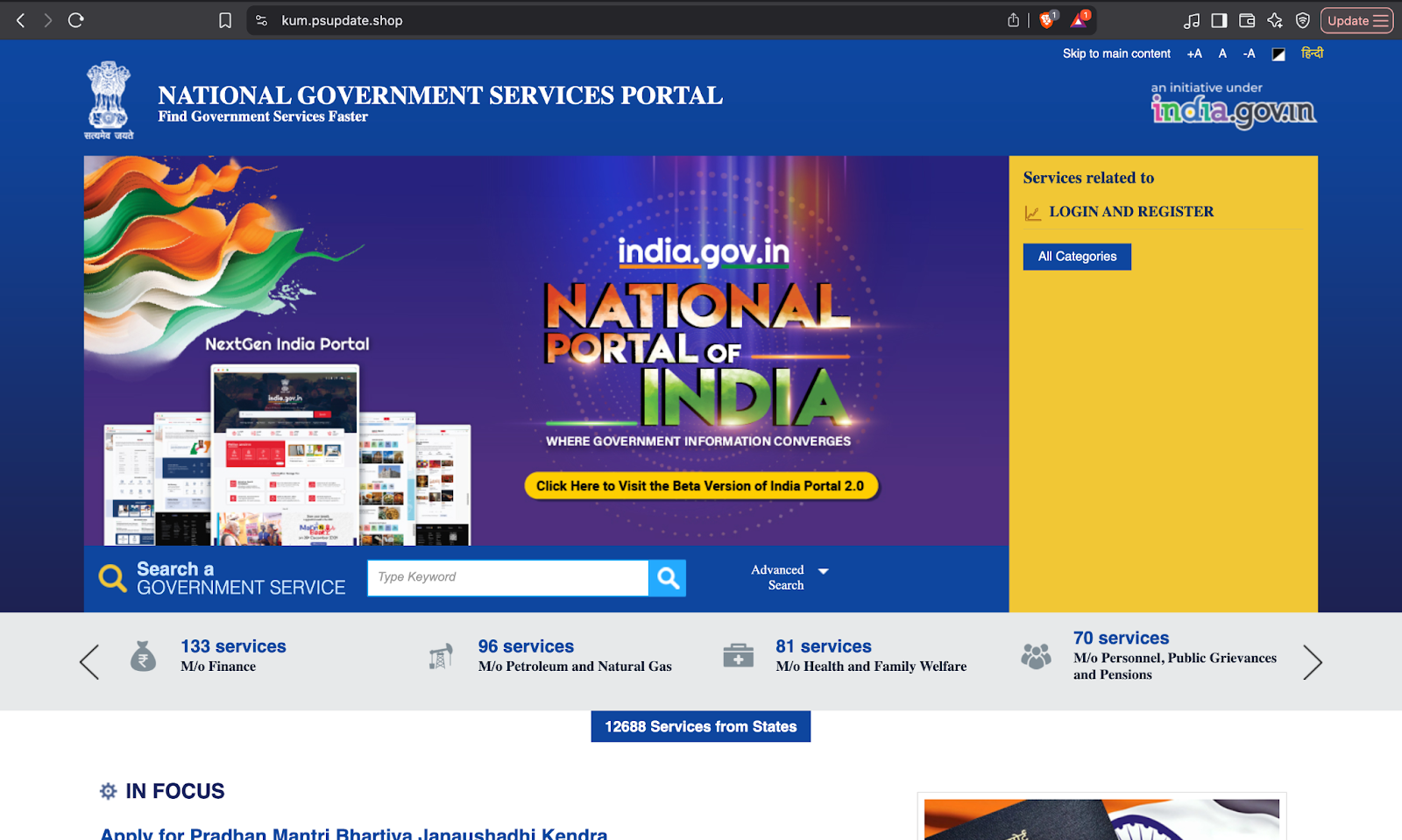
There are also multiple fake phishing domains which are impersonating government email and cloud services which are used to harvest credentials from government employees.
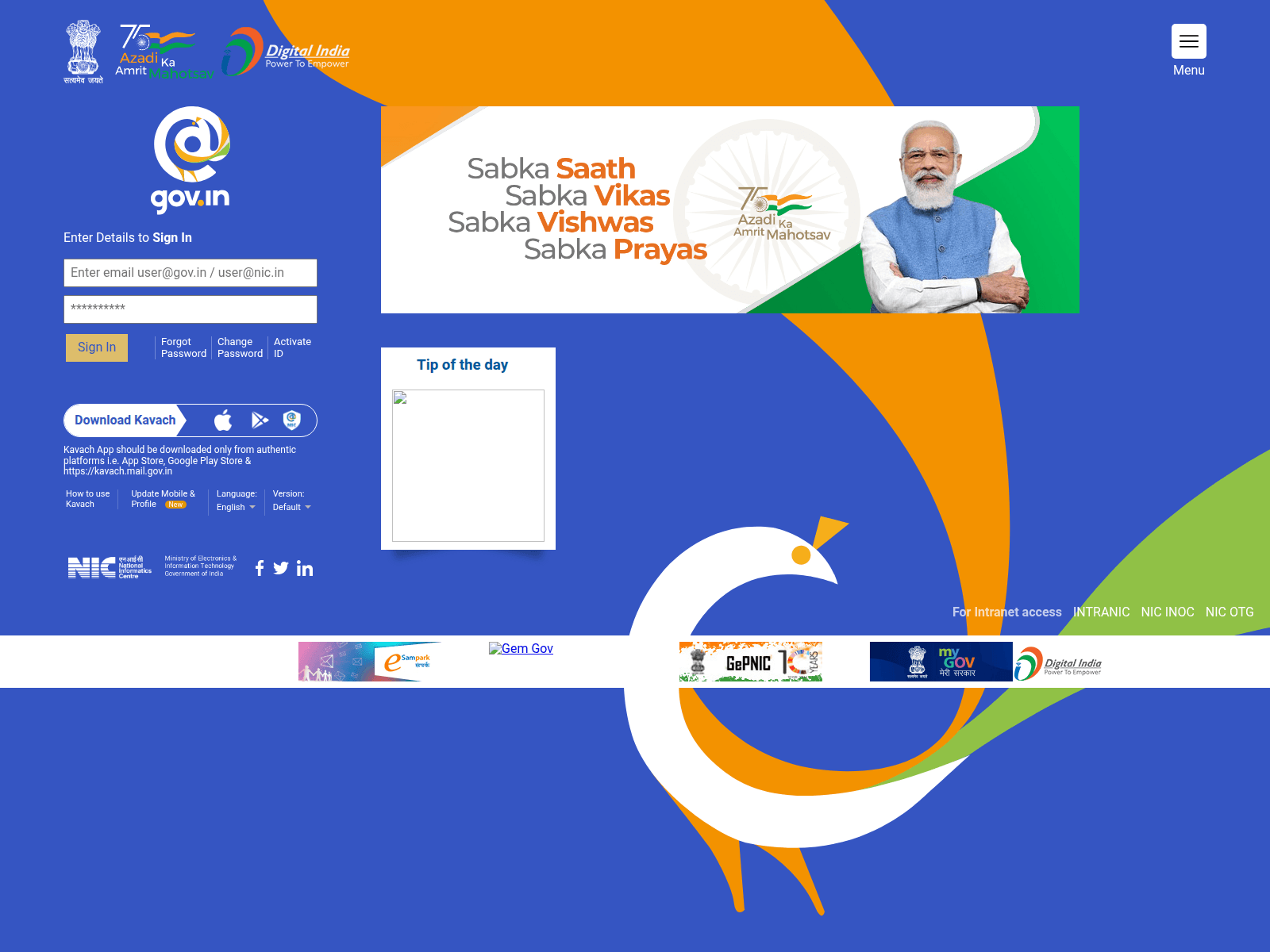
Fake Offers & Festival Scams
While APTs conduct targeted attacks, other criminals use broader tactics. A highly effective tactic that preys on the celebratory mood. Criminals create convincing scams, like those seen during Raksha Bandhan, promising free gifts or massive discounts. Expect to see "Independence Day Special Offers" circulated widely on WhatsApp that lead to data-harvesting websites.
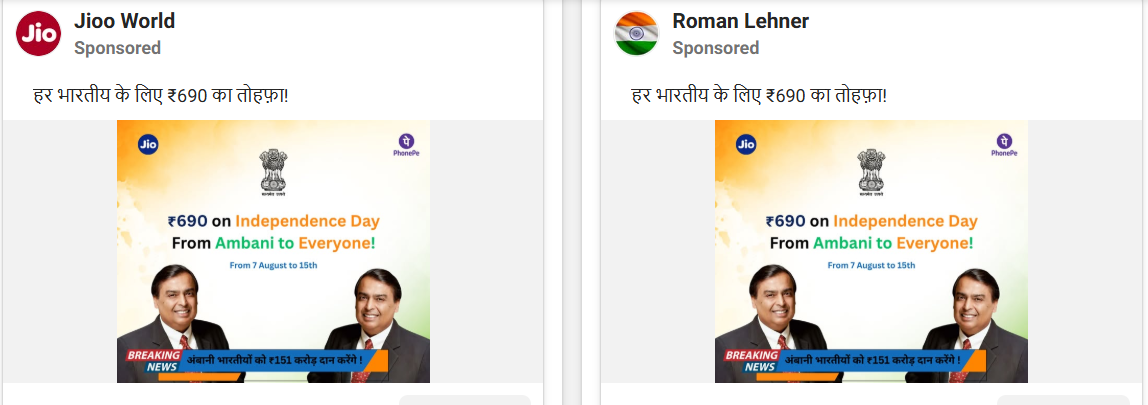
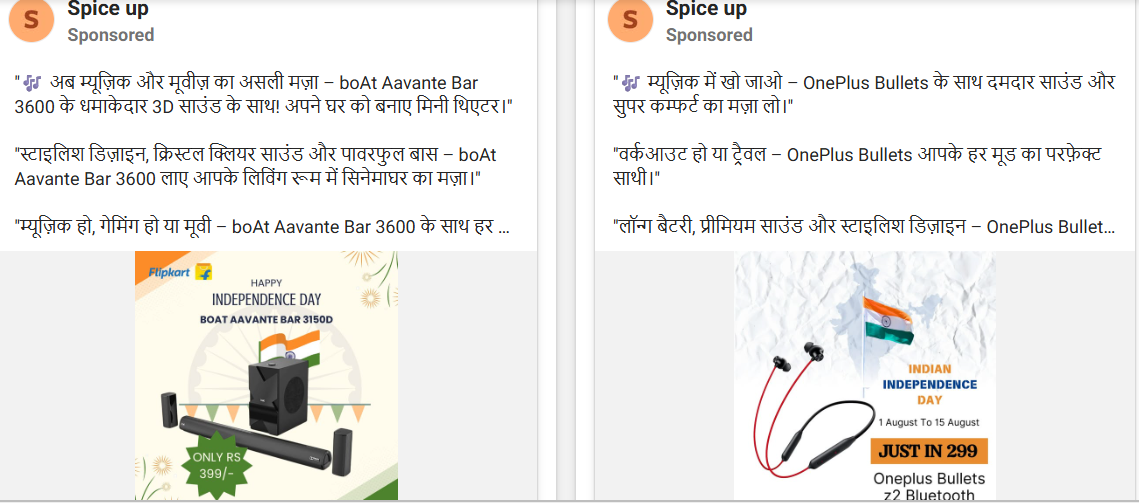
Advanced Persistent Threats (APTs)
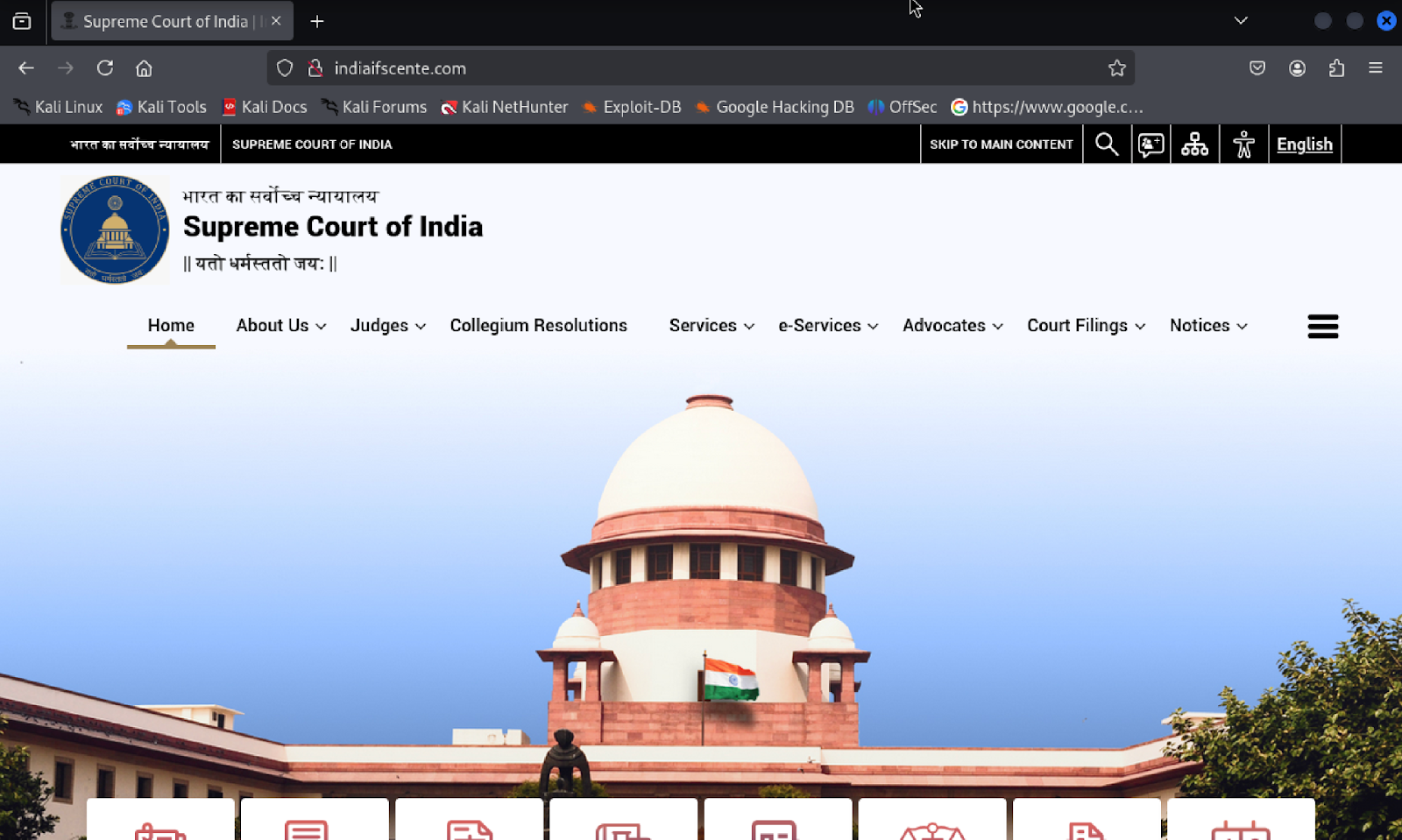
Beyond broad phishing, Pakistan-nexus group APT36 (Transparent Tribe) has been actively targeting Indian government and military websites by registering new domain infrastructure that meticulously impersonates the Indian Army, DRDO, Ministry of Defence (MoD), and government email and cloud services. The main aim of this campaign is credential harvesting, targeted phishing, and long-term intelligence gathering from India's defense and government sectors. Additionally APT36 uses custom malware such as CapraRAT, often delivered via spear‑phishing emails, enabling persistent espionage against high‑value defense and government targets.
Alongside APT36, SideCopy has rapidly evolved its attack infrastructure and tactics to hit Indian critical sectors with spear-phishing, cross-platform RATs, and persistent credential-theft operations. Additionally, China-linked APT41 has expanded targeting to sectors including telecom, manufacturing, technology, and finance in India, leveraging supply chain intrusions, zero‑day exploits, and credential theft campaigns.
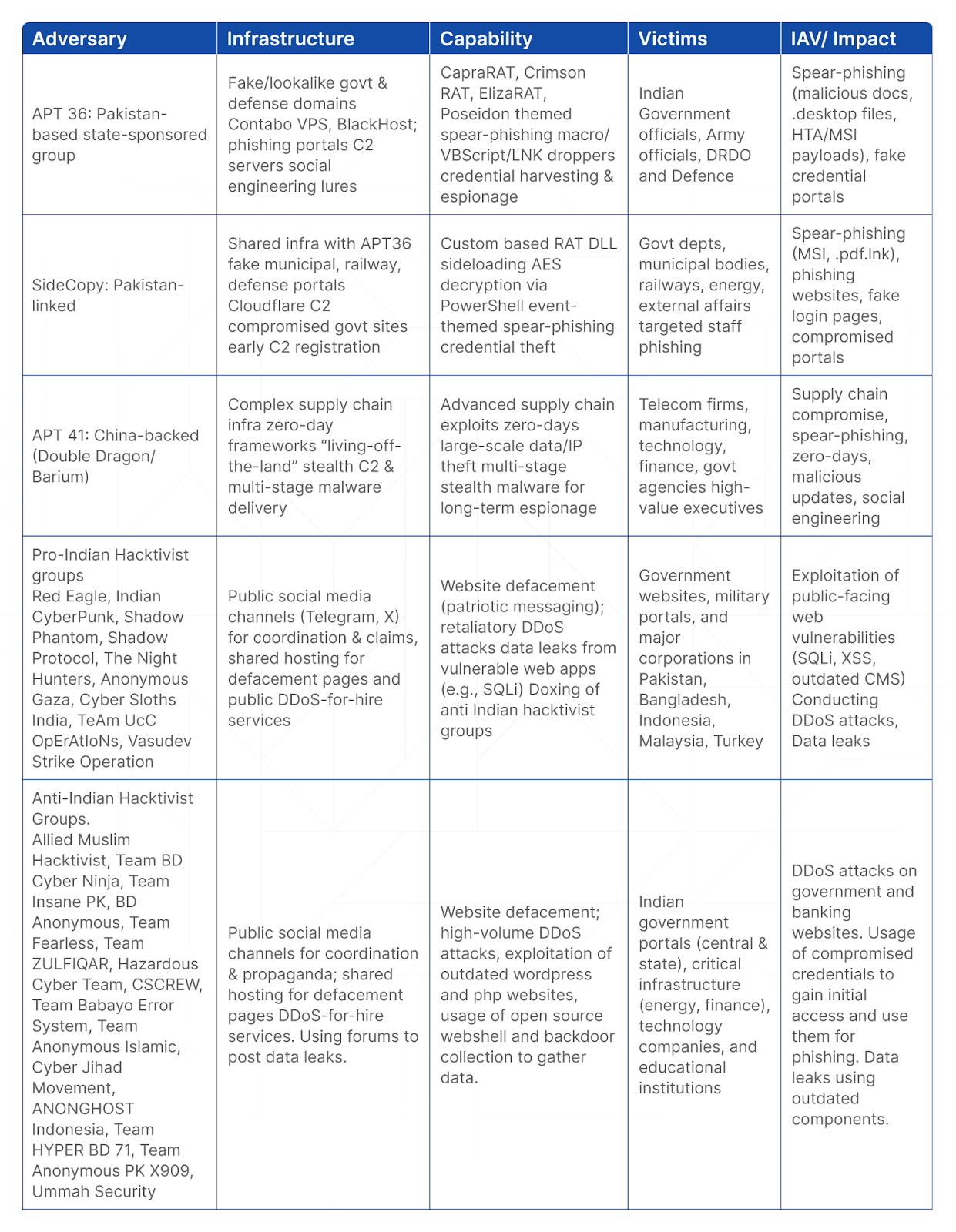
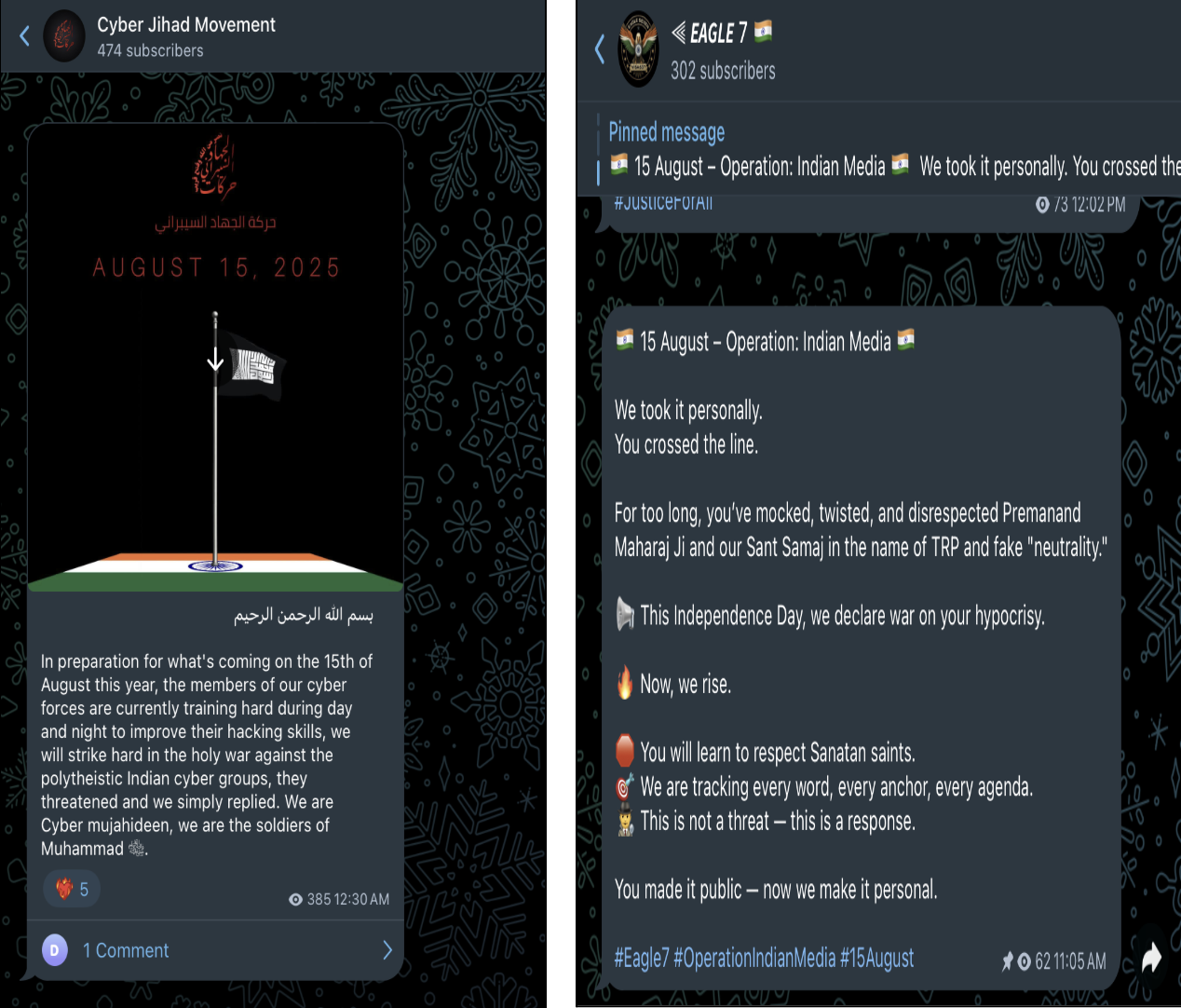
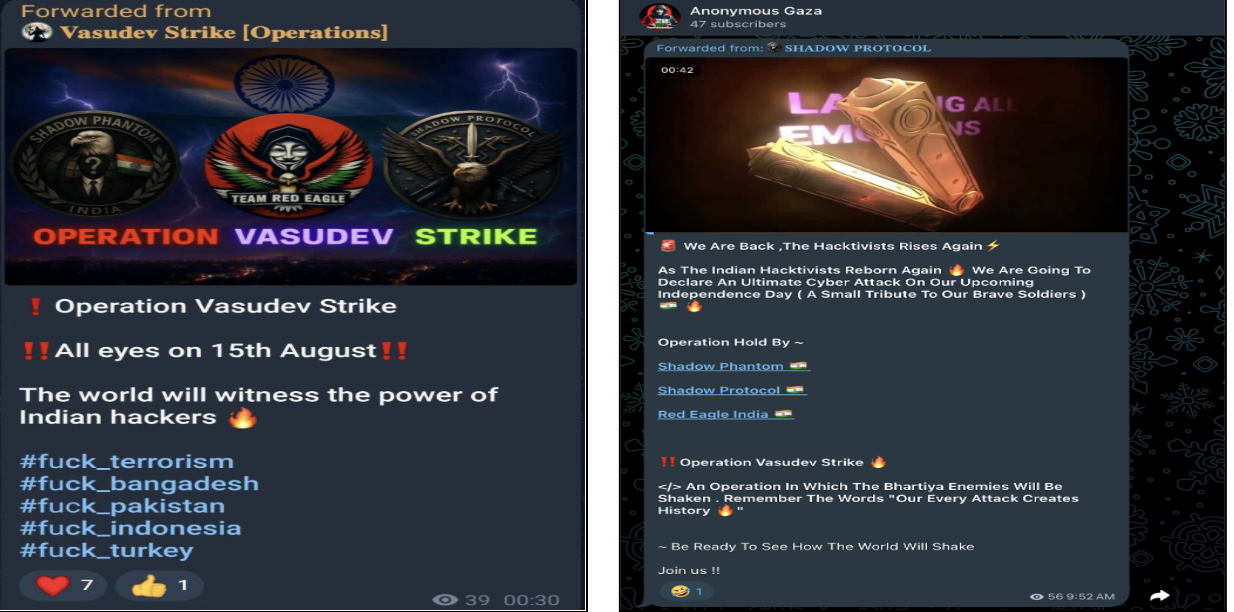
Prior to Independence Day, multiple pro-Indian and anti-Indian hacktivist groups are seen coordinating and launching campaigns. They are using public platforms like Telegram to organize, recruit, and broadcast their intentions.
How to Stay Safe
While the threats are serious, you can significantly improve your security by adopting a vigilant mindset and following these essential steps:
As India celebrates its independence, the nation's digital frontiers require our collective vigilance. The threats are organized, ideologically driven, and growing in intensity, but they often rely on exploiting human trust and technical vulnerabilities. By understanding the tactics of these threat actors, adopting strong cyber hygiene, and maintaining a healthy sense of skepticism, every Indian citizen and organization can play a crucial role in defending our shared digital space.
CloudSEK’s flagship digital risk monitoring platform XVigil contains a module called “Underground Intelligence” which provides information about the latest Adversary, Malware, and Vulnerability Intelligence, gathered from a wide range of sources, across the surface web, deep web, and dark web.
